technology INTEGRATIONS
Code42 Incydr™ Ecosystem
Architected for the integrated and collaborative enterprise

A growing network of partnerships and integrations
The Code42 Incydr Ecosystem is a growing network of strategic partnerships and technology integrations that enable organizations to speed Insider Risk detection and response. Our direct integrations with corporate cloud, email and SaaS applications power Incydr’s risk prioritization and signal capabilities, which can then be used to automate or streamline incident response processes related to insider data risk.
Featured Integration
Okta Identity Cloud + Code42 Incydr
Leverage Okta’s user identity to monitor high-risk users and response quickly to remove access where necessary. Code42 Incydr integrates with Okta Identity Cloud to automate access controls and speed investigations to insider threat incidents
Learn More

Prevent exfiltration activity from potentially compromised users
Manage Watchlists and prioritize risk based on user attributes
Detect and manage files shared from your Box environment
Surface risk to data and accelerate response to insider threats
Contain data risk in response to insider threats
Stop data leaks caused by users with privileged access
Ingest alerts, get actionable insights and triage insider threats
Mitigate data leaks through corporate email accounts
Detect and manage files shared from your Google Drive environment
Automate monitoring and Watchlist management for departing employees
Ingest alerts, get actionable insights and triage insider threats
Mitigate data leaks through corporate email accounts
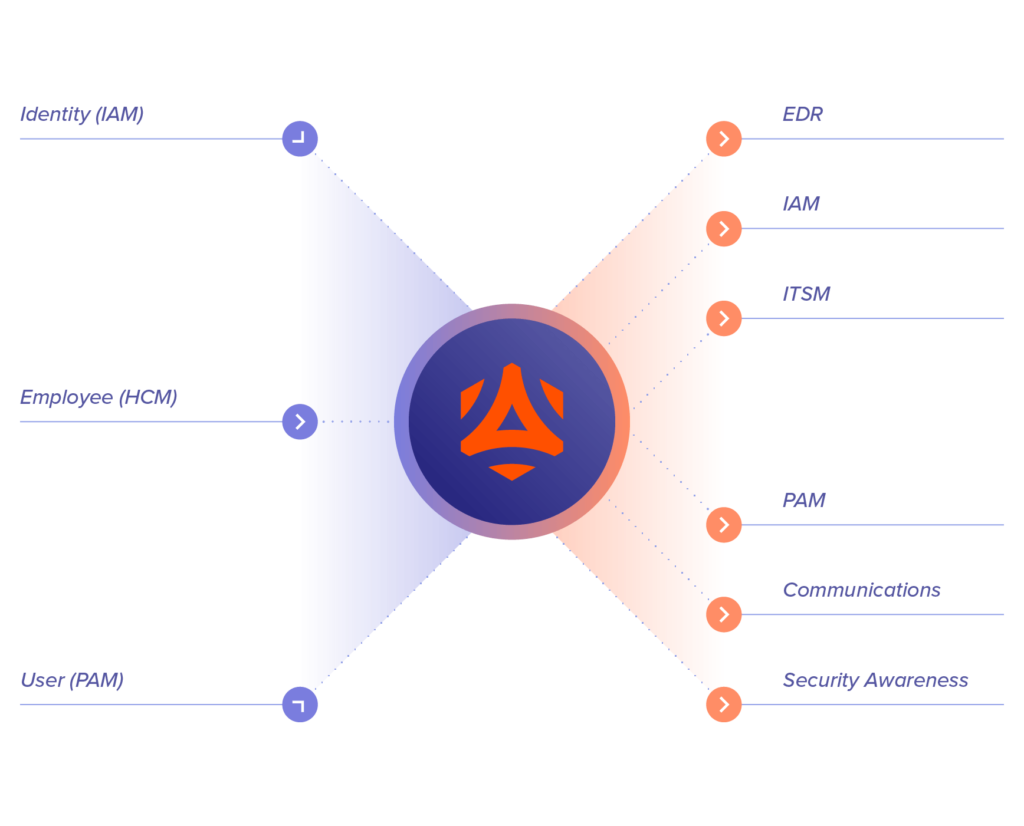
Simplify your integrated workflows with Incydr Flows™
Automate actions between Incydr and other corporate systems like IAM, PAM, EDR, HCM and ITSM in order to save time and increase effectiveness – all with no-code automation. Incydr Flows are incorporated into the Incydr product.
Learn MoreMaximize the value of your existing security tech stack
Code42’s open API allows security teams to create custom reports, perform automated actions or integrate with existing systems within your organization to establish or strengthen your Insider Risk program.
Connect With SalesDeveloper Portal
Develop your own REST-based application leveraging the Code42 API for automation and scripting. Find resources to assist you in the Developer Portal.
Integrate with any SIEM
Correlate and analyze Code42 Insider Risk data in any SIEM via a command-line interface integration.
Streamline Insider Risk workflows
Build custom integrations into HR or other ticketing systems leveraging py42 commands accessible in Github.
Access to security services
We can provide consulting and technical resources to guide you through the integration process and enrich the value of your security stack.
Why customers love Incydr according to Gartner Peer Insights
“This product was exactly as advertised, and we were very happy with it.”
“That employee you like, they’ve taken data.”
Read Full Reviews