GENERATIVE AI
Secure Your Data As Employees Use Generative AI
Protect your company’s data with confidence while embracing Generative AI tools. Code42 Incydr™ stops data from moving to tools and sites that you don’t trust, giving security teams peace of mind.
Connect With Sales
The Problem
86% of security leaders fear employees leak data to GenAI tools, exposing it to competitors
Generative AI platforms, which rely on prompts and data inputs from millions of users, can inadvertently generate and expose sensitive data. The very features that make AI powerful — speed, automation, and learning capabilities — present major threats to data protection:
AI advancements pose challenges for regulations & hamper data protection efforts
GenAI can expose sensitive data by mimicking patterns
Employees using unvetted AI tools can breach protocol and cause data leaks
The Solution
View data movement to Generative AI tools with Incydr
Stay ahead of potential data leaks by monitoring files shared with Generative AI tools. Incydr easily spots risks in corporate file uploads and copy/paste to AI tools with dedicated risk indicators. You can quickly be alerted to these potential data leaks and respond immediately.
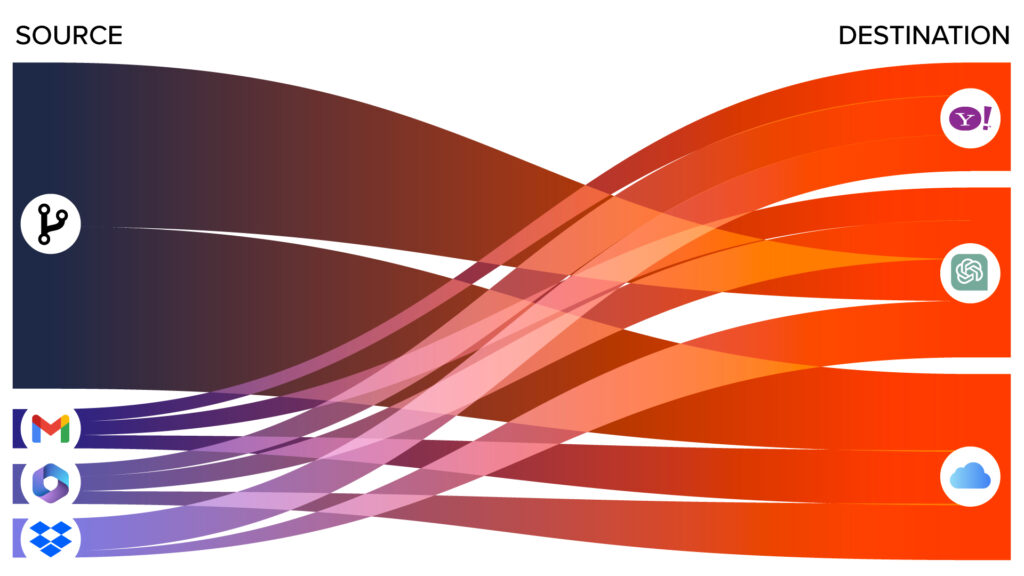
Incydr is built to protect your data from Generative AI tools
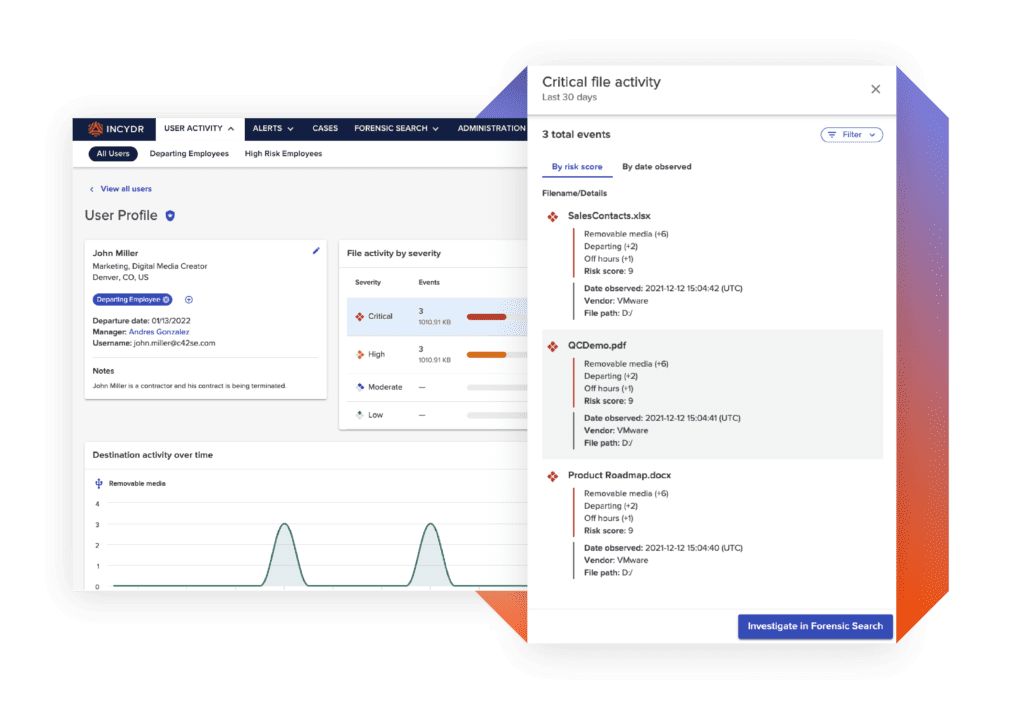
What makes Incydr stand out?
Visibility into cloud and endpoint exfiltration in one, including Git push/pull activity, Salesforce downloads, Airdrops and cloud syncs
Correct users when data is shared incorrectly with integrated security lessons that prevent risky activity from becoming the norm
Validate actual file contents to know for sure how sensitive the data is
Implement real-time blocking for high-risk employees working closely with intellectual property
How Does Incydr Work?Our customers protect their IP from leaving behind their back
Let us show you how they see and stop data leaks with Incydr.
Connect With Sales
Use Cases
Explore other Incydr use cases
Source Code Leaks
Stop proprietary source code from landing in the wrong hands by detecting and preventing source code exfiltrations to untrusted repositories.
Learn MoreDeparting Employees
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
Learn MoreHigh Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn More