reorganizations
Positions Change But Data Should Remain The Same
During company restructuring, data risk increases as employees gain access to new data and others leave the business. With Code42 Incydr™, you can effortlessly secure your data during these changes.

The Problem
During company reorgs, security takes a backseat
Did you know that more than half of cybersecurity experts feel like they don’t have a say in important business decisions? Yet the consequences of insider data incidents can be costly, averaging at $16 million, not to mention the potential damage to company reputation. Data loss during reorgs can occur due to simple oversights or more malicious intentions, like:
The Solution
Get peace of mind your company's valuable data stays where it belongs
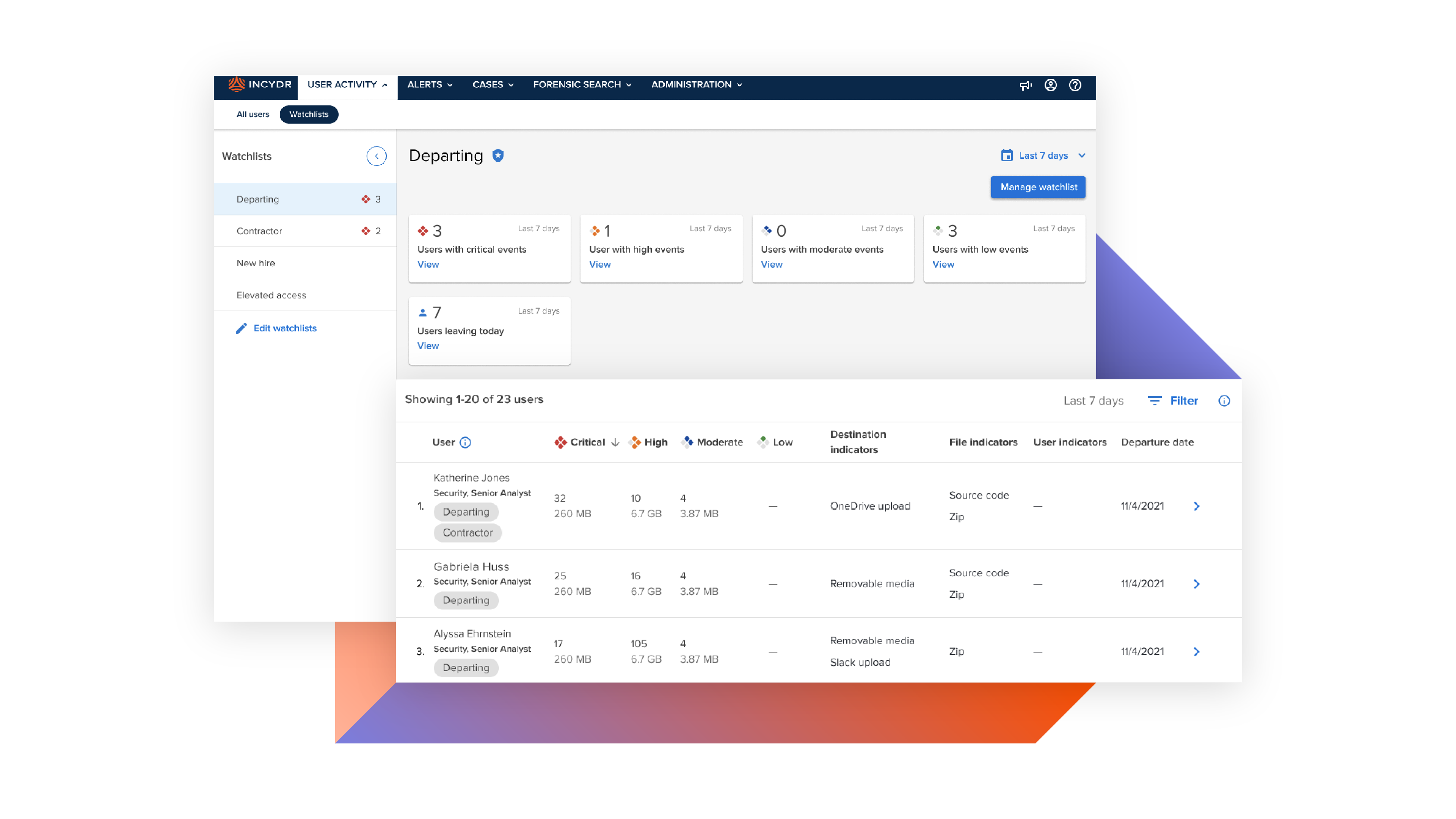
With Code42 Incydr, you have full visibility over your data, including activities like Salesforce downloads, Airdrops, Git pushes, and cloud syncs. Incydr is smart enough to distinguish between harmless actions and potential data leaks, so you can focus on what matters during times of transition. Take control with quick response options to contain threats or block data exfiltration entirely.

Incydr is built to protect data loss during reorganizations
What makes Incydr stand out?
Deploy Incydr in only a few days to quickly provide visibility into data leaks during company reorganization
Integrate directly with HR tools to automatically revoke permissions – without even bothering HR
Validate actual file contents to know for sure how sensitive the data the is
Implement real-time blocking for departing employees
$$$$ just got real. Data leaks from insiders happen daily.
Don't be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before major damage is done.
Connect With Sales90GB
of sales data prevented from moving to an external drive – thanks to Incydr.
High Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn MoreIP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreDeparting Employees
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
Learn More