high risk employees
Identify And Mitigate Your Top Insider Security Risks
Flight risks, privileged users, and individuals with performance concerns pose a greater threat to your data security. With Code42 Incydr™, you can focus data protection measures on these high-risk employees, minimizing your risk of insider data leak and theft.
Connect With Sales
The Problem
Traditional security solutions treat all employee data risk equally
One-size-fits-all data protection methods don’t cut it anymore. Militaristic blocking strategies fail to prevent data leaks as employees when find quick workarounds. Digital change is happening faster than security teams can keep up, which creates visibility gaps that complex policies can’t even address. And let’s face it – a distracted employee who makes a minor file sharing mistake shouldn’t be treated the same as these high-risk employees:
Employees with privileged access
Remote workers
Disgruntled employees
Negligent employees
Contractor workers
The Solution
Tailor your data protection based on the offender and offense
With Code42 Incydr™, you can prevent IP from leaving your organization without the need to classify every piece of data. From day 1, Incydr automatically identifies genuine threats amidst everyday risky events and puts a stop to unacceptable activities by high risk individuals. Preserve your competitive edge and safeguard your brand without resorting to blocking everything.

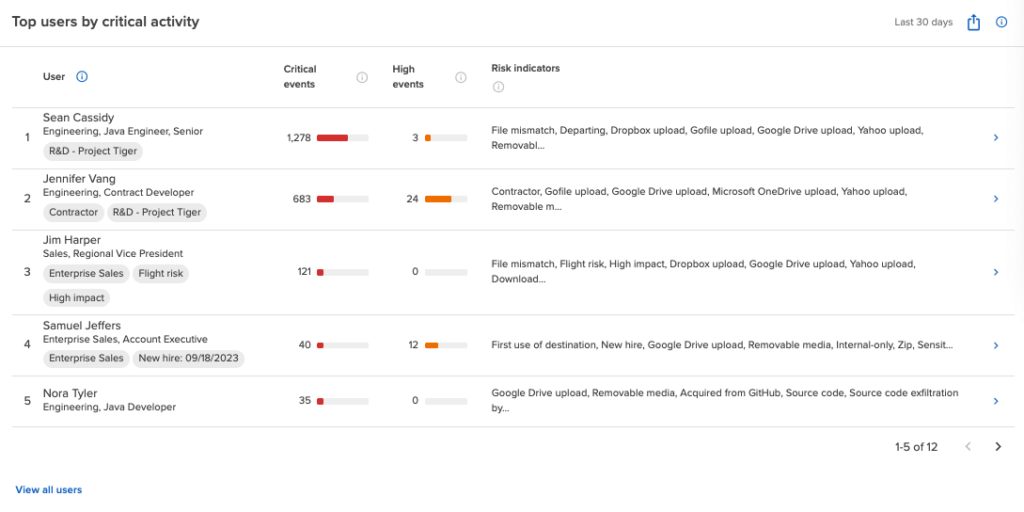
Built to protect high risk employee data leaks
What makes Incydr stand out?
Visibility into cloud and endpoint exfiltration in one solution including Git push/pull activity, Salesforce downloads, Airdrops and cloud syncs
Add high risk users to a Watchlist for enhanced data activity monitoring
Implement real-time blocking for employees working closely with intellectual property
Correct users when data is shared incorrectly using Instructor lessons that prevent risky activity from becoming the norm
Can you put a price tag on your company’s IP?
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before damage is done.
Connect With Sales$9M
worth of deleted files that helped disprove lawsuit accusations – thanks to Incydr.
Contractors
As temporary members of the organization, contractors present a heightened risk for data theft. Monitor files access and flag unusual or unauthorized activity.
Learn MoreIP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreDeparting Employees
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
Learn More