Data Loss Prevention
Outdated DLP?
No More.
Say goodbye to outdated and cumbersome data loss prevention. Even with a DLP in place, the majority of companies still experience a data breach. That’s why Code42 offers a different approach to tackling this problem.
Connect With Sales
Today’s Problem
Legacy DLP is a resource-heavy approach
Don’t let rigid policies and blocking-first controls hinder your data loss prevention efforts. Traditional DLPs are a hassle to implement, customize, and manage, only detecting what you specifically instruct them to. They struggle to detect real threats amidst the digital collaboration noise and lead to disruptions in employee productivity.
Code42’s Solution
Easy to manage DLP with no user impact
Protect your data with Code42 Incydr™. Detect and prevent unauthorized data movement across endpoints and cloud apps – without the need for complex policies. Save time for your team with automated responses and easy integrations. Incydr is lightweight and easy to implement, so it won’t impact user productivity or require multiple protection tools.
No more guesswork, just quick detection
Stop wasting time on lengthy policy writing that doesn’t work. From the moment Incydr is deployed, it automatically monitors your cloud and endpoint exfiltrations, swiftly pinpointing data leaks and theft – that includes Salesforce downloads, source code movement, Airdrops, ChatGPT, cloud syncs & more. Cut through the noise of trusted activity and focus on protecting your most sensitive data.
Is Your Data Leaking Via ChatGPT?

Response actions for every incident
Unlike old-school DLP solutions that stick to rigid, block-first playbooks, Incydr’s response controls adapt to the severity of each data incident. Whether it’s a simple mistake or a serious threat, Incydr allows you to respond with pinpoint accuracy. Correct user mistakes, investigate potential breaches, and block malicious activity from risky users.
What Is Incydr's Response Strategy?Boost productivity without compromises
Incydr doesn’t just amp up your security game – it’s a productivity booster too. While clunky traditional DLPs slow processes down, Incydr is lightweight and integrates seamlessly into your systems, including messaging, HCM, ITSM, and more. Incydr provides automated security education to improve employee behavior and create a workforce of security allies. Your company can operate at peak efficiency without compromising on security.
Code42's Integrated Security Education
Technology INTEGRATIONS
Incydr is easy to implement with your existing tech stack
90% of companies use a combination of DLP, CASB, UEBA, or IRM to stop data exfiltration. Consolidate your data protection tools with Code42 Incydr and integrate seamlessly with your existing tech.
Want to see Incydr from the inside?
In under four minutes, our product demo shows how Incydr can see and stop data leaks – before major damage is done.
Watch Demo Now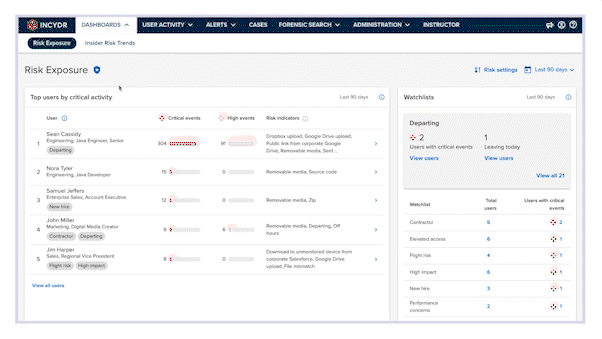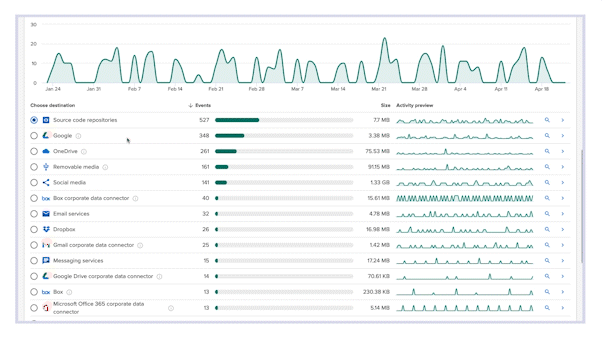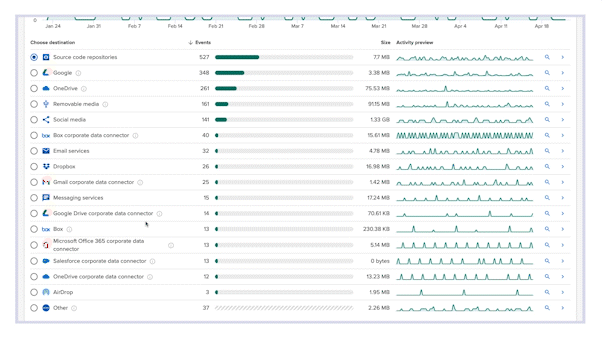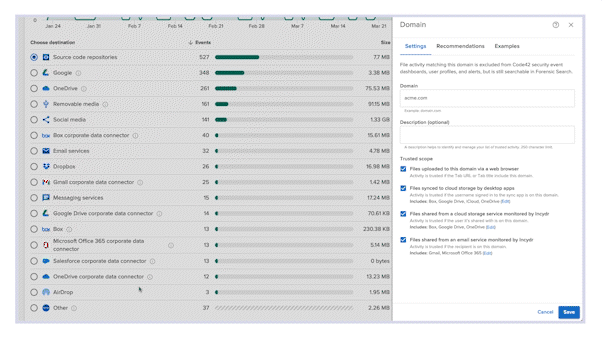
IP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreSource Code Detection
Stop proprietary source code from landing in the wrong hands by detecting and preventing source code exfiltrations to untrusted repositories.
Learn MoreMergers & Acquisitions
Sensitive data leaks during highly regulated transitions like M&A can be particularly disastrous. Mitigate data loss during company transitions with proactive risk monitoring.
Learn More