Layoffs
Keep Company Data Secure During Turbulent Times
Don’t let valuable data leave your organization during layoffs. With Code42 Incydr™, you can detect and prevent data theft by employees before they even walk out the door.
Connect With Sales
The Problem
Company layoffs increase risk of data theft
Layoffs not only trigger job searching and decreased loyalty, but also make disgruntled employees more prone to committing data theft. The organizational changes during layoffs also introduce security gaps, privileged access abuse, and logistical oversights that can result in unnoticed data exfiltration.
The Solution
Detect data theft before terminated employees walk out the door
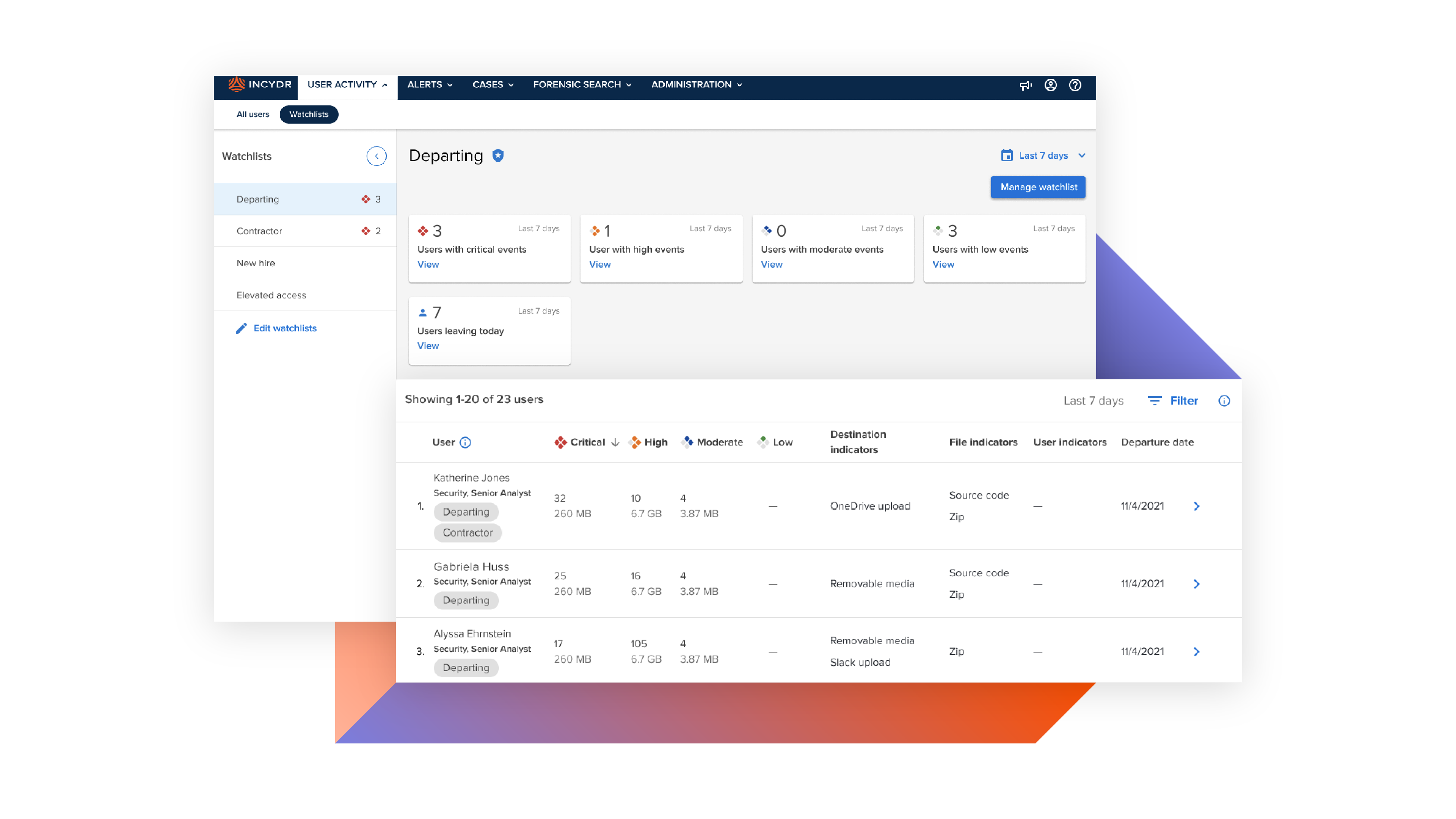
With Code42 Incydr, you gain complete visibility over data movements by terminated employees. From the very beginning, it intelligently distinguishes low-risk activities from potential security breaches. Armed with a wide range of response controls, you have the power to swiftly contain threats or even block data exfiltration altogether.

Built to protect data from leaving during layoffs
What makes Incydr stand out?
Monitor cloud and endpoint exfiltration in one solution including Salesforce downloads, Git pushes, Airdrops and cloud syncs, & more
Add terminated employees to a Watchlist for enhanced data activity monitoring
Validate actual file contents to know for sure how sensitive the data the is
Stop unacceptable data exfiltrations by terminated employees with real-time blocking capabilities
Can you put a price tag on your company’s IP?
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before major damage is done.
Connect With Sales$9M
worth of deleted files helped disprove lawsuit accusations – thanks to Incydr.
High Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn MoreIP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreReorganizations
The logistical challenges of reorganizations can lead to security gaps that increase the risk of data exfiltration going undetected.
Learn More