Use Cases
Identify And Respond To Common Insider Threat Incidents
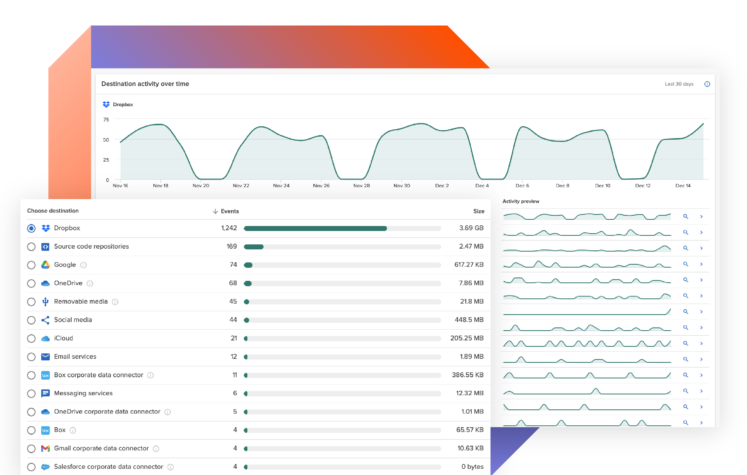
Explore primary use cases for Incydr™
Fueled by fast-paced, cloud-powered collaboration cultures, Insider Risks continue to increase across organizations today. Here are some of the most common types and how Incydr can help protect against them:
Departing Employees
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
Learn MoreIP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreSource Code Leaks
Stop proprietary source code from landing in the wrong hands by detecting and preventing source code exfiltrations to untrusted repositories.
Learn MoreRemote Workforce
Remote workers introduce new security challenges. We help you manage the risk of off-network activity when employees work from home.
Learn MoreLayoffs
Layoffs can cause disgruntled employees to commit data theft. Get peace of mind that company data is protected during turbulent times.
Learn MoreGenerative AI
Stay ahead of potential data leaks by monitoring files and content shared via Generative AI tools.
Learn MoreContractors
As temporary members of the organization, contractors present a heightened risk for data theft. Monitor files access and flag unusual or unauthorized activity.
Learn MoreShadow IT
63% of employees use the tech they want to get their jobs done. Stop your data from moving to unsanctioned applications.
Learn MoreHigh Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn MoreRepeat Offenders
Behind every data risk event is an employee who likely didn’t follow the rules. Stop data exfiltrations from users who continue to violate security policies.
Learn MoreMac Environments
When it comes to your Mac users, what data exfiltration aren’t you seeing? Get the data visibility you are missing – across Windows, Linux and Mac endpoints.
Learn MoreReorganizations
The logistical challenges of reorganizations can lead to security gaps that increase the risk of data exfiltration going undetected.
Learn MoreMergers & Acquisitions
Sensitive data leaks during M&A can be particularly disastrous. Mitigate data loss during transition with proactive risk monitoring.
Learn MoreSecurity Awareness Training
Improve security awareness within the organization to reduce Insider Risk incidents and encourage employees to report suspicious activity.
Learn MoreCan you put a price tag on your company’s IP?
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before major damage is done.
Connect With Sales$9M