Code42 Incydr™ For Business Services
Data security from insider threats for consulting, accounting, legal and creative firms
Today’s Problem
Traditional data protection software doesn’t work for relationship-driven businesses
Data security products that utilize classification and rigid rules to identify sensitive data, trigger alerts and block file activities stand in the way of working with your customers and their applications. And these systems are only as good as the rules you write:
- Make rules too sensitive and you trigger false positive alerts that block legitimate work
- Make rules too specific and high-value data slips past your defenses
The constant fine-tuning drains security time and money while damaging employee productivity. But how do you protect your work and your customers’ data without something standing between the way employees work today?
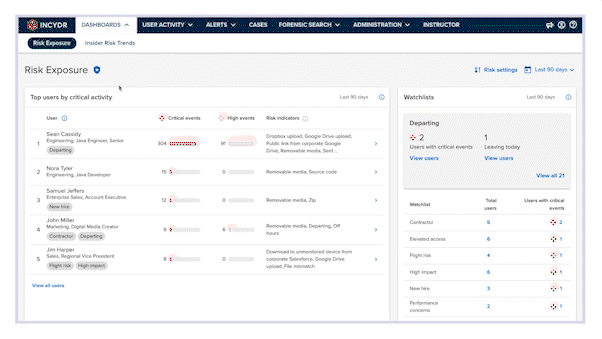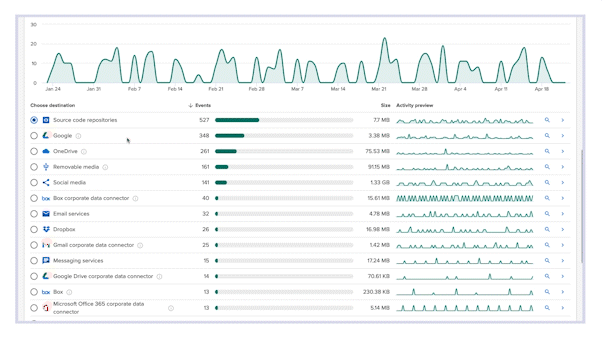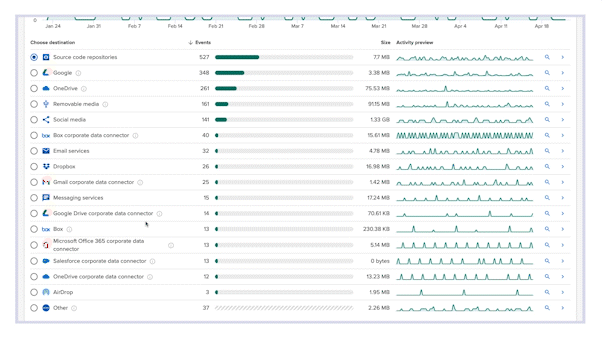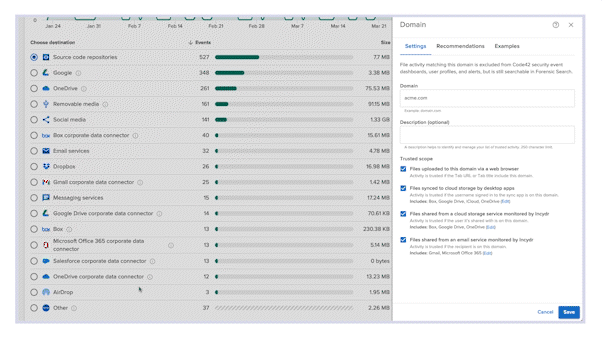
How Incydr Works
3 ways Incydr protects data in risk situations
Slack and external channels
While engaging with your clients, chances are, your operational teams are joining external slack channels. But that shouldn’t impede your ability to monitor sensitive data, whether it’s yours or your customers’.
Salesforce.com downloads
Downloaded customer data and pipeline forecasts from Salesforce are shared across the workforce everyday – but it shouldn’t be shared outside of your organization. Salesforce downloads can contain PII, and one accidental email or public link could mean a breach.
Sharing data the way your customers prefer
One client might use Google products, another might be a Microsoft shop. Either way, cloud collaboration documents are flying around your organization, and it only takes one misguided click to make them public and accessible by anyone from any device.
Why Incydr works for business service firms

No barriers
Instead of putting up barriers, Incydr ensures your employees and contractors don’t send valuable data to people and places you don’t trust. We show you where and how data is leaving, what activities need review, and how to respond to different types of risk.
Visibility to where data actually lives
From computers, to corporate cloud apps (like O365, Google Drive, and Salesforce), to browser uploads, Incydr monitors the places your data lives and moves, and identifies untrusted activity without regex policies or proxies. And it works for your whole environment: Mac, Windows, and Linux.
Signals of real risk
Incydr monitors data with an emphasis on signal — weeding out the noise, highlighting critical activity, and giving you the context you need to act with certainty.

Hear what our business services customers have to say
“With Incydr, the security team can now see all file activity and prioritize those events without missing what might slip by a policy-based solution. That context helps them quickly identify the truly risky insider actions and determine the right-sized response.”
Senior Analyst at a Media Production Company
Want to see Incydr from the inside?
In under four minutes, our product demo shows how Incydr can see and stop data leaks – before major damage is done.
Watch Demo Now