Overview
See & Stop Data Loss With Incydr™
Code42 Incydr helps you quickly see and stop data leak and theft in one platform, eliminating the need for DLP, CASB, and UEBA in most organizations.
Secure collaboration without burdening your security team
With Incydr as your data protection solution, you will detect data theft on day 1 and tailor responses based on the offender and the offense. It’s not too good to be true – all of this can be done without slowing users down or creating extra work for security.
Visibility when critical IP leaves your organization
Do you know which files contain your company’s intellectual property? Truth is, there are millions of files and thousands of places they can go. Incydr has full cloud and endpoint visibility to detect data leak and theft across browsers, USB, cloud apps, Salesforce, email, Airdrop, Git push/pull and more.
Pair that with contextual prioritization, and you’ve got a solid way to protect IP. Identify when files move outside your trusted environment (including personal accounts or unmanaged devices!). All of this is out-of-the-box to detect threats on day 1.
How Incydr Prioritizes Data Risk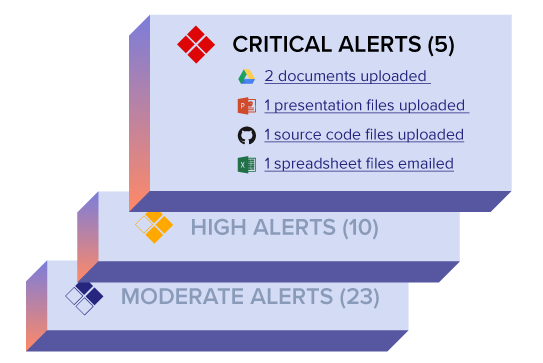
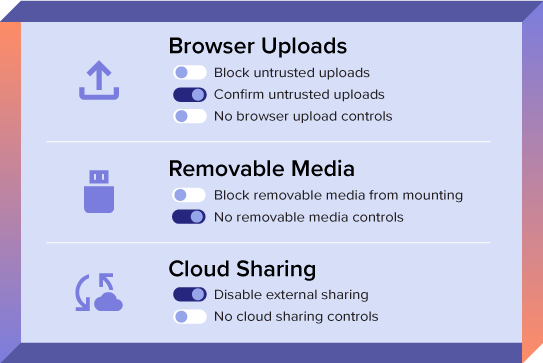
Contain data leaks without disrupting employees
Security teams often take a block-first approach to response. The problem is, that forces users to find workarounds to policies and creates more risk (and work) for security.
With Incydr, you can tailor your response strategy to the offender and the offense and respond appropriately to every type of event – from mistake to threat. This is crucial to correct user mistakes, document and investigate true threats, and block unacceptable activity from high-risk individuals.
View Full Range of Response ControlsLess work for you and less complaints from users
Traditional data protection solutions cause internal battles – but not Incydr. It seamlessly integrates with cross-functional systems such as messaging, HCM and ITMS systems, and has a lightweight agent that doesn’t slow down devices.
It has built-in security training that is a win-win – employees complain less about security getting in the way of work, and security can focus their time on bigger data risks.
Plus, we provide a success map so you can avoid concerns around employee privacy or stakeholder roles.
How Code42 Supports Program Set-Up
Customer StorY
How Incydr became an integral part of Snowflake’s security stack
“Without hesitation, Incydr, and how it fits into our overall strategy, is central to our security program. Using Incydr, we see particular patterns and behaviors that suggest a potential insider moving data to untrusted systems.” – Mario Duarte, VP of Security
Read Case StudyCan you put a price tag on your company’s IP?
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before major damage is done.
Connect With Sales$9M