Table of Contents
Data exfiltration refers to the unauthorized transfer of sensitive information, such as personal data, financial records, or intellectual property, from a computer or network. This can occur through accidental leakage by employees or through malicious insiders who intentionally leak data to unsafe locations. Alarmingly, since 2021, there has been a 28% increase in the average number of monthly insider-driven data exposure, loss, leak, and theft events.
The changing nature of work, including the rise of collaboration tools, a volatile workforce, and increased innovation with AI, has put companies at greater risk of data exfiltration. As AI tools become more integrated into the workplace, new data exfiltration threats emerge when employees copy and paste sensitive information into unfamiliar platforms. Additionally, outdated security practices have led to resentment among employees, prompting them to find workarounds to maintain uninterrupted workflows, further increasing the risk.
In this article, we will define data exfiltration, share real-world examples, and explain how to detect and prevent it effectively.
Data exfiltration defined
Data exfiltration is the unauthorized removal or movement of any data from a device or network. Also known as data exportation, data leakage, or data extrusion, data exfiltration can lead to data loss and cause immense damage to an organization’s reputation and revenue.
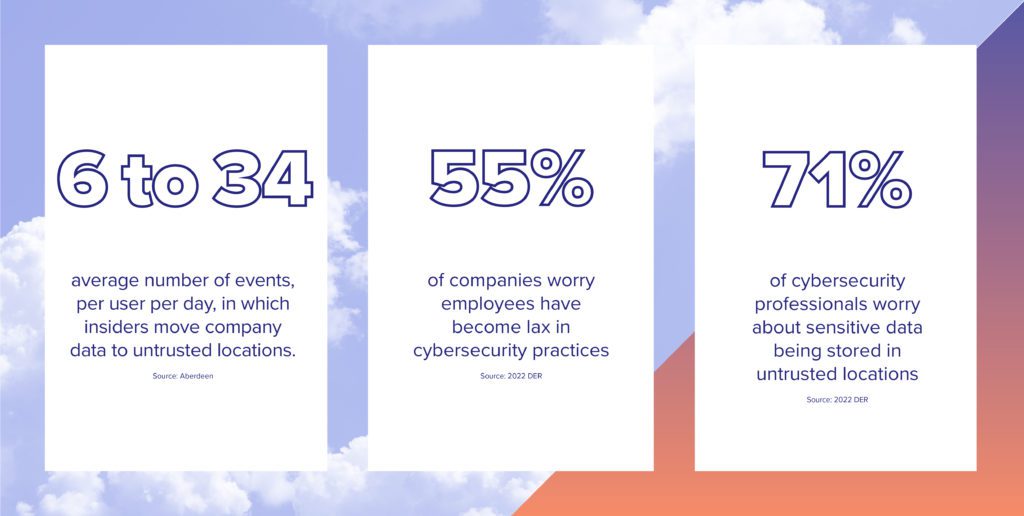
The same cloud-based technologies and hybrid or remote work models that help companies thrive also put them at risk of data exfiltration via insider threats in particular. One recent report found that over the span of five business quarters, the number of events in which insiders move company files to untrusted locations via methods like email, chats, cloud, etc., averages anywhere from six to 34 times per user, per day.
2024 Data Exposure Report
85% of security leaders are worried their sensitive data is vulnerable to AI technologies

How does data exfiltration occur?
Given the significant repercussions data exfiltration can have on an organization (one insider data incident costs a business $15 million, on average), it’s important to be able to understand all of the different ways in which it can occur. You can break data exfiltration into two categories: external attacks and insider threats.
External attacks happen when a cybercriminal penetrates an organization’s network and data. Often, external attacks occur via malware or phishing. Sometimes malware can do its damage quickly after being introduced into a system, using attack vectors (like phishing) or payloads (like worms) to do things such as steal info or create botnets.
Insider threats, on the other hand, stem from employees, contractors, third parties, or others with legitimate system access. Insider risk occurs when any data exposure — regardless of type of data or user intent — jeopardizes the well-being of an organization and its employees, customers, or partners. The intent of these insider threats can be accidental or negligent: synching work documents with a personal iCloud account; using unapproved tools to get their job done; or simply sharing cloud files with the wrong folks or making them public.
A larger portion of data exfiltration from insider threats are actually malicious, and malicious actors often cause breaches: spying for foreign nationals, changing file names and extensions to obfuscate the value of data being moved, or taking data to get a leg up on a new role.
Security infrastructure is generally set up to handle adversarial threats, especially those that originate from external actors. Given both the workflows at many businesses and human nature, some causes of insider breaches are more common than others. Although the list below is not exhaustive, it includes types of data exfiltration that organizations are most likely to encounter.
Types of data exfiltration
In today’s digital landscape, data exfiltration poses threats to source code, valuable IP, and customer information. For security professionals, understanding the various methods by which sensitive information can be illicitly transferred out of a network is crucial to building robust defense mechanisms.
From human error and non-secure cloud app behavior to deceptive strategies like phishing and social engineering, the avenues for data exfiltration are numerous and varied. Even seemingly benign activities, such as sending a simple email, can serve as unwitting conduits for data leaks. Our goal is to arm you with the knowledge to identify and mitigate these threats effectively.
Human error and non-secure cloud app behavior
While cloud technology and tools have enabled new ways of working, they’ve also intensified the scale and impact of data exfiltration. To that end, 71% of cybersecurity professionals surveyed in the 2022 report mentioned earlier are worried about sensitive data saved on local machines/personal hard drives and/or personal cloud storage and services.
Some of the most common behaviors that center around cloud apps in particular include:
- Using untrusted personal devices to log into corporate cloud apps
- Making private cloud links publicly available
- Downloading corporate data via cloud app to a home device
- Using unsanctioned clouds (usually personal clouds) to share data with 3rd parties and colleagues
Every time an authorized user performs one of these actions, they put your data at risk.
A significant amount of data exfiltration is also caused by human error. Employees inadvertently expose data when they do things like accidentally connect an iPhone to a corporate device or share a private link to a public Slack channel. Although employees may not do these things on purpose, the resulting data exposure can be impactful. Thankfully, situational and timely security training can help prevent these occurrences.
Emails
When 319 billion emails are sent each day, it’s no surprise that some of them might be involved in data exfiltration. Many employees end up using their personal email or personal file hosting services to send or store confidential work documents. This movement can be out of convenience or it might stem from more nefarious motivations, but even emailing a work document to and from a personal Gmail, for instance, can have destructive consequences — whether employees know it or not. Forrester discovered that 64% of security professionals have challenges identifying data movement between personal and corporate domains like Gmail with their current DLP or CASB solutions. Once a domain is whitelisted, it’s nearly impossible to blacklist every possible iteration of that domain.
Phishing and social engineering
Social engineering is a method of data exfiltration that exploits individuals to get them to reveal sensitive information. Malicious actors pose as trustworthy security professionals and employ techniques based on human psychology to breach security defenses. These actors may pose as a trusted coworker or an executive who will utilize a sense of urgency or fear to pressure employees into giving out sensitive information. Establishing clear communication expectations and training teams to identify social engineering scams is essential to keeping data safe.
Phishing is a form of social engineering where malicious attackers deceive individuals to release sensitive information through email or text. Phishing emails often try to emulate company branding and messaging in hopes to connect with employees through familiarity. The best way to combat phishing is to get ahead of the game by educating employees on email security and authenticity. Conducting regular phishing tests can familiarize teams with the tactics that bad actors might use.
Uploads to external devices and browsers
Another example would be when employees upload company data to websites or clouds that aren’t IT-approved. This is called shadow IT and it can be dangerous. With no way to turn-off employee access upon departure, and an inability to monitor what happens when data reaches that browser destination and beyond, seeing untrusted browser uploads as they happen is critical. This type of threat can be malicious in nature, for example: data theft. A user might upload source code or intellectual property to their external device for personal gain later on.
Downloads to untrusted devices
There could be many reasons why an employee would want to download company data and put it on their phone, tablet, or personal laptop. An employee may download a list of prospects to meet with at a conference, or they may download a report from Salesforce because they are taking that sales list to a competitor. But no matter the intent, downloading data to untrusted devices moves it to untrusted locations that are outside of your domain, causing a breach.
How to detect data exfiltration
Even when you know what data exfiltration looks like in all its forms, it’s challenging to detect. Because there are so many methods and data types by which data exfiltration can occur, it’s near-impossible to categorize. Unstructured data, for example, is harder to detect because sensitive data might be hiding within the native, unsearchable file formats. Below, we examine a few ways analysts and software can work in tandem to identify and stop data exfiltration.
Monitor file activity
Typically, networks act as a natural filtration system, accepting or rejecting attempts to access data. But now that most employees and contractors are working in various locations, the majority of activity is taking place off-network. And outdated VPN technology notoriously brings business to a crawl. Instead, analysts are recognizing the end of traditional perimeters and using software to continuously validate trust and/or monitor data movement directly.
Tools that automatically surface metadata so you can see how files are moved and shared across your entire organization – and most importantly, when they move outside of trusted environments – are aligning security methodologies with workforce changes.
This bird’s eye view of data exposure allows security analysts to distinguish between normal activity and suspicious activity that could warrant a quick response.
Know who has authorized access to data
Data exfiltration gets even more difficult to detect when authorized personnel are the ones leaking that information. That’s why security teams should know who has permission to access sensitive data and continually monitor accounts for changes in behavior. But keeping an up-to-date list isn’t so simple. Authorized users are likely constantly changing, with new employees joining the company and others leaving. Analysts can better judge the risks associated with user activity by using software specifically designed to integrate with Privileged Access Management [PAM] and HR systems to automatically refresh the list of authorized users and pick up on shifts in their behavior.
Respond accordingly to potential threats
Detecting data exfiltration is only the first step in addressing an attack. Once your security team identifies a threat, they must assess the event’s severity, trace its root cause, and contain any damage. With those details in mind, they can put together a mitigation plan that stops the negative impact of data loss on the organization. Of course, this doesn’t mean they can take their time. Security teams must act swiftly to stop data exfiltration at its source and recover sensitive information as soon as possible.
How to prevent data exfiltration
Many businesses use Data Loss Prevention (DLP) software to protect their data against exfiltration, but this methodology can fall short. In order to implement a DLP, companies must set rules that help the system identify sensitive data, block file activity, and send alerts. But that means that your DLP solution is only as good as the rules you set. Sometimes rules can be too sensitive, triggering false alerts that take time and attention away from real threats—and force your security team to needlessly interrupt the workflow of other teams.
Other times rules can be too specific, missing potential threats entirely. To comprehensively combat data exfiltration, you need to:
- Multi-factor authentication: MFA requires users to verify their information in multiple ways. In addition to a login and password the user is sent a code, or uses an app, to verify their identity. This second layer of authentication increases security.
- Offer visibility and context: Organizations need comprehensive visibility into their data exposure and which activities require security intervention. That means closely monitoring computers, cloud applications, and email providers to fully evaluate potential risk.
- Prioritize greatest risks: Companies are constantly bombarded by risks of data exfiltration, but not all of those risks are created equal. The right tools can help security teams identify the events and users that pose the greatest danger and prioritize their responses accordingly.
- Generate an aligned response: Your security analysts need to use their limited time and resources wisely. Ideally, they’ll have access to software that allows them to orchestrate a combination of human and technical responses that are aligned with the severity of the event and situational context.
- Optimize a positive user experience: The best data protection software gives companies a holistic picture of data exposure at their organization by measuring and improving risk posture – without infringing on the employee experience.
- Provide security awareness training: One of your best protections against data exfiltration is your employees. So teach them what steps they can take to keep your company’s data and your customers’ data safe. Leading data protection platforms have built-in features to facilitate employee training, encourage proper use of their tools, and share information securely.
- Use the right DLP tools: When selecting a DLP tool, it is imperative that your DLP technology can keep up with your DLP strategies. DLP technologies are often challenged by complexity and ineffective implementations that fall short when it comes to classifying data and responding to data movement. Make sure your DLP tool is up to the job by seeing if it meets the seven requirements you should consider when evaluating technologies for modern day security.
Keep your data and IP safe
Workforce volatility has drastically changed the way companies and employees work, and the threat landscape has changed along with it. With insider threats and data exfiltration on the rise, your company’s IP is at risk.
Unlike traditional DLP approaches, Code42 Incydr™ is a data protection solution that moves beyond pre-identifying and outright blocking all data exfiltration. Incydr protects high value data like source code, customer data, and more by monitoring data movement across all endpoints, browsers, and cloud services – and prioritizes actions to swiftly address high-risk incidents. The best part? It detects data exfiltration one day 1 without slowing down your business.
Learn more about why Code42 Incydr stands out above the rest for protecting your data.

