Why it’s time for a new response methodology
The ability to automate response controls that are aligned to your organization’s risk tolerance is essential for Insider Risk Management. While this may seem like it’s stating the obvious, it is a capability that even the most traditionally mature security teams struggle with. That’s because security teams today are lacking the context required for accurate risk detection. This results in mountains of false positives or dead end alerts that leave 72% of security leaders without the necessary context to know if they should close the alert or pursue an investigation.
This uncertainty harms the productivity of the security team and contributes to analyst burnout. At the same time, the productivity of end users is harmed when overly harsh response controls are triggered by false positives or inaccurate detection. This sort of blocking culture is frustrating for employees. It causes them to find workaround ways to move data and creates a negative perception of the security team. Overtime, this will result in a workforce that is lacking risk-awareness and ultimately increase corporate exposure to Insider Risk.
Introducing Incydr Flows
Security teams need a new method for responding to Insider Risk, one that enables a response that is right-sized based on context and prioritization. That’s why we built Incydr Flows. By using Incydr Flows to automate common Insider Risk workflows, security teams will:
- Mitigate alert fatigue
- Reduce manual, repetitive or error prone tasks
- Accelerate response times
Incydr Flows are no-code automated integrations that add context and accelerate response capabilities by connecting Incydr to systems like IAM, PAM, ITSM and communication applications. They are built and managed by Code42 professional services to help bring additional context into Incydr and trigger a variety of response controls.
- Incydr Context Flows enhance Incydr’s signal by adding user attributes like employment milestones, departure date, or elevated access credentials, to Incydr risk detection lenses or alert rules.
- Incydr Response Flows automate containment, resolution and educational controls based on the severity of the detected data leak event.
Controls to contain data leaks
Incydr Flows help to contain detected data leaks by taking action at the user, network or device level so that no further data exposure will take place. Containment controls available through Incydr Flows include conditional and privileged access controls, stopping local sync apps, disabling USB ports, locking a device and network containing an endpoint.
For example, the Incydr + Okta Flow automatically removes a user’s access to a specified corporate application on trusted, untrusted or mobile devices. This control is recommended for response in critical situations like when Incydr detects a departing employee downloading their customer list from Salesforce.
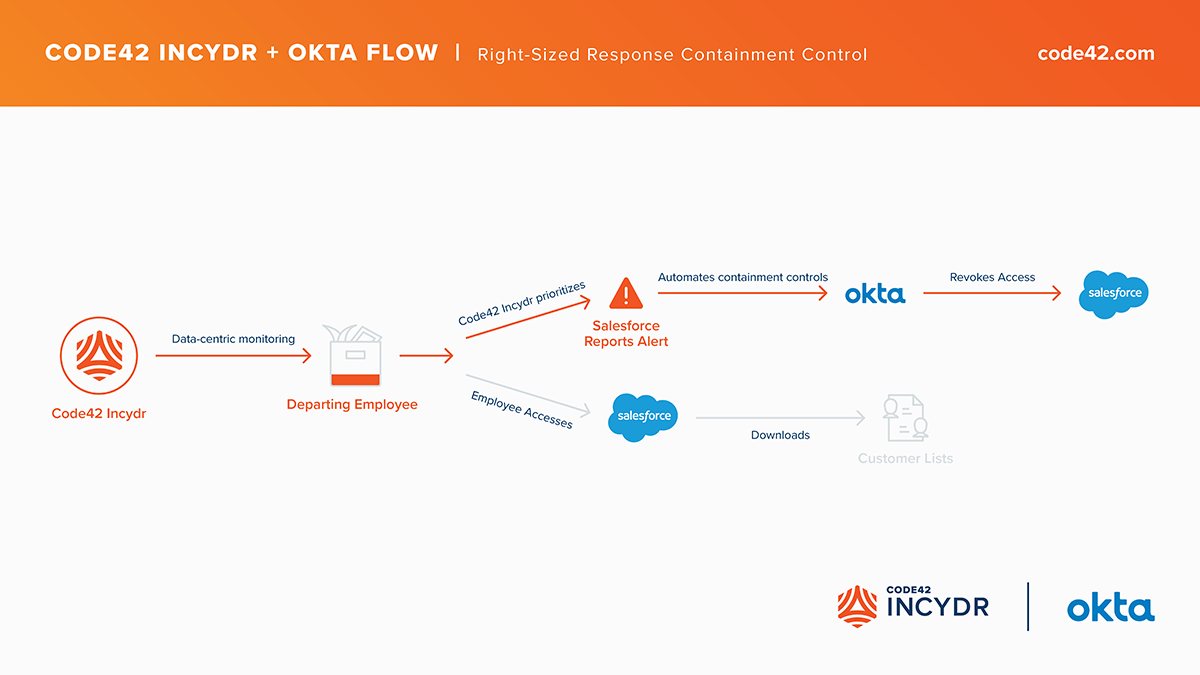
Speed the time to resolve data exposure
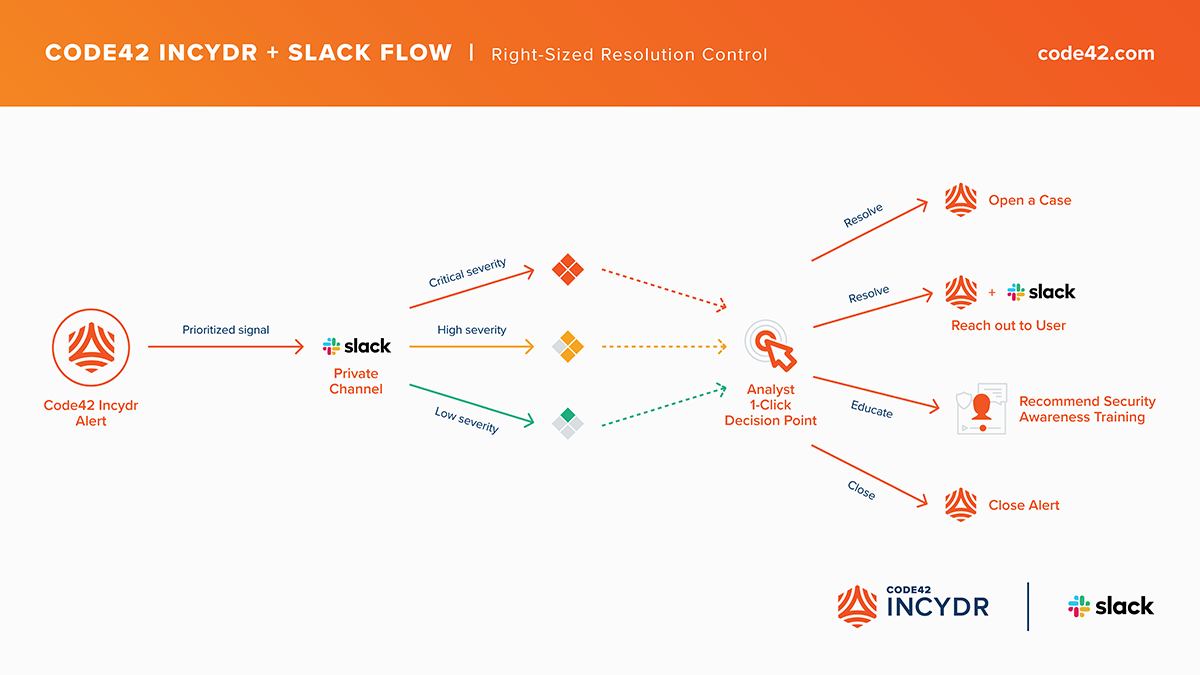
Incydr Flows resolve data exposure by automating processes that rely on data from multiple sources and people from multiple teams. Resolution controls are helpful for automating human controls like an inquiry with the user to evaluate the users intent and ask for a user action to resolve the issue. Other controls may involve follow up action over screen share, or escalations to the users manager, legal or HR.
For example, analysts can use the Incydr + Slack Flow to triage alerts and automate direct outreach to the end user through pre-populated Slack messages.
Use education controls to prevent future data leaks
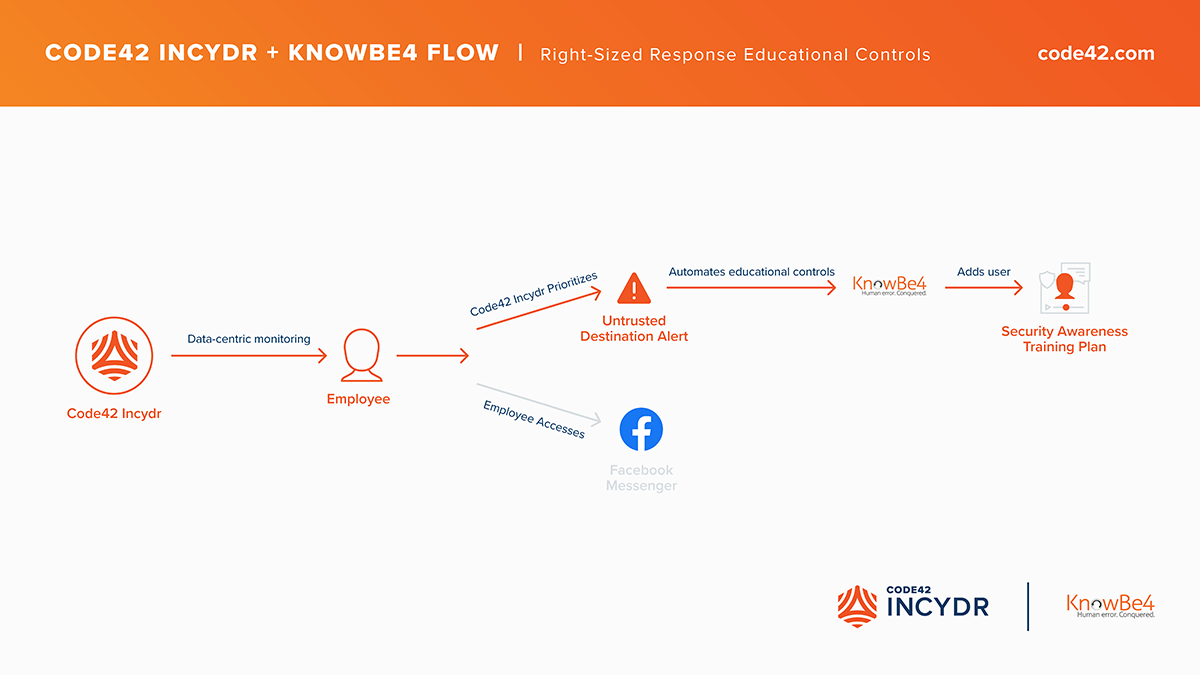
Incydr Flows help to reduce future instances of data exposure so that an organization’s Insider Risk posture improves over time. In response to low severity events, Incydr Flows can recommend security awareness training or ask them to re-acknowledge the corporate acceptable use policy.
For example, if Incydr detects an employee files from a corporate device to a social media messaging platform, an Incydr Flow could automatically add the user involved to a security awareness training plan in KnowBe4.
Insider Risk presents itself in many ways. Each situation is unique based on the combination of the user who took the action, the exfiltration vector used and the data involved. A one-size-fits-all response is an impossible notion, but that doesn’t mean that responding to Insider Risk needs to be complicated, manual or painful.
Want to learn more? Read this white paper for more information about Code42 Incydr’s right-sized response methodology or contact us.
