TechNOLOGY INtegration
Incydr™ Flows, powered by Tines
It’s time to simplify your manual and error-prone workflows.

Today’s Problem
Complex workflows are getting in the way of protecting data
Protecting data and managing insider threat often depends on cross-functional processes and information from disparate systems. The complexity of consistently bringing the right people, processes and technology together to accurately detect and effectively protect data has traditionally been challenging.
Code42’s Solution
Incydr Flows’ no-code automation saves time for security
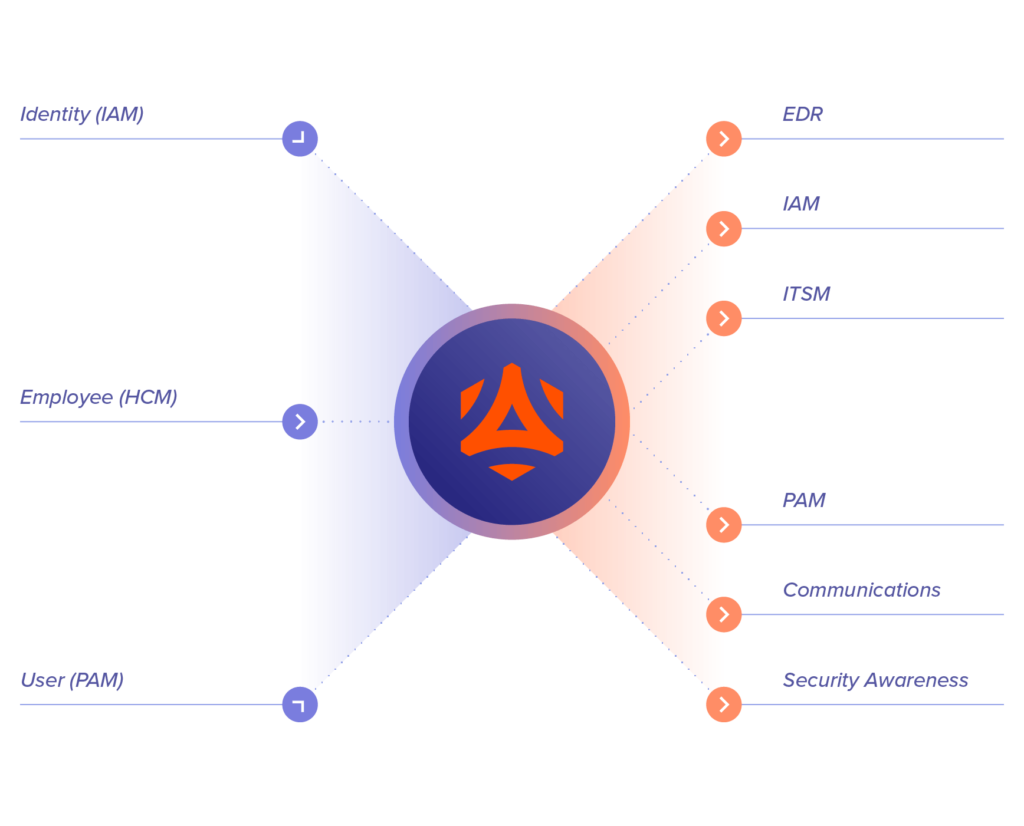
Incydr Flows, powered by Tines, allow security teams to automate actions between Incydr and other corporate systems like IAM, PAM, EDR, HCM, ITSM, and email security in order to save time and increase effectiveness. Since Incydr Flows are powered by Tines and are incorporated into the Incydr product, you simply purchase Incydr Flows from Code42 for a nominal fee and do not need to purchase Tines separately.
With Incydr Flows, security teams will:
Triage alerts
Contain threats by removing user access
Manage Watchlists
Contain threats by quarantining endpoint
How It Works
Automate workflows between Incydr and your current tech stack
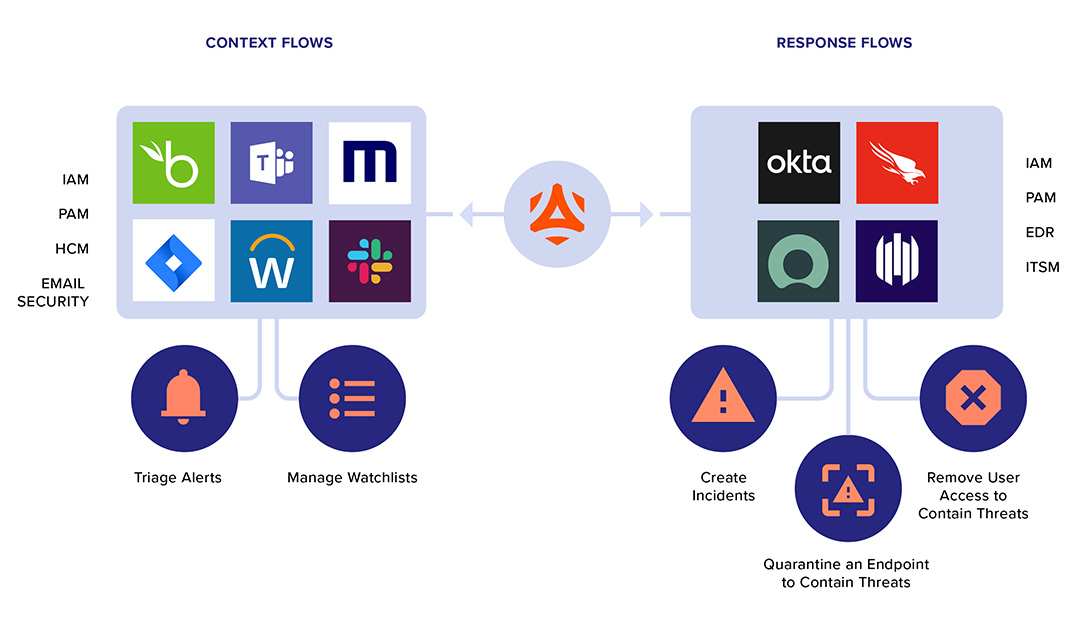
Context Flows
Context Flows ingest user attributes, such as employment milestones, departure or access details from corporate IAM, PAM, HCM, and email security systems. With user context from these systems, Context Flows automatically add users to alert rules or Watchlists for heightened monitoring.
Learn MoreResponse Flows
Response Flows orchestrate controls to mitigate corporate data leak. These controls are intended to contain active insider threats and can be automated based on the severity of an event. They are delivered through integrations with systems like IAM, PAM, EDR and ITSM.
Learn MoreGet In Touch


