CASB vs Code42
CASBs Are No Longer Enough
Discover why cloud access security brokers can no longer keep up with modern data protection requirements.
Shortcomings of CASB in today’s data architecture
Cloud access security brokers (CASBs) were designed to keep data in the cloud safe. But with the advent of remote work, proliferating cloud apps and increasing data sprawl, CASBs are struggling to contain insider threats. Why CASBs fall short:
No protection in data movement beyond the cloud
A user downloads data to their working machine and uploads it to a different service. Once data is stored on the endpoint, CASB loses all visibility and context – creating significant risk.
Often requires TLS inspection or proxy
Nothing is more frustrating than investing in a tool that creates performance bottlenecks or becomes too complicated to maintain. Or even worse – routing all traffic through a proxy only for it to fail.
Blocking the known vs. the unknown
It’s impossible to identify every data loss scenario at your organization, and CASBs require constant policy tuning for each change in information flow. This often leads to a one-size-fits-all response strategy which disrupts legitimate business and causes extreme response to simple, every day employee mistakes.
Restrictive policies hinder productivity
When a CASB policy blocks employees’ file-sharing ability or restricts their access to commonly used cloud applications, employees resort to unapproved tools or bypass the CASB policies altogether – creating new security risks.
Code42’s Solution
Go beyond policy-based protection
To effectively prevent data loss, organizations need a data protection solution that goes beyond the limitations of policy-based defenses. Code42 Incydr™ offers a risk-based approach to reduce data loss by automating response to everyday mistakes with Instructor™, investigating what’s unusual, and blocking the unacceptable. Even Okta chose Code42 over a CASB to avoid data leak from the cloud.
| Features | CASB | Code42 |
|---|---|---|
| Monitoring capabilities | Monitors cloud applications only | Monitors both endpoint and cloud-based applications |
| Protection of data in motion | Only protects data in the cloud | Protects data in motion regardless of where it’s stored |
| Monitoring of email | Limited monitoring capabilities | Comprehensive monitoring capabilities, including email and ability to distinguish personal from corporate accounts |
| Data exfiltration detection | Limited detection capabilities | Advanced detection capabilities using behavioral analysis and a Trust Model |
| User education and prevention | Basic capabilities | Advanced just-in-time micro-trainings and integrated case management to prevent data loss |
| Context and visibility of data | Limited visibility and context | Provides context and visibility for each file, including built-in access to file contents |
| Real-time blocking | Enforce complex data-centric security policies based on burdensome data classification | Block unacceptable data movement based on the user without the management burden, inaccuracy, and endpoint impact of content-based policies. |
3 ways Code42 works better than a traditional CASB
Leverages API connections to monitor cloud-based & endpoint applications
allowing for complete visibility across an organization’s entire data landscape – without needing proxies.
Advanced detection of data exfiltration using behavioral indicators
and a Trust Model, enabling organizations to quickly identify and respond to potential data security incidents.
Just-in-time micro-trainings and integrated case management
to prevent data loss, empowering employees with the knowledge and tools they need to make informed decisions about data protection.
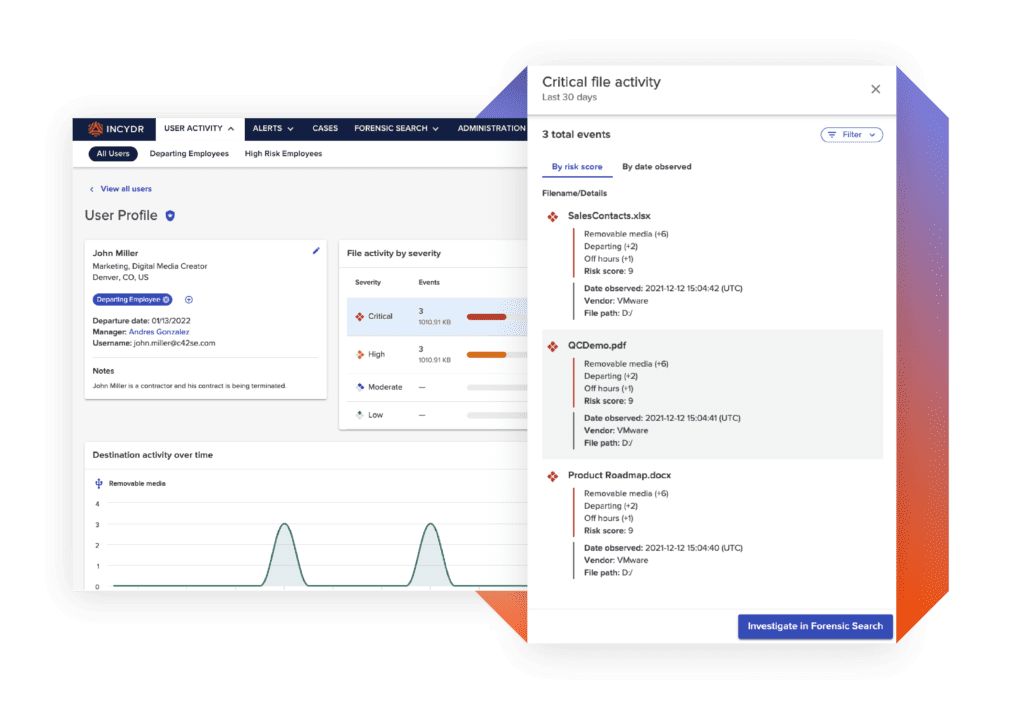
How Incydr WorksCustomer StorY
Why Okta Chose Incydr Over CASB to Avoid Data Leak from Cloud File Sharing
“Incydr stood out for how quickly it could be implemented and see value within the month. Incydr’s direct, API-to-API approach to integrate with cloud and email systems meant Okta would not need to set up and manage a proxy server in order to avoid accidental data leak via cloud file sharing and email.”
– Matheo Lord-Martinez, IT Security Director at Okta
$$$$ just got real. Data leaks from the cloud happen daily.
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before major damage is done.
Try Incydr5 min
after turning on Incydr, a customer discovered 30GB of data exfiltration via DropBox.
Resources
There’s a better way for companies to protect their data than CASB

Annual Data Exposure Report 2023
CISOs rank insider risk as the most difficult threat to detect in Code42’s latest data exposure report.
Download Report
What Is A Cloud Access Security Broker (CASB)?
Gain a deeper understanding of what CASB is, how it works and its limitations when protecting data on the cloud.
Read Blog
Why Traditional Security Tools Aren’t Getting The Job Done
Forrester survey results show that the DLP and CASB tools are not aligned with security’s changing priorities related to securing the collaboration culture.
Read Blog