IP Theft Protection
Prevent Intellectual Property Theft
Intellectual property theft can be carried out by the people closest to sensitive data – including employees or contractors – and it’s among the most damaging security breaches.
Easily prevent your company’s valuable IP from leaving your organization with Code42 Incydr™.

The Problem
Too many files containing IP data + too many places they can go
Digital change is happening much faster than security teams can update policies. As files become easier to share and employees move from job to job, intellectual property has become harder to monitor and protect than ever. Security teams are one exfiltration away from an IP theft data breach due to:
Too many data exfiltration blind spots
Excess alerts on low-risk events
No details on exact files exfiltrated
The Solution
Differentiate IP theft from every day low-risk events
It’s time to stop living in fear of being the next data breach headline in the news. Code42 Incydr takes a new approach to detecting IP theft – making file signatures and classification tagging a thing of the past.
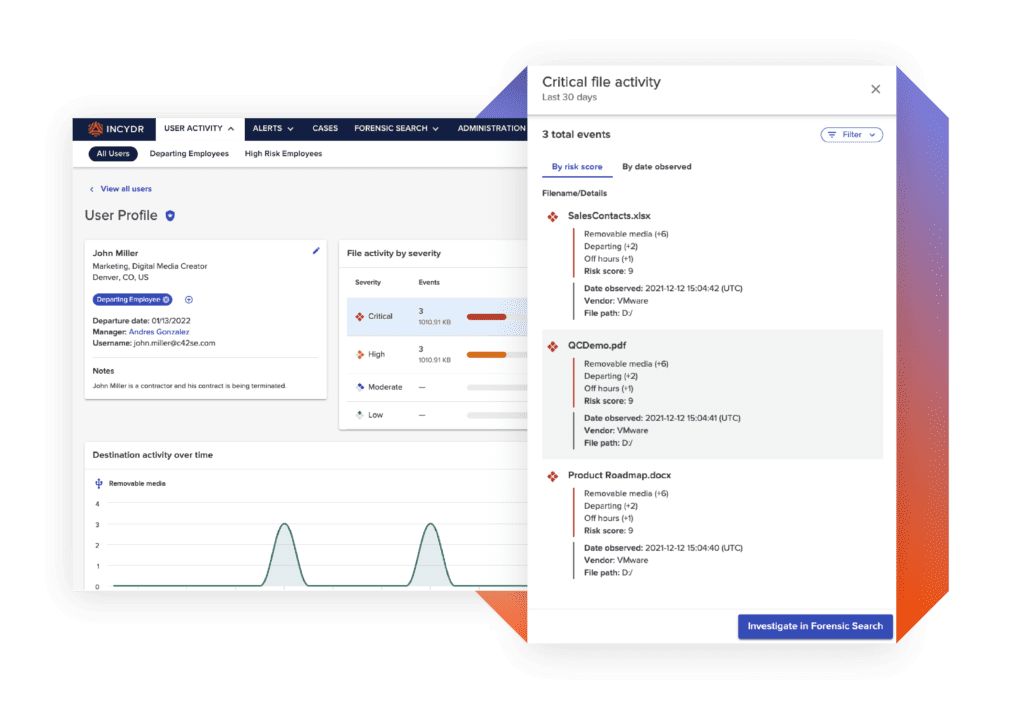
Incydr provides complete visibility into your organization’s data exposure to eliminate blind spots. It automatically differentiates between real threats and low-risk events, so you can spend less time addressing alerts and more time investigating IP theft incidents.
Incydr is built to protect intellectual property theft
What makes Incydr stand out?
Visibility into cloud and endpoint exfiltration in one, including Git push/pull activity, Salesforce downloads, Airdrops and cloud syncs
Correct users when data is shared incorrectly using Code42 Instructor™ lessons that prevent risky activity from becoming the norm
Validate actual file contents to know for sure how sensitive the data the is
Implement real-time blocking for high-risk employees working closely with intellectual property
How Does Incydr Work?Our customers protect their IP from leaving behind their back
Let us show you how they see and stop data leaks with Incydr and Instructor.
Connect With Sales
Remote Workers
Remote workers introduce new security challenges. We help you manage the risk of off-network activity when employees work from home.
Learn MoreContractors
As temporary members of the organization, contractors present a heightened risk for data theft. Monitor files access and flag unusual or unauthorized activity.
Learn MoreDeparting Employees
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
Learn More