Data Governance & Compliance
Maintain Compliance Without Disrupting Productivity

GRC & security teams can partner to reduce corporate data risk
Stopping the misuse of sensitive data and confidential information is an integral part of a company’s compliance and data governance. But finding the right way to protect that data without locking down access or slowing the workforce isn’t clearly defined in the major standards and frameworks that guide GRC teams.
CIS, NIST and ISO frameworks indicate the importance of both endpoint and cloud visibility and controls to ensure data is only moving to trusted locations. But employees work everywhere now – and infrastructure, networks and data are not tethered to corporate offices – making it harder than ever to get a comprehensive view of data risk.
Simply put, compliance frameworks require GRC and security teams to partner in order to understand employees’ use of corporate data. These teams need to think about the following questions:
- What is considered untrusted data use?
- What untrusted data use poses extreme risk to the organization?
- What is a suitable method of remediation?
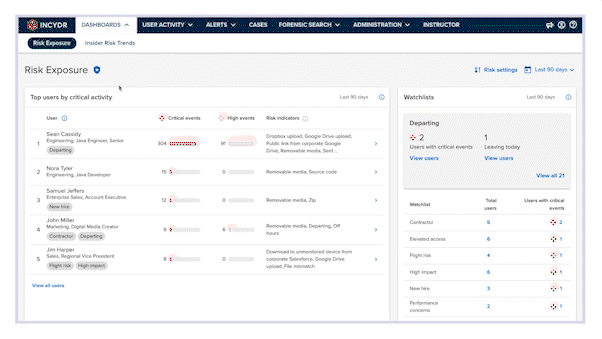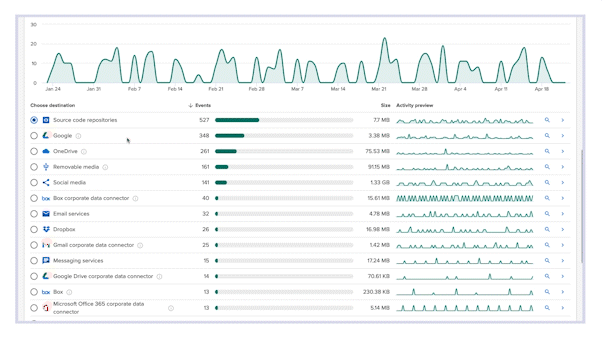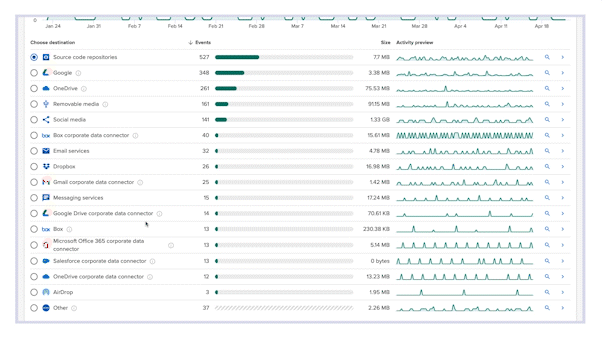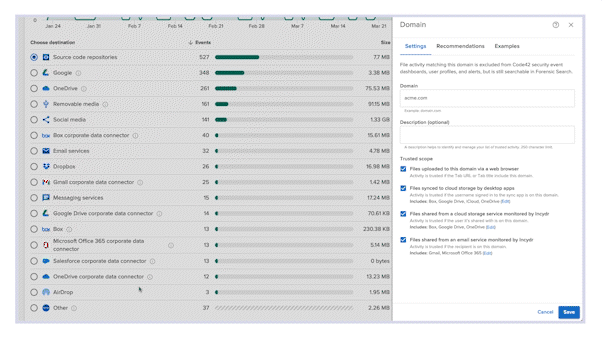
Code42 Incydr™ can answer these questions for your team by offering complete visibility to your data exposure, as well as effective features to control or reduce that exposure.
| Control Family | Security Framework | How Code42 Addresses This Control |
|---|---|---|
| Data Protection | • CIS CSC v8 • ISO 27002:2022 • NIST 800-53 • NIST 800-171 | • Detect, investigate, respond and block |
| Insider Risk | • NIST 800-53 | • Manage and support investigations • Service offerings to develop insider threat programs |
| Monitor & Alerting | • ISO 27002:2022 • NIST 800-53 • NIST 800-171 | • Monitor data movement across users and channels • Adjust risk settings and alerts • Monitor users of similar risk levels |
| Storage Media | • ISO 27002:2022 • NIST 800-53 • NIST 800-171 | • Detect, block and alert on file activity to/from storage media |
| Awareness & Training | • CIS CSC v8 • ISO 27002:2022 • NIST 800-53 • NIST 800-171 | • Correct user behavior with micro-trainings |
| Audit | • NIST 800-171 | • Detailed information at a user level and file metadata level |
Code42’s products and services offer advanced compliance solutions
Incydr, Instructor and Insider Risk Management services help strengthen data governance, mitigate data risk, and enable organizations to monitor and enforce compliance expectations.
- Gain full visibility into risk exposure from endpoints, browsers and cloud apps with visual reports tailored for both an executive audience and analysts involved with data governance
- Reduce risk by stopping untrusted data movement and drive secure work habits with bite-sized employee training delivered in real-time
- Enforce compliance expectations with a range of controls including just-in-time microtrainings and real-time blocking that let you respond automatically to data risk events in a way that’s proportionate to their severity
Hear what our customers have to say on Gartner Peer Reviews
From public organizations creating new medicine or growth-focused tech leaders, our customers are balancing employee productivity with their audit response requests and meaningful security maturity. Hear how they use Code42 Incydr to manage these pressures.
Read Incydr Reviews


