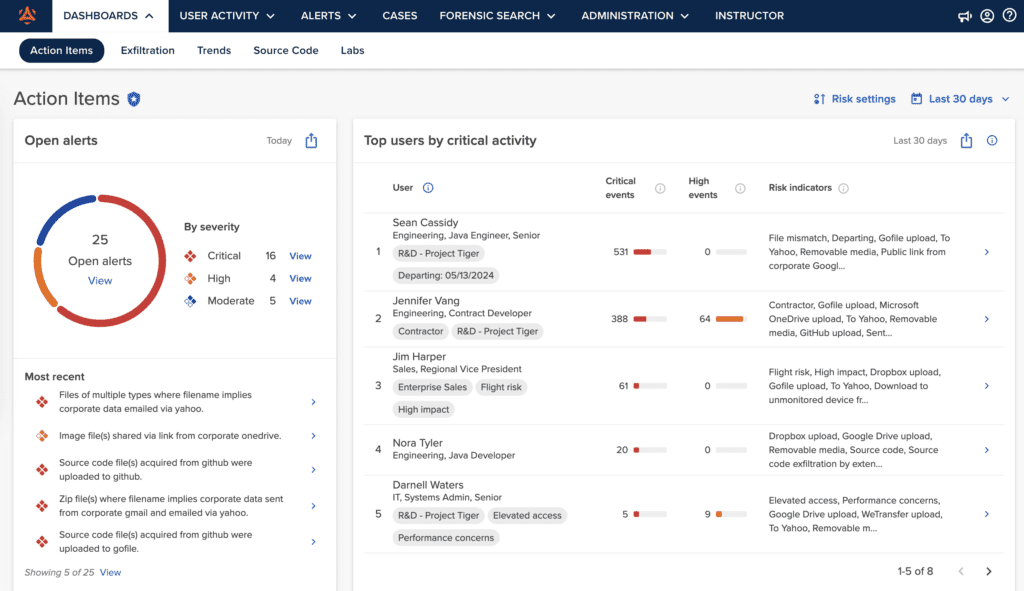
Action Items Dashboard
Effortlessly manage your to-do list with the Action Items dashboard. From here, you can view all open alerts, top users by critical activity, upcoming departures, unwatched security lessons, and open cases in one convenient location.

Exfiltration Dashboard
Explore the Exfiltration dashboard for a new perspective on data movement in your environment. Identify trends and reduce risk with informed decision-making.
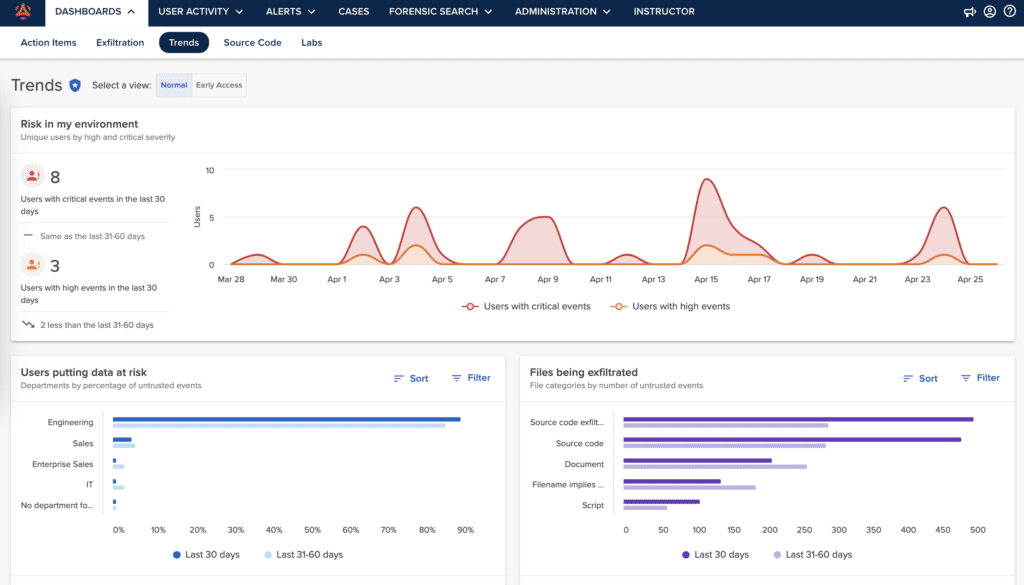
Trends Dashboard
The Trends dashboard is designed for an executive audience to easily track program progress and compare it to previous months.

Source Code Dashboard
Get context on source code movement with the Source Code dashboard, empowering analysts to swiftly pinpoint potential risks in their organization.
With Incydr’s dashboards, you will:
Get context for quick response
Quickly assess risky activities and receive recommendations from one convenient page for prompt action.
Uncover data visibility gaps
Eliminate data blindspots with Incydr’s dashboards for complete exfiltration visibility across your entire environment.
Detect source code leaks
Get in-depth information on unauthorized source code transfers and how to prevent them effectively.
Build a program that lasts
Measure and improve your data protection program to prove Incydr’s ROI to leadership teams.
Want to see these Dashboards in action?
Get a tour of how Incydr’s dashboards make it easy to detect and measure data loss from insiders.
Connect With Sales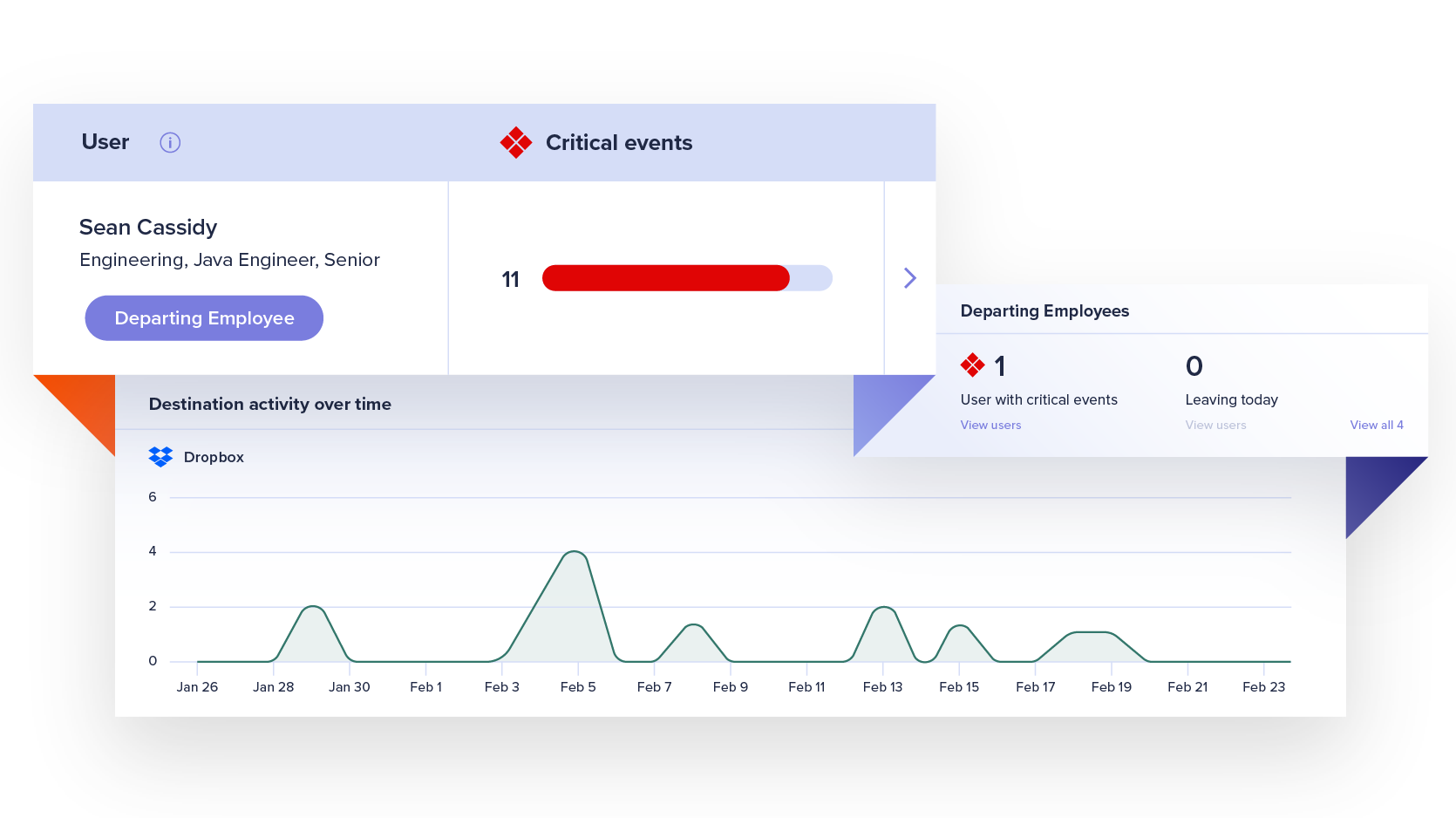
Features
Easy-to-use capabilities that stop data leaks in their tracks
Watchlists
Automate management workflows and get focused visibility into file activity for a subset of users who are more likely to put data at risk, such as departing employees.
Learn MoreForensic Search
Investigate event details and custom query a comprehensive, cloud-based index of activity metadata without putting strain on employee devices.
Learn MoreResponse Controls
Implement effective, automated responses to protect data without disrupting productivity or burdening security teams.
Learn More