Risk Exposure Dashboard
The Risk Exposure Dashboard provides a company-wide view of suspicious file movement, sharing and exfiltration activities.
Learn More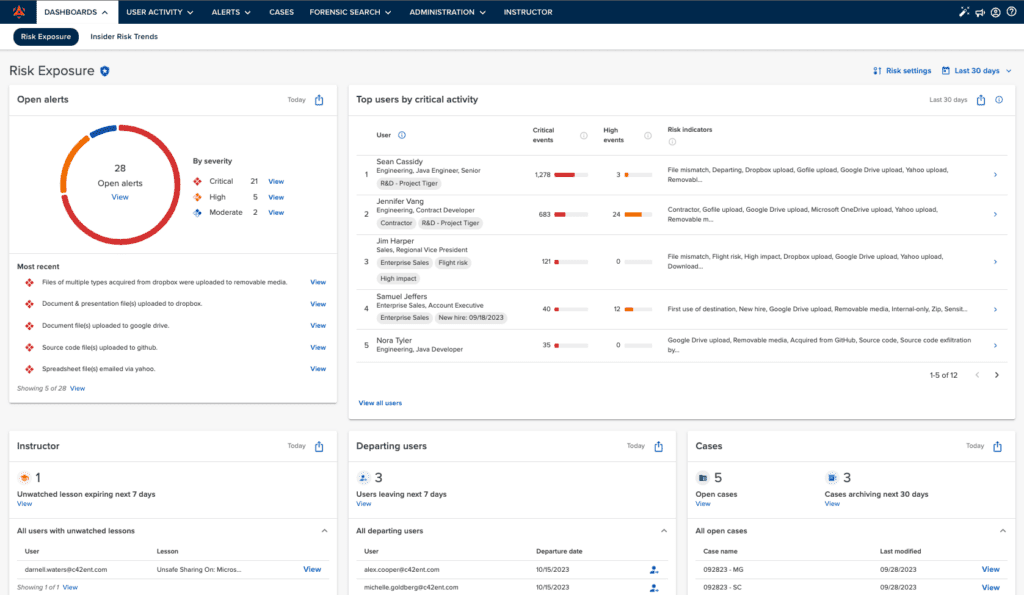
Risk Trends Dashboard
The Risk Trends Dashboard is tailored for an executive audience who needs to report on the current state of IRM program efforts, and how that compares to months past.
Learn More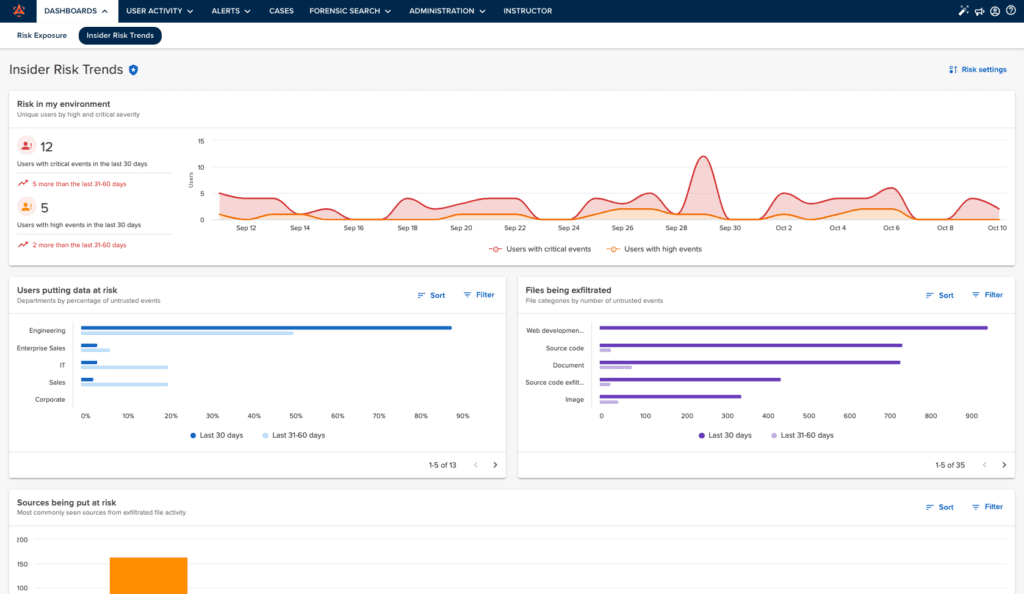
Risk Exposure Dashboard
Monitor file exposure from people and places you don’t trust with the Risk Exposure Dashboard
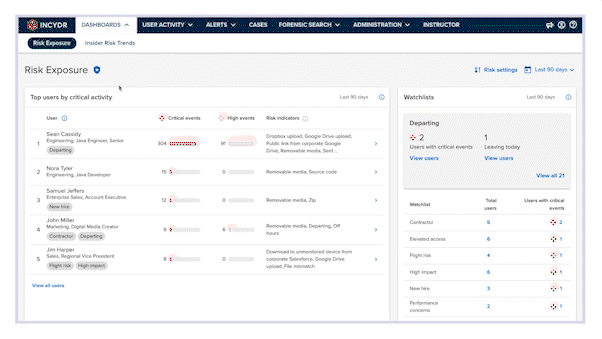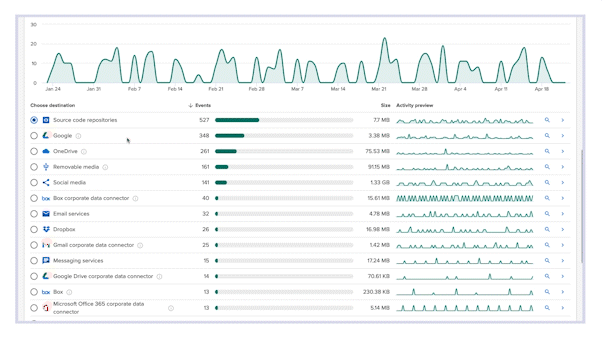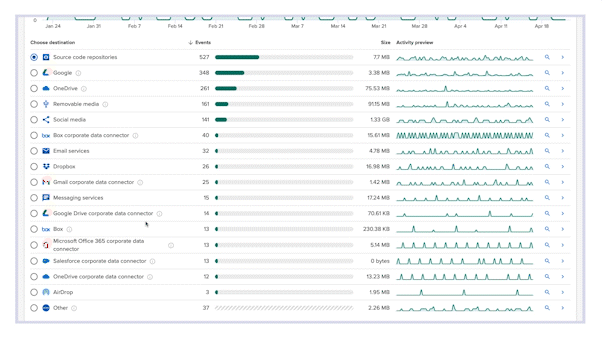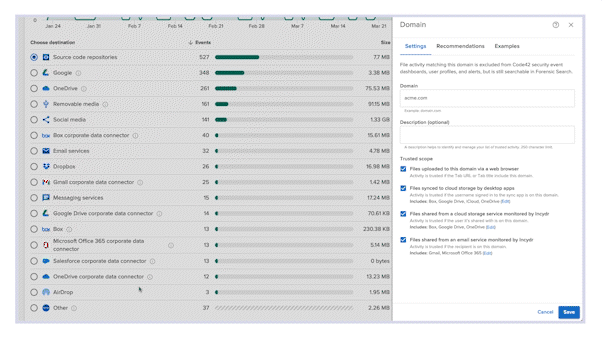
- Audit unsanctioned file movement
Detect files going to untrusted destinations, and review activity by exfiltration vector or file type.
- Review highest risk users
A userlist prioritized by critical events tells you exactly whose activity requires investigation, and why.
- Know exfiltration vectors in use
90-day historical visibility gives you an understanding of file movement trends by exfiltration method.
- Pinpoint gaps in training and tools
Uncover and address employee workarounds, corporate policy violations and improper file sharing.
Risk Trends Dashboard
Measure and improve your data protection program with the Risk Trends Dashboard
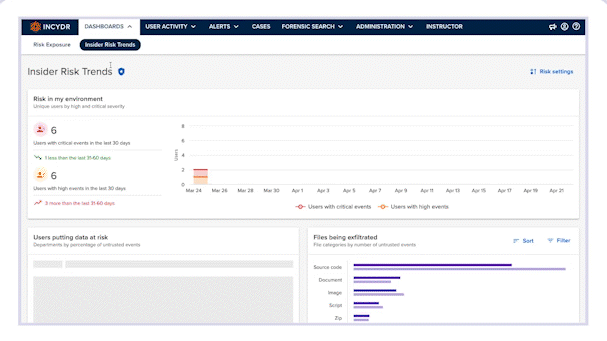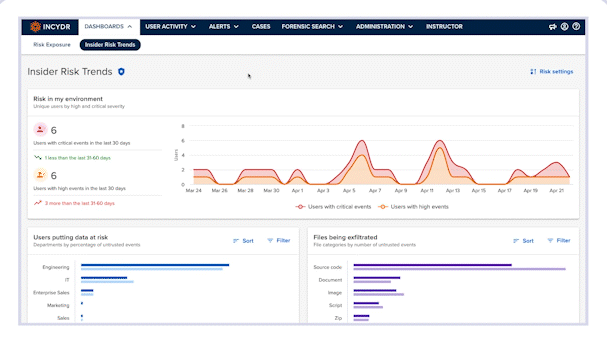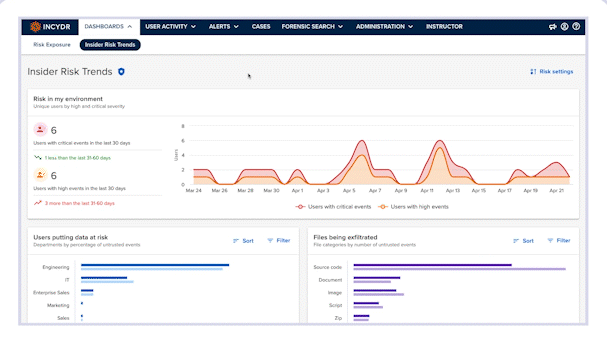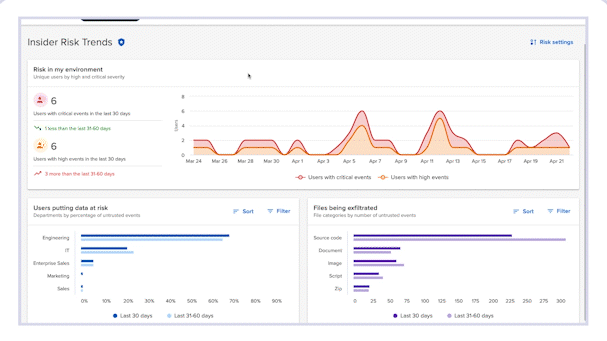
- Identify Insider Risk trends
Review trend information on Incydr events by severity, the riskiest departments with untrusted file events and more.
- Make policy, tech and training adjustments
Use dashboard insights to make the programmatic changes needed to drive secure work habits across the organization.
- Measure behavior changes over time
Evaluate how program adjustments impact your Insider Risk posture and measure how effectively your actions are reducing risk to data over time.
- Share insights with leadership and the Board
Report out on the effectiveness of your corporate Insider Risk Management program and use learnings for organizational alignment and prioritization.
Want to see these Dashboards in action?
Get a tour of how Incydr’s dashboards make it easy to detect and measure data loss from insiders.
Connect With Sales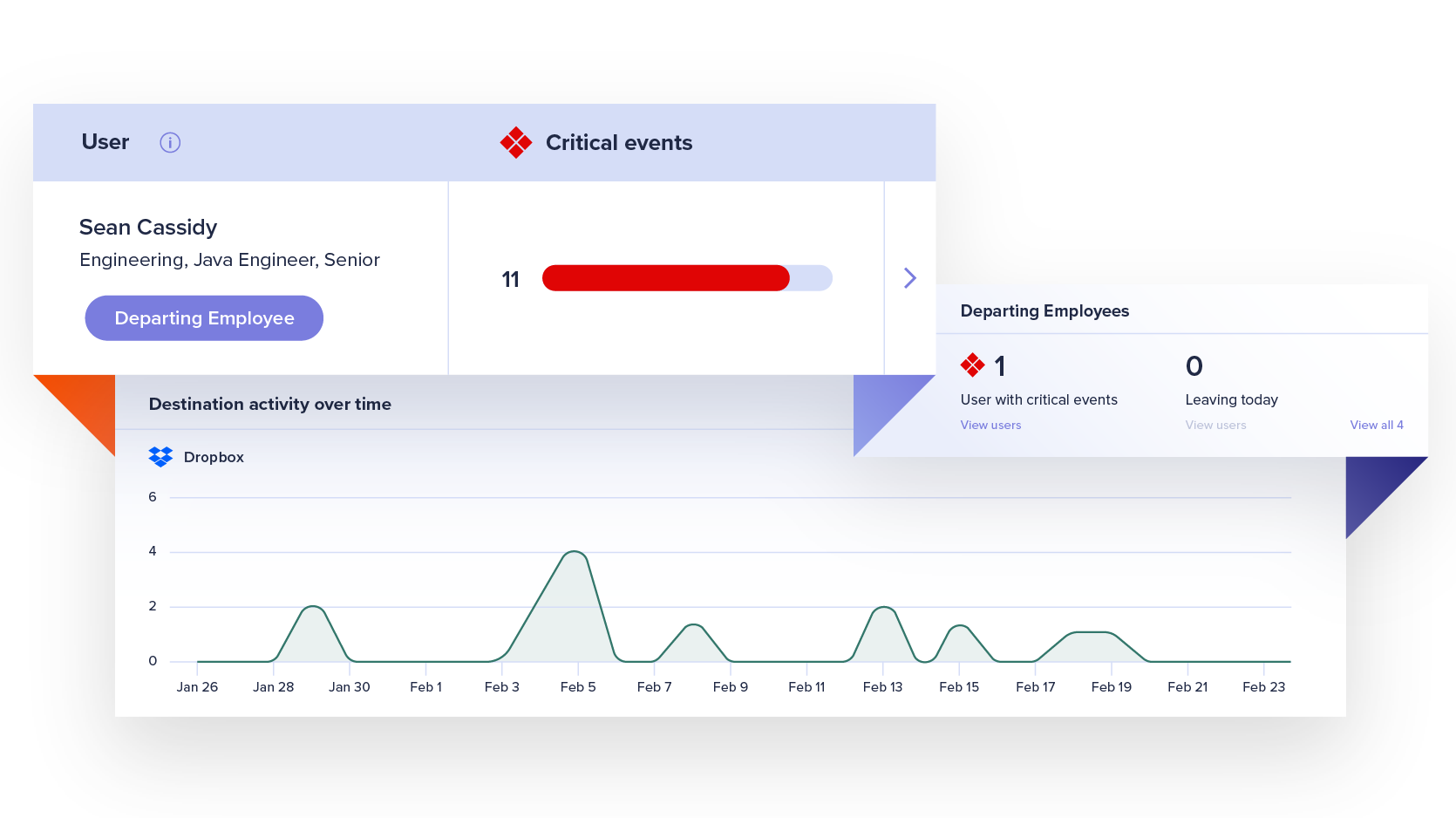
Watchlists
Automate management workflows and get focused visibility into file activity for a subset of users who are more likely to put data at risk, such as departing employees.
Learn MoreForensic Search
Investigate event details and custom query a comprehensive, cloud-based index of activity metadata without putting strain on employee devices.
Learn MoreResponse Controls
Implement effective, automated responses to protect data without disrupting productivity or burdening security teams.
Learn More