Latest Data Protection Enhancements From Code42
Code42 Product Benefits
Spend less time administrating
and more time protecting your data
Complete data visibility
Incydr has visibility into all data movement including cloud sharing, browser uploads, unstructured data & more.
Prioritize threats quickly
Focus your attention on untrusted data activity and see the actual file contents that were exfiltrated with Incydr.
Effective response controls
Preventative blocking, automated security education & more help correct user behavior without draining resources.
Incydr™ Product Release Summary
At Code42, we’re always working hard to improve our products and provide the best possible data protection for our customers. We’re excited to share with you some of the latest enhancements we’ve made to Incydr over the last few months.
Data Visibility
Data Movement visualization
Interactive visualization into all your data movement
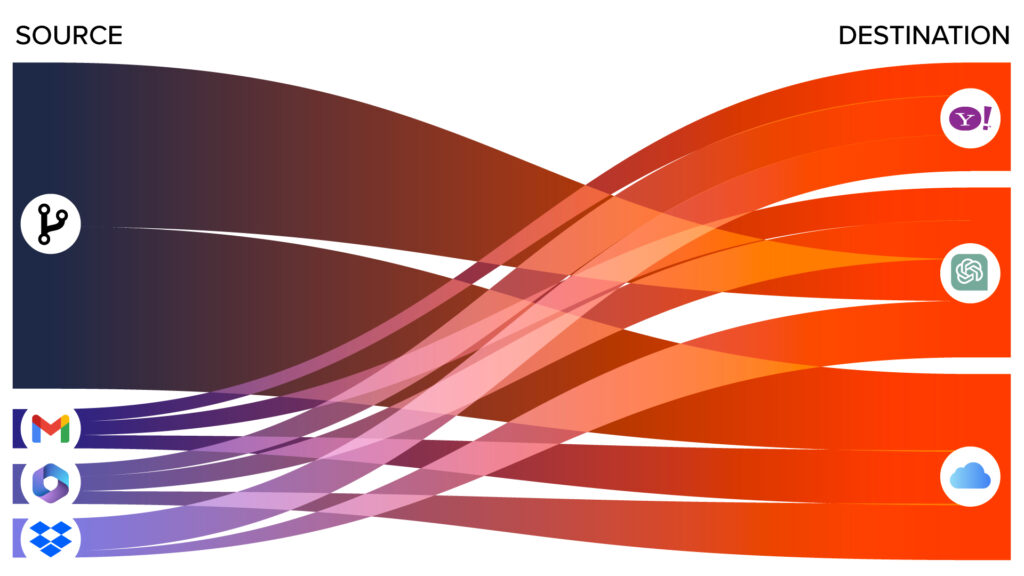
It’s a new dashboard containing an interactive Data Movement section that shows how data in your environment is moving to untrusted destinations. This enables you to better recognize trends and make decisions to lower overall risk.
Incydr detects and surfaces all data movement across endpoint, cloud, and email. With this new dashboard feature, you can easily apply filters to see where your data is coming from and going to, giving you even more insight to unknown risks.
Visibility into data movement is key for organizations. It’s easy to understand the risk of data movement for places you know to monitor, like your corporate sanctioned destinations. But what about places you aren’t monitoring? The data movement visualization helps quickly show you where your important data, like source code, is moving and when it’s moving to untrusted locations so you can lower your overall risk.
Data Visibility
Source Code dashboard
Easily monitor source code exfiltration

Get context on source code movement with the Source Code dashboard, empowering analysts to swiftly pinpoint potential risks in their organization.
View in-depth details about source code activity in your environment, including:
- Source code files pushed from trusted corporate repositories to unmonitored and potentially risky destinations
- Patterns of source code movement
- Top users with risky activity
- Activity for all destination repositories, categorized by ownership type (personal, organization) and privacy settings (public, private)
- Untrusted repositories with the most activity
The Source Code dashboard enables you to easily investigate specific Git activity, as well as add Git repositories and accounts to your list of Trusted activity.
Prioritize Threats
Generative AI Incydr Risk Indicators
Stay ahead of potential data leaks by monitoring files and content shared via Generative AI tools

The generative AI platforms, drawing prompts and data from millions of users, can unintentionally reveal sensitive information. The very traits that empower AI – speed, automation, and learning abilities – pose significant risks to data protection efforts by increasing the likelihood of data exposure and breaches.
Incydr surfaces data movement to 13+ generative AI tools out-of-the box, with the ability to create custom risk indicators for any additional generative AI tool. Our context-driven prioritization model will automatically score and surface data movement to generative AI tools to your analyst so they can take the proper response action.
Prevent data leaks proactively by monitoring files shared through Generative AI tools. Incydr efficiently identifies risks in company file uploads and can block copy/paste action. Stay informed about potential data leaks and take immediate action.
Data SECURITY ASSESSMENT
Is your sensitive data walking out the door? Find out for free using the latest features.
Get A Free AssessmentTrusted by security. Preferred by employees.
“Incydr is easy to implement, configure, and use!”
“Service and support has been excellent. Knowledge base documentation is well written and clear. It’s very easy to find what I need quickly. Information is presented in the dashboard in a very clear way, making things super easy to understand. Professional services has been very helpful.”
Read More 5-Star Reviews