Detect Source Code Leaks & Avoid IP Theft

Code42 Incydr™ detects source code exfiltrations to untrusted repositories without needing to know what to look for – offering much-needed protection of source code without disrupting the productivity of engineering teams.
Respondents to the 2024 Data Exposure Report rank source code as one of the top three most valuable IP data types – especially for technology, medical device, and software companies. Yet, protecting it from unsanctioned use is difficult for security teams. 88% of security leaders wish they had more visibility into source code that is sent to repositories to ensure it doesn’t end up in the wrong hands.
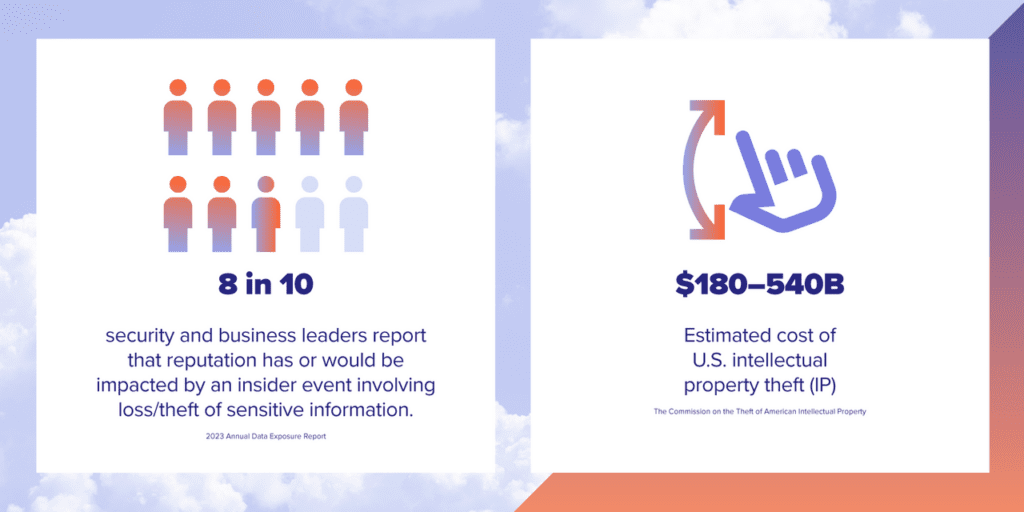
The most recent update from the Commission on the Theft of American Intellectual Property estimates the cost of U.S. intellectual property theft (IP) at between $180 billion and $540 billion. Having a way to accurately detect and respond to IP theft helps businesses avoid financial loss, protect their competitive advantage, and yes, ensure no damage is done to their reputation.
Software developers utilize Git to create source code. Much of their Git usage is sanctioned as part of their everyday work – creating or pulling existing code and pushing it to corporate and/or open source repositories. However, engineers who want to exfiltrate IP could also use Git to send code to a personal code repository service, such as GitHub.
Code42 Incydr watches all Git activity to identify if the code came from your corporate repository. This allows security to accurately pinpoint source code exfiltration and speed response times without getting in the way of sanctioned development or impacting engineering team productivity.
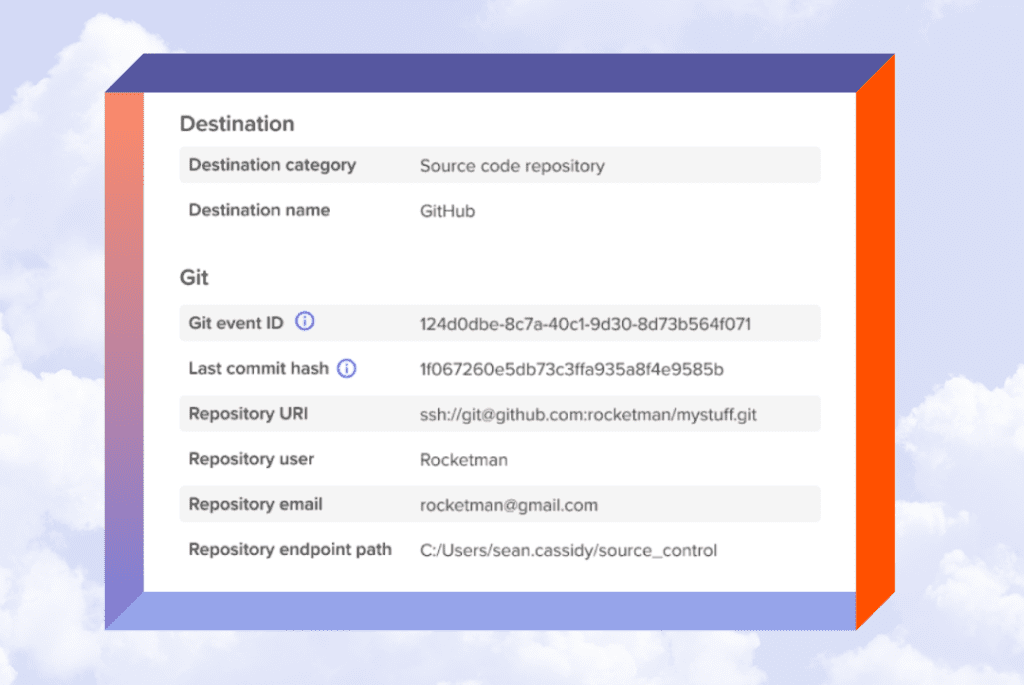
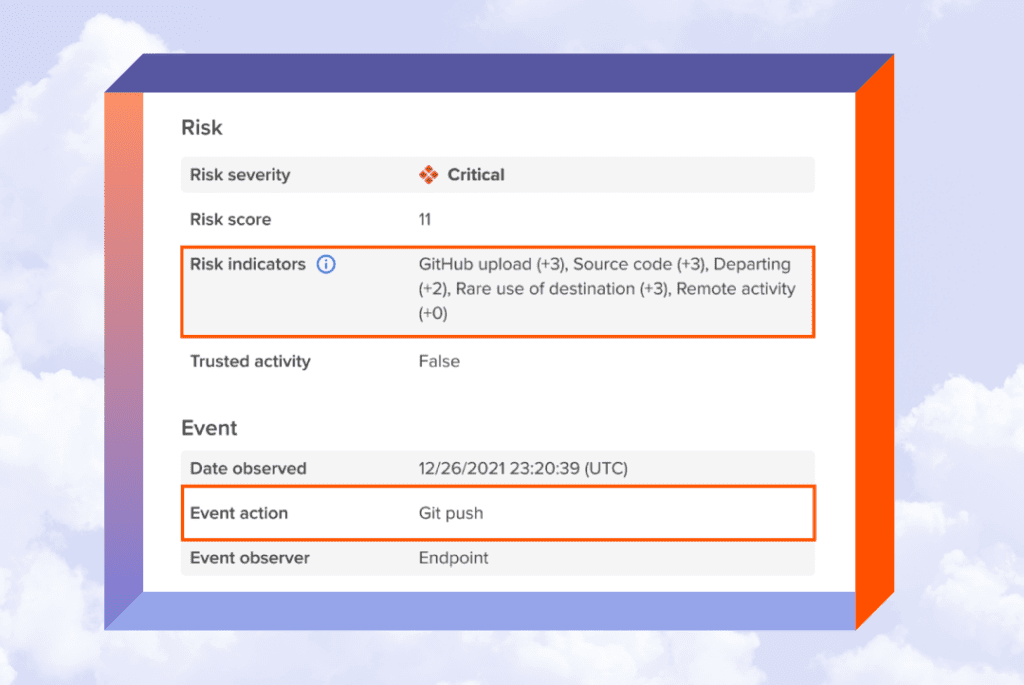
With Code42 Incydr, security teams can:
- Continuously monitor developer endpoints for Git commands
- Access the Source Code Risk Dashboard for easy visibility into all the risky Git activity
- Ensure legitimate Git push activity does not generate alerts, thus avoiding alert fatigue for administrators
- Custom source Incydr Risk Indicators (IRIs) for source code repository paths so you can identify your highest value repository
- Monitor Git pull, clone, and fetch activity to trace files coming from a corporate repository
- Receive alerts on unsanctioned source code movement
- Tailor your response to risk based on the offender and the offense with a full response strategy
Watch our product demo:
Our customers keep their source code firmly where it belongs
Connect With Sales
The post Detect Source Code Leaks & Avoid IP Theft appeared first on Code42.