Tech Comparison
Proofpoint vs Code42:
Uncovering Key Differences
You want to get the best-fit data protection in the easiest way possible. To help simplify the process, we’ve outlined the key differences between Code42 Incydr™ and Proofpoint Sigma™ cloud-based data protection solutions – and why Incydr is a better solution to protect you from insider threats.

Identify the right data protection solution for your busy, lean team
Proofpoint Sigma provides user activity monitoring and data loss prevention through risk scores, screen recording and alerts. It intrusively surveils all employee behavior and activity, regardless of the risk posed or value of data moved.
On the other hand, Code42 Incydr protects your data without requiring you to know everything about it or how it’s used. Incydr shows where data is going, how it’s getting there, who’s moving it and when – so you can quickly understand the risk, automate response to everyday mistakes, block the unacceptable, and free up your time to investigate what’s unusual.
Why Incydr delivers better value than Proofpoint Sigma
Save time
Proofpoint evaluators should consider how much time will be spent on deployment and administration due to policy management. With Incydr, detected events are prioritized on day 1, right out of the box.
Reduce user impact by 4x
Customers complain about Proofpoint’s agent footprint and memory utilization, which uses 4x more endpoint resources than Incydr.
Get greater visibility
Proofpoint is policy-driven, while Incydr is context-driven. Poorly calibrated Proofpoint policies allow high-value data slips. Incydr uncovers both known and unknown risks using its context-based Incydr Risk Indicators.
Change user behavior
Proofpoint Sigma’s response strategy relies on blocking as the primary method to protect data, which we know disrupts users and creates rogue employees. Code42 offers 95+ persona-based lessons to correct behavior when it happens. Customers like Crowdstrike have used these trainings to reduce low-risk events by 36%.
Prioritize employee privacy
Proofpoint’s monitoring techniques, like screen recording, border on surveillance. Incydr delivers security teams the information they need without invasive monitoring. This approach not only respects employee privacy, but also enhances user productivity and leads to a better company culture.
How Incydr stacks up against Sigma
Here’s a snapshot of how exactly Code42 Incydr’s key capabilities compare to Proofpoint Sigma.
| Feature Name | Code42 | Proofpoint | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Rapid Deployment and Ease of Use
|
|||||||||||||||||||||||||||||||||||||||||
|
Policy creation & management
|
No policies. Detected events are prioritized out-of-the-box on day 1. | Requires you to set up policies and determine what events are risky on your own. | |||||||||||||||||||||||||||||||||||||||
|
Corrective Response Controls
|
|||||||||||||||||||||||||||||||||||||||||
|
User blocking
|
|||||||||||||||||||||||||||||||||||||||||
|
User containment
|
Unknown | ||||||||||||||||||||||||||||||||||||||||
|
User correction
|
Pop-ups and 95+ micro-trainings | Focused on email and phishing use cases only; requires Proofpoint Security Awareness Training | |||||||||||||||||||||||||||||||||||||||
|
Impact on User Systems
|
|||||||||||||||||||||||||||||||||||||||||
|
CPU Usage
|
Typically less than 1% usage | High memory usage slows down devices | |||||||||||||||||||||||||||||||||||||||
|
Ecosystem
|
|||||||||||||||||||||||||||||||||||||||||
|
Number of integrations
|
30+ | 12 | |||||||||||||||||||||||||||||||||||||||
|
Expert Resources
|
|||||||||||||||||||||||||||||||||||||||||
|
Communications templates
|
– | ||||||||||||||||||||||||||||||||||||||||
|
Program RACI examples
|
– | ||||||||||||||||||||||||||||||||||||||||
|
Dedicated CSM
|
– | ||||||||||||||||||||||||||||||||||||||||
“Relying on content inspection and classification is a losing game.”
As a mechanical contractor, McDonald Miller has a ton of unstructured data including 3D files and engineering schematics. Eddie Anderson, their security & IT manager, believes Code42’s approach to blocking works best because it doesn’t rely on content inspection and classification.
Connect With Sales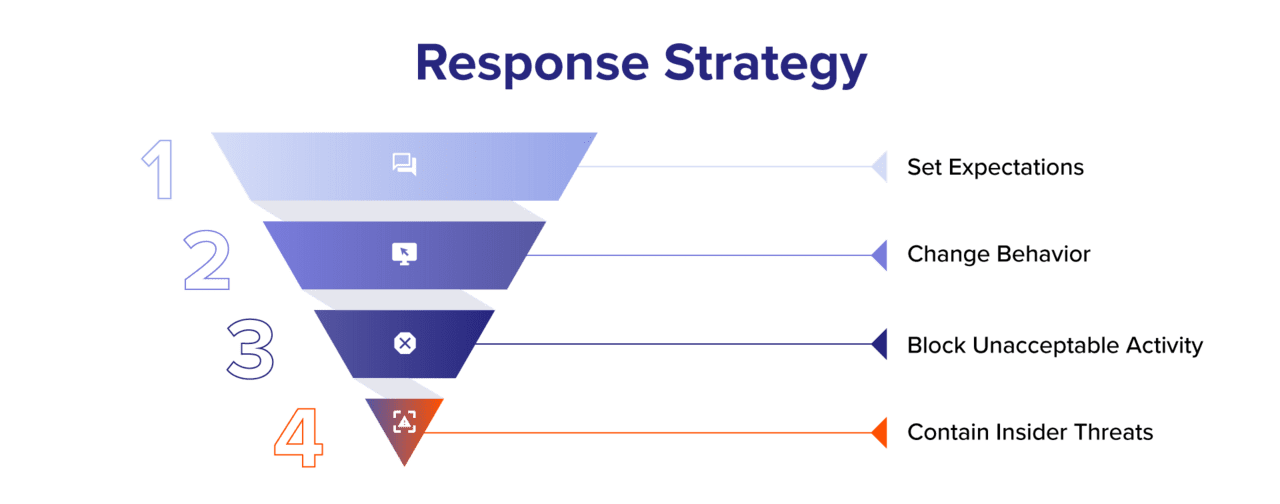
Don’t Just Take Our Word
Our 65 Gartner reviews speak for themselves
That’s 27 more than Proofpoint has.
Read Customer Reviews