As corporate adoption of cloud-based collaboration tools continues to increase, security teams are running into new challenges to keep data secure and false positive alerts down.
One of these challenges: when sanctioned business applications have a consumer offering, which is becoming more of the norm. Google Drive is one of the most prevalent examples as a solution commonly used in both enterprise and consumer markets. How can security teams differentiate between files being uploaded and shared to their trusted corporate Google Drive environment vs an employee’s personal drive account?
Domain-based methods don’t work
Browser uploads to Google Drive register as drive.google.com traffic regardless of whether the account destination is enterprise or personal. So how are security teams managing this challenge today, and how concerned are they that files could be exfiltrated under the radar?
To get to the bottom of this, we worked with Pulse Research to survey security leaders throughout the United States. We heard from 100 security leaders, 91 of whom were a Director title or above. Most work at mid-to-large enterprises, with over 21% of respondents from organizations with 5,001-10,000+ employees and nearly half from 10,000+ employee organizations.
Here’s a quick look at the results.
91% of security leaders agree users may be exfiltrating data via personal accounts like Google Drive.
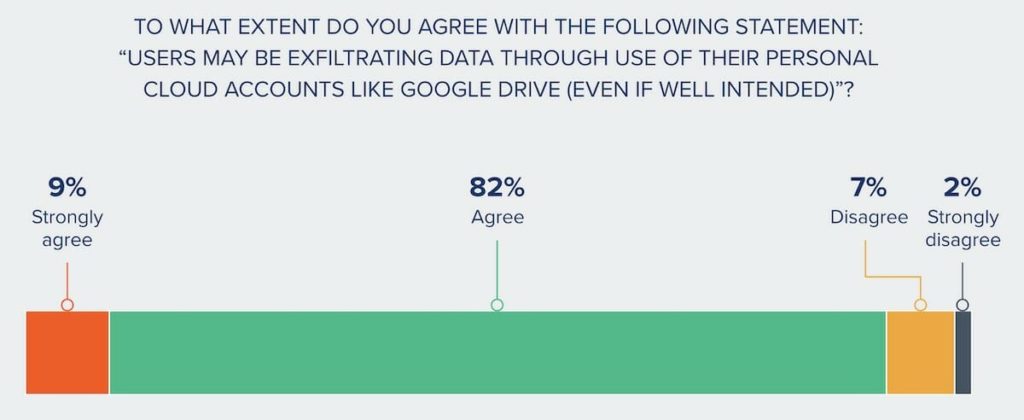
With results like these, clearly security leaders are aware that cloud tools are a breeding ground for insider data leak and theft – be it malicious or negligent. It’s also known these activities can result in real damage – like loss of up to 20% revenue annually. Admitting the problem is half the battle. So with so many security leaders readily in agreement, why has more not been done to address this risk?
It looks like the issue comes down to technology.
Nearly ½ of security leaders don’t have a tool to differentiate personal vs corporate Google Drive uploads.
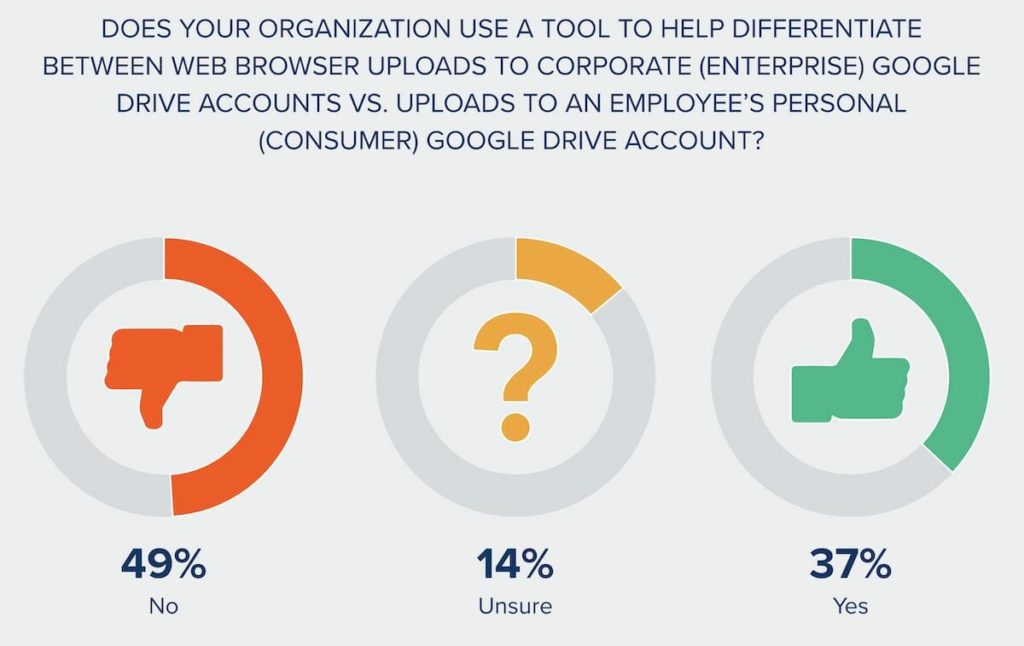
Without a practical solution, the problem continues unchecked.
The 37% of respondents who indicated they have a way to pinpoint unsanctioned, personal activity are only able to do so through a lot of manual effort–and not a lot of enforcement. Common ways to gain visibility include custom solutions and manual audits in Google.
It’s time security teams have a new method at their disposal. Code42 Incydr detects and alerts to file exfiltration via personal accounts (such as Google Drive and Box) without admin configuration, changes to network infrastructure, or rigid policy maintenance. This means administrators are never bogged down by alerts on trusted activity. This frees them up to quickly respond when untrusted file movement takes place.
Goodbye noise, hello signal
Interested to see how it works? Contact us for a demo to see how Incydr allows you to contain, resolve and reduce potential Insider Risks in your organization.
