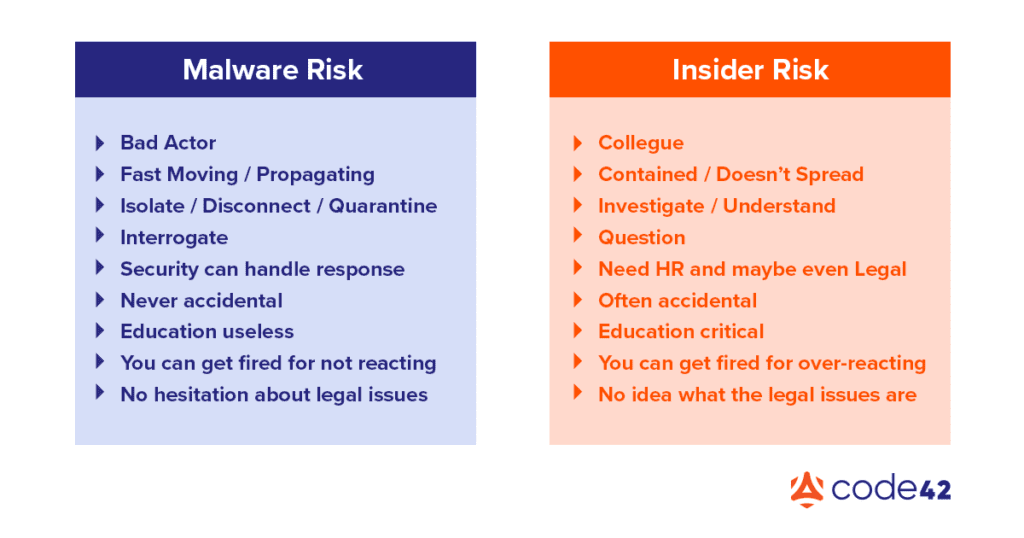
First things first, dealing with risks presented by internal users requires a different approach than those from external threats. While this likely isn’t news to some of you, it does need to continue to be said, as this reality unfortunately has yet to be widely accepted by the security industry. It’s still far too familiar to see the cudgels common to blue teams everywhere wielded against internal users who run afoul of security. And frankly who can blame overworked security teams – dealing with internal folks is way more fraught with challenges – it’s far simpler to triage all risks with the same tools and techniques at our disposal for external threats.
But it’s 2022, and it’s long past time we strove for something better. Let’s reconsider how we conduct ourselves when dealing with people inside the wire. I know, I know, no one relishes the thought of standing up separate processes and procedures just for insiders, but our reputation as security professionals and the reputation of our security programs is at stake as we respond to these insider risks. And really, our goals aren’t wholly different from those we have when dealing with external threats. We still need to “stop the threat” but HOW we go about that is paramount when dealing with insiders; reaching for tried and true technical responses (locking down an endpoint for example) can be far too punitive when applied to your coworkers.
To this end I’m proposing a shift in the analyst’s mindset when handling risks presented by insiders. Below we’ll discuss a few areas we must attend to in order to get our heads screwed on straight and make ourselves and our programs more effective at dealing with these risks.
Asking the Big Question
The biggest change I see, which requires the reordering of priorities when dealing with internal risks, is the vast importance of “why”. When it comes to external threats the “why” is either less relevant or perfectly evident (it’s not rocket surgery to understand why a criminal wants credit card data). But why an internal user took an action – why they shared that folder full of data with an external email address – means all the difference in our response to that action.
- Was it an innocent mistake by a user in their first weeks with the company, requiring training and support?
- Or was it someone bending the rules in order to get business done, requiring a reevaluation of standards and policies?
- Or did that user know better and went ahead and sent that customer list to themselves anyway, requiring corrective action or even review of that user’s employment status?
As with all things, how you go about getting to that “why” is going to make all the difference.
In Pursuit of Why
Now that we’re clear on where we’re going, we’ve got another mindset shift to make – from assuming guilt (servers don’t get “accidentally” accessed from Russia), to presuming the positive intent of your coworker. Note that I said presume, NOT assume. Presumption is based on probabilities, there is a reason that this person works for your company, they were hired out of a pool of other qualified candidates and imbued with access to company systems and data in order to perform a specific, necessary function. Especially in this job market, there is very little reason for an unhappy employee to hang onto a job which makes them miserable, so as we deal with insiders let’s make an effort to approach situations presuming that that user had a good reason for doing what they did. Now this doesn’t mean we give folks carte blanche with company data, just that we don’t ascribe malintent without evidence. For more on finding the “why” check out this post.
A Word on Security Programs and End User Relations
As we’ve established, it’s more than likely that you’ll end up needing to talk to a real live human being in order to better understand their actions. A major factor in how these interactions with end users will go is determined by the goals of your specific security program and how the program is perceived internally (I’m generalizing here so if your specific IRM program isn’t housed under security, transpose “security” as needed).
If you are anything like me you’ve had your share of groans while dispatching your duties as a security professional. In general security is not usually thought of as a “friend”, and most often it’s seen as an “impediment to progress”. More disturbingly this status quo appears to be just fine with many security professionals. I suppose I can understand the instinct – who cares what Phil from Finance thinks if we only concern ourselves with external threats, but this is really no longer an option.
The effective handling of insider risks requires if not the partnership, at least the participation of every person at your organization. It’s also critical that an insider risk program has the support and backing of key stakeholders around the organization, such as Human Resources, Legal, the larger Security team, and most importantly Leadership. These partners help set the tone for an IRM program and provide the backing and legitimacy that is required to be successful.
As with any customer-facing role (at the end of the day the business is our customer) doing this requires more than a little grace – but I’ve been to the mountaintop, I’m here to tell you it’s worth the investment. Making friends by being available and helpful wherever and whenever you can is one of the most impactful things you can do to increase the effectiveness of your insider risk program. If you can set folks at ease during your routine interactions and answer inquiries with honesty you’ll go a long way to make folks comfortable, and when people are comfortable you’ve got a better chance that they will come to you with problems rather than the other way around.
Human Motivation, or How Empathy Increases Effectiveness
While it may feel far-fetched, we as Insider Risk Management analysts are most effective when we appreciate the full range of potential motivations which drive people. Everything from discontentment at being passed over for a promotion, disagreement with company leadership, familial factors (divorce, illness of a family member), financial struggles (debts, gambling, etc.), compromise by foreign powers, desire for personal gain/glory, etc. the list goes on. I bring all this up to say that while it may just be another Tuesday for you, the stakes may be life-altering for the subjects of our scrutiny, and I believe that it is our duty to wield this responsibility with as much compassion and empathy as possible. The HOW we do something is equally as important as WHAT we do.
Our duty is to the facts, and to the goals of our security program. We are counted on to deliver clarity and uncover risks to the organization, not to sit in judgment of others. We may not know every person in our organization by name, but in our capacity as insider risk analysts they are entrusted to our care. Misattribution of events or misappropriation of facts could cost someone their reputation or even their career. This is why I say that we must have empathy. Attempting to shut our eyes to the motley grayscale of human motivation and remain purely logical when dealing with people can only lead us to overlook crucial factors.
Join us next week for part 2 where we’ll dig into the details of how to conduct investigations of an insider while maintaining the mindset we discussed above.
Get in Touch
Learn more about how you can build a successful IRM program with Code42 or contact us today to talk to an Insider Risk expert.
