See & Stop Data Loss With Incydr™
Stop guessing where your data is going. Let Code42 Incydr do the hard work to see and stop data leaks from employees – all in one platform.
Connect With SalesThe Incydr Solution
Secure collaboration without burdening your security team
Visibility when critical IP leaves your organization
Contain data leaks without disrupting employees
Less work for you and less complaints from users
Learn How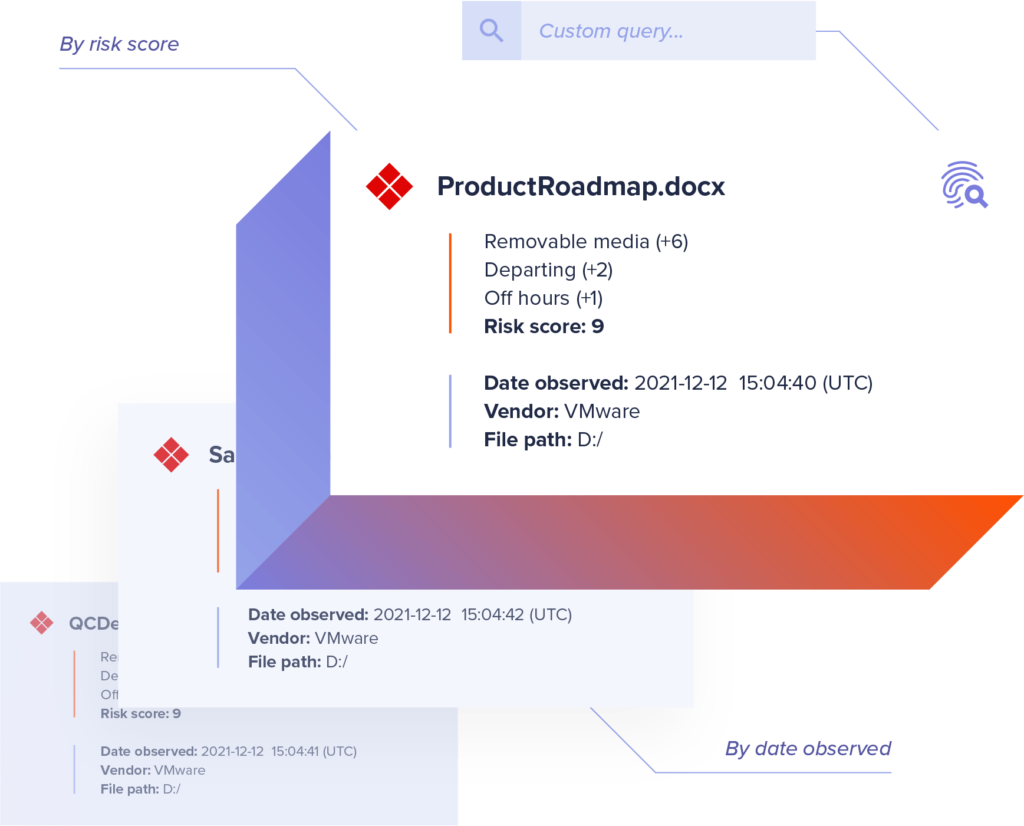
Connect With Sales
Don’t be the next company to hit headlines for a data breach.
An Incydr customer detected $5 million worth of source code exfiltrated by a departing employee and quickly responded before major damage was done. Can you put a price tag on your company’s IP?
INTEGRATIONS
Incydr plays well with your existing tech stack
90% of companies use a combination of DLP, CASB, UEBA or IRM to stop data exfiltration. Consolidate your data protection tech with Code42 Incydr and integrate seamlessly with your remaining tech.
View All IntegrationsDon’t Just Take Our Word
“Great solution to a difficult problem.”
Read why our customers stand by using Incydr for data protection on Gartner Peer Insights.
Read Reviews