Mergers & Acquisitions
Put A Stop To Data Leaks During M&A
During M&A, the risk of data leak increases as companies merge their people and systems. Code42 Incydr provides complete visibility into data activity during critical times of transition.

The Problem
The hidden data risks during M&A are on the inside
When it comes to M&A transitions, there’s a lot at stake. One crucial aspect is safeguarding your data and ensuring it stays where it belongs. It’s not just external cybersecurity threats that you need to be mindful of; many security issues arise from within the company itself. Some of the common vulnerabilities that put your data at risk include:
Undisclosed data breaches
Historic or undisclosed data breaches may surface and damage the brand.
Merging systems
IT teams can overlook issues when combined with another organization’s systems.
IP theft
Employees can leak sensitive data regarding the M&A prior to the announcement.
The Solution
See & stop unauthorized data exfiltrations before it’s too late
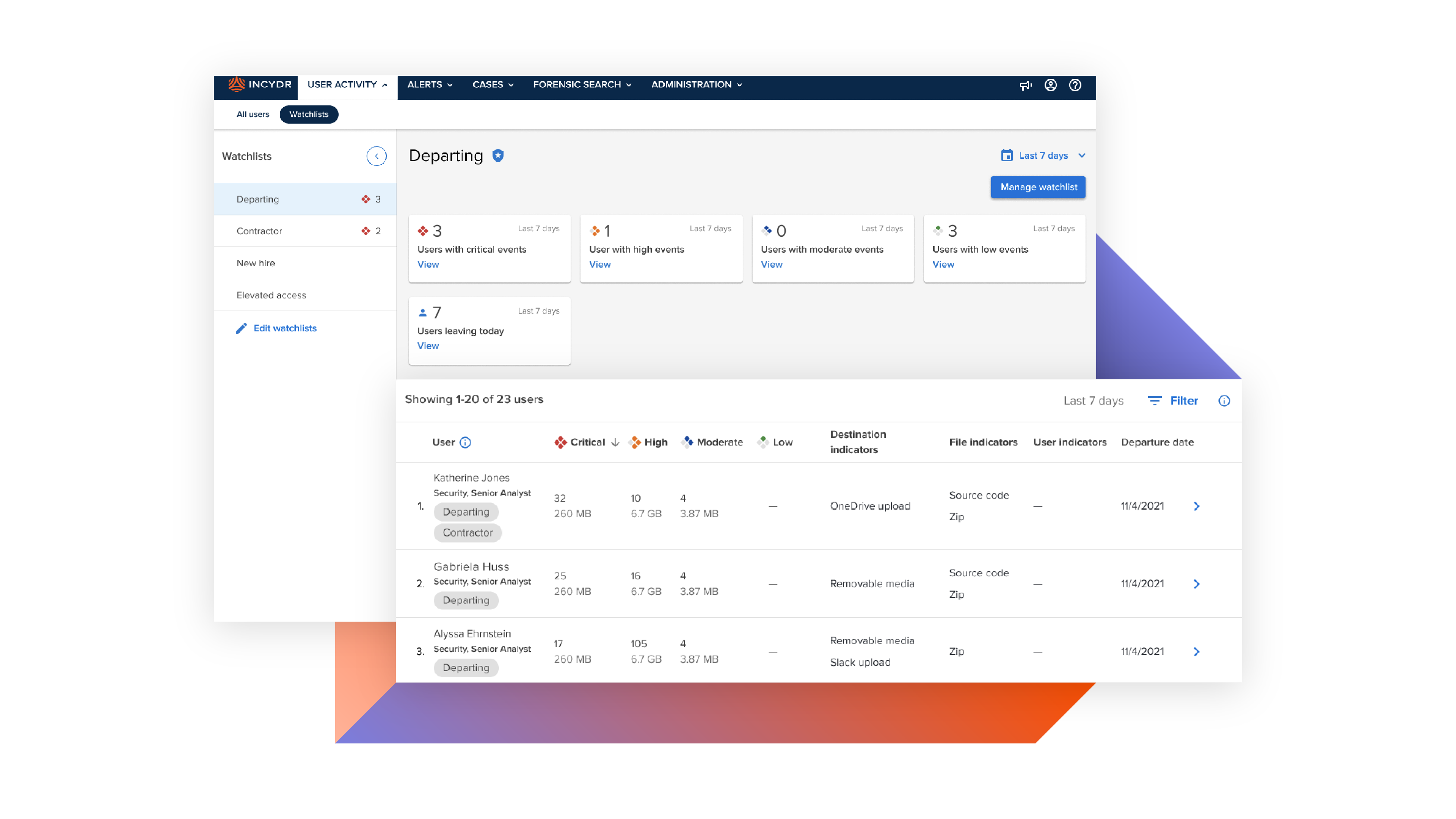
With Code42 Incydr, you gain complete visibility over your data including Salesforce downloads, Airdrops, Git pushes, cloud syncs & more. From day 1, Incydr intelligently differentiates low-risk activities from potential data leaks that require investigation. Armed with a wide range of response controls, you can quickly contain threats or even block data exfiltrations altogether.

Incydr is built to protect M&A data risks
What makes Incydr stand out?
Deploy Incydr in only a few days to quickly provide visibility into data leaks for the sell-side company
Automatically categorize data like source code, customer lists and other IP that requires special attention – without time-consuming data classification
Validate the actual content of exfiltrated files for full understanding of their level of sensitivity
Stop unacceptable exfiltrations with real-time blocking capabilities
Can you put a price tag on your company’s IP?
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before major damage is done.
Connect With Sales$9M
worth of deleted files helped disprove lawsuit accusations – thanks to Incydr.
High Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn MoreIP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreReorganizations
The logistical challenges of reorganizations can lead to security gaps that increase the risk of data exfiltration going undetected.
Learn More