departing employees
Don’t Let Data Leave With Departing Employees
When employees leave your organization, there is a 1 in 3 chance they take IP with them. The question is, do you see it and can you stop it?
Code42 Incydr™ is the best solution to help offboard employees with ease by delivering complete visibility and effective response controls to stop employee data theft.

The Problem
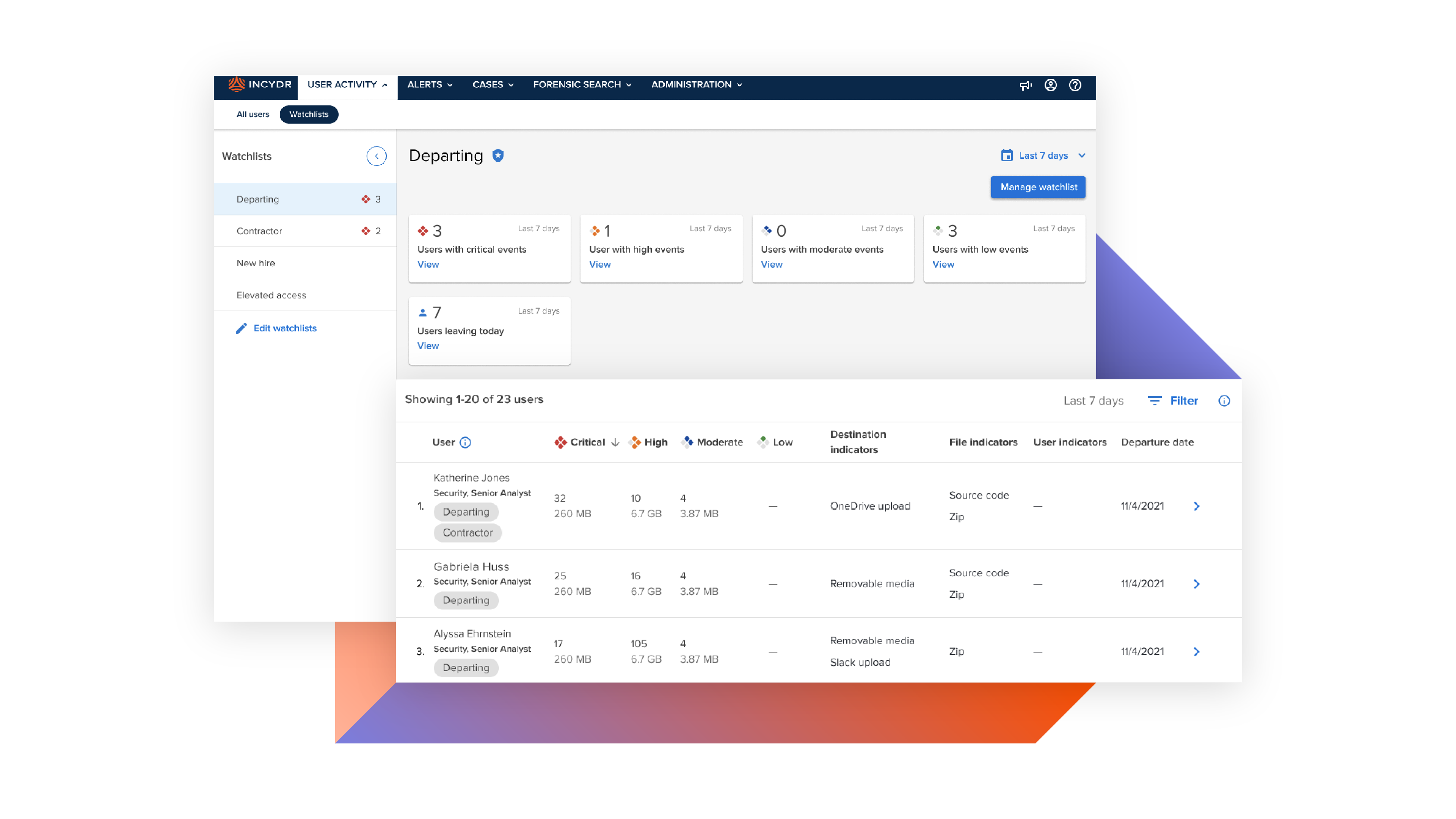
Departing employees are walking away with your most valuable IP
Whether malicious or because they feel ownership over their work, employees are leaving the business with customer lists, research data, source code and more – and that has serious implications.
The Solution
See and stop data theft before employees walk out the door
Code42 Incydr can see all the ways IP moves out of the organization from departing employees. From day 1, it automatically differentiates low-risk events from real departing employee threats. And with Incydr’s wide range of response controls, you can quickly contain the threat – or outright block their attempt of exfiltration.
Built to protect departing employee data theft
What makes Incydr stand out?
Visibility into cloud and endpoint exfiltration in one solution including Git push/pull activity, Salesforce downloads, Airdrops and cloud syncs
Integrate directly with HR tools to automatically revoke permissions – without even bothering HR
Validate actual file contents to know for sure how sensitive the data the is
Implement real-time blocking for departing employees
$$$$ just got real. Data leaks from insiders happen daily.
Don’t be the next company to hit headlines for a data breach. Our customers remediate massive insider incidents before damage is done.
Connect With Sales$5M
worth of source code exfiltrated by a departing employee – detected by Incydr.
Contractors
As temporary members of the organization, contractors present a heightened risk for data theft. Monitor files access and flag unusual or unauthorized activity.
Learn MoreIP Theft
76% of companies have experienced IP loss. Stop your crown jewels from being stolen.
Learn MoreHigh Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn More