Insider Threat
Don’t Let Insiders Compromise Your Data
Companies continue to reap the benefits of digitization and cloud adoption, but still face a growing danger: insider threats. In today’s modern workforce, how do you cultivate a secure environment without creating negative tension between security and employees?
Connect With Sales
Today’s Problem
Data has never been more vulnerable to employee leak and theft
Digital change is happening much faster than security teams can update policies. As data volumes grow and files become easier to access and share, the risks of data exfiltration by insiders are harder to monitor and protect than ever.
Code42’s Solution
Insider threat detection and response made easy
Code42’s security solutions for insider threats offer a new approach to data security. Incydr™ does the monitoring & detection for you – so you can focus on tackling only the most critical risks. And when it’s time to respond, you can contain insider threats while still fostering a positive work environment for other employees.
Say goodbye to data blind spots from insider threats
Relying on classifying data and blocking slows down the business – and still leaves you with gaps in data visibility. Incydr is the most comprehensive solution to monitor cloud and endpoint exfiltrations all-in-one – that includes Git pushes, Salesforce downloads, Airdrops, ChatGPT, cloud syncs & more. It filters out the noise of harmless data movement to trusted domains so you can focus only on the riskiest insider threats.
What Is Insider Threat Detection?

Not all insider incidents should be treated equally
You can’t always tell bad actors inside your organization apart from distracted or careless employees making mistakes. Risk is nuanced, and therefore, there’s not one type of response. With Incydr, you will tailor your response to the offender and offense. You can correct, block and contain to reduce overall risk and decrease the number of events you have to manage.
What Does Effective Response Look Like?Stop insider threats without getting in the way of business
Traditional solutions for managing insider threat often put security professionals at odds with the business. These dated solutions don’t always integrate with existing tech stacks, or use heavy agents that slow down business. Even worse – they simply don’t have a response for what to do next once an actual threat is detected.
With Incydr, you can remove all these roadblocks and keep business moving. And with integrated security education, you will build a culture of security while decreasing low-risk events for your team.
Code42's Responsive Security Education
Technology INTEGRATIONS
Incydr executes insider threat response with your existing security stack
Insider threats are multifaceted – and there are additional security tools that will help address it. Incydr has a robust ecosystem of integrations to ensure you can respond appropriately, every time.
Want to see Incydr from the inside?
In under four minutes, our product demo shows how Incydr can see and stop data leaks – before major damage is done.
Watch Demo Now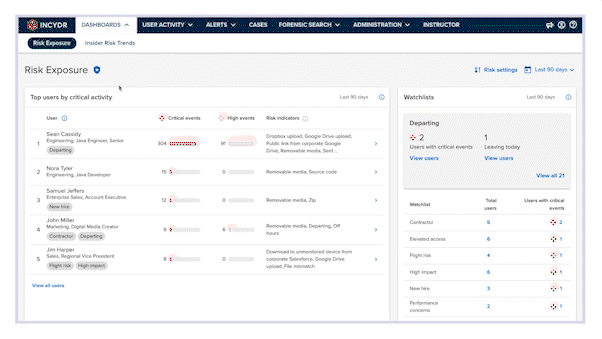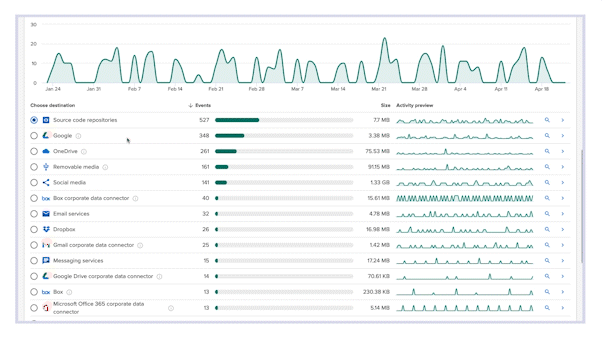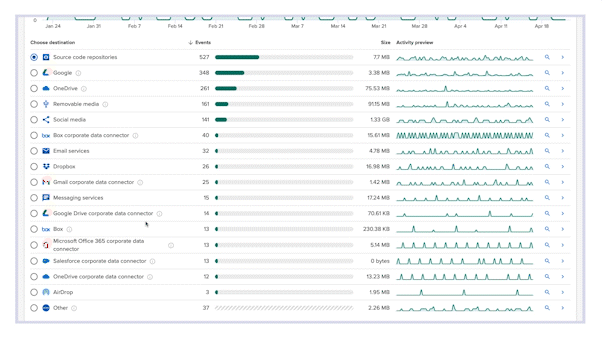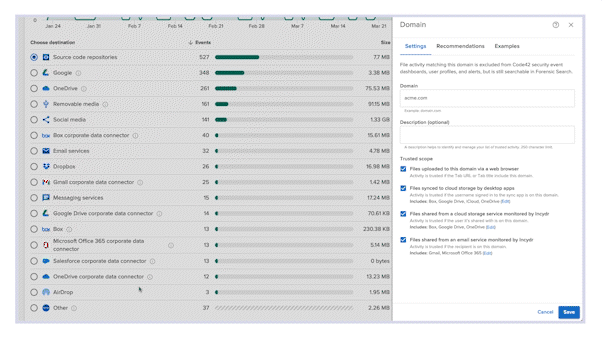
Departing Employees
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
Learn MoreRepeat Offenders
Behind every data risk event is an employee who likely didn’t follow the rules. Stop data exfiltrations from users who continue to violate security policies.
Learn MoreHigh Risk Employees
Programmatically protect data by monitoring flight risks and other high risk employee types.
Learn More