Incydr Risk Indicators
Automatically Prioritize Risks That Need Immediate Attention
Connect With Sales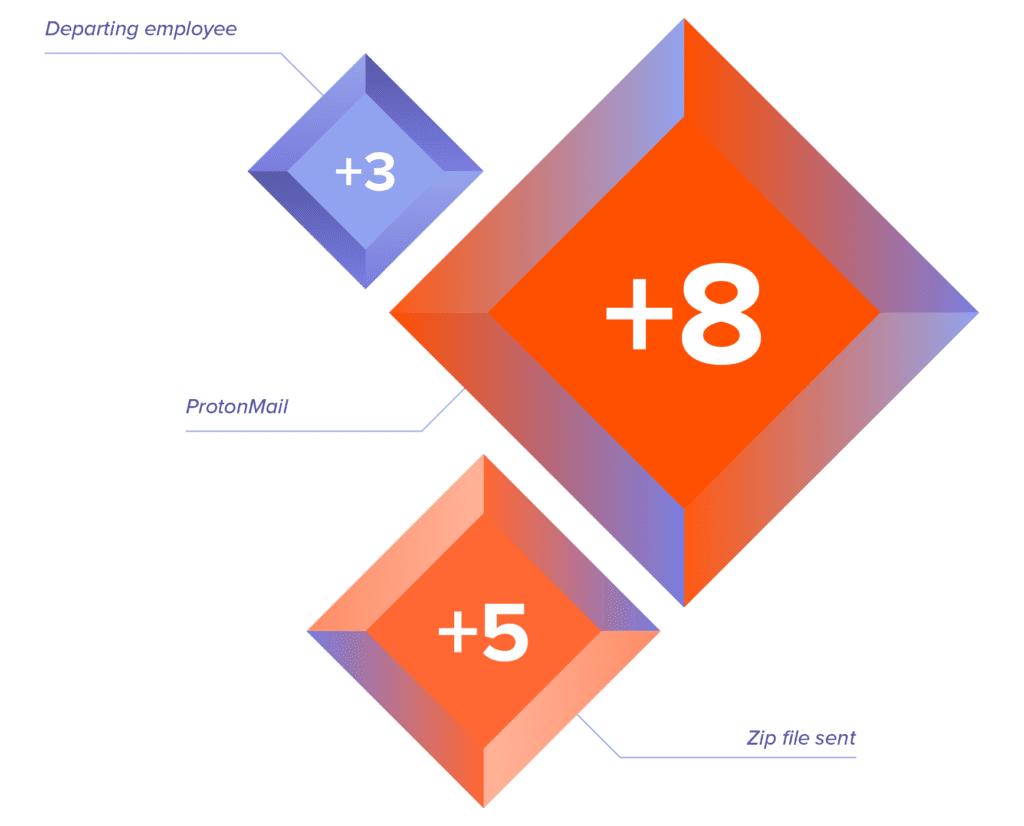
Watch A Demo
Incydr Risk Indicators (IRIs) are activities or characteristics that suggest corporate data is at a higher risk of exposure or exfiltration. A library of more than 250 IRIs drive Incydr’s context-driven, pragmatic and adaptable risk prioritization model.
How it works
Risk scoring based on file, destination, source and user characteristics and behaviors
- Apply multi-dimensional context
Information related to the file, source, exfiltration destination and user is used contextually to determine the risk of an activity.
- Detect anomalous user behavior
Pinpoint deviations from baseline user behaviors such as the first use of a destination, and rare use of a destination.
- Expertly scored on day 1
A research-backed risk score is assigned to every IRI out of the box, and score thresholds determine an event’s severity.
- Adjust to changing risk tolerance
Risk settings can easily be tuned to increase or decrease the risk score of an IRI based on your unique risk tolerance.
Incydr Risk Indicators examples
Files
Zip file exfiltration
Source code exfiltration
Salesforce report exfiltration
Earnings report exfiltration
Destination
Public link in Google Drive
Dropbox sync app
Attachment to ProtonMail
Airdrop transfer
Source
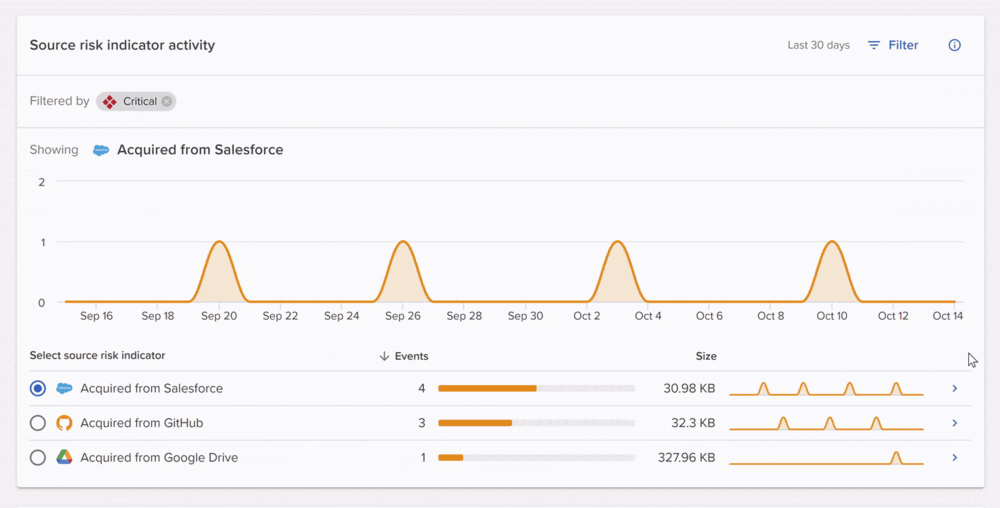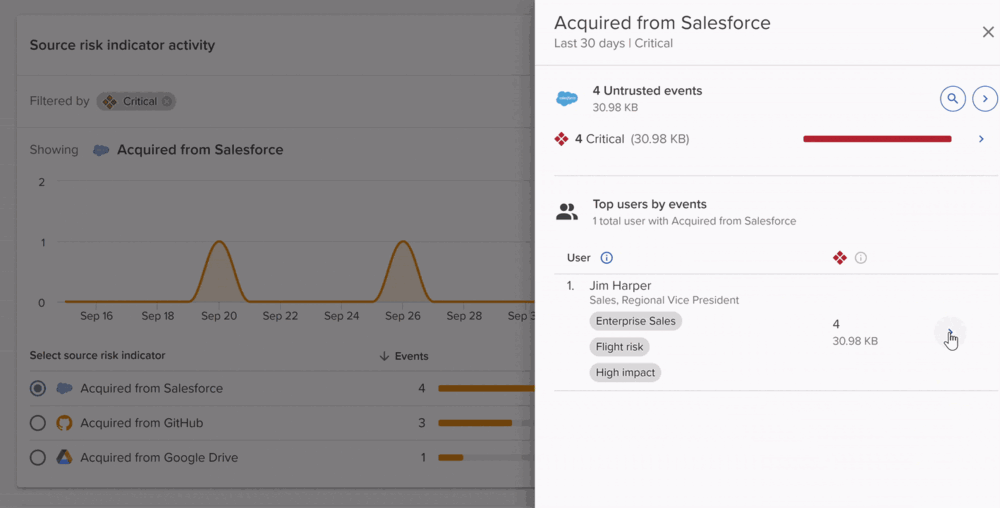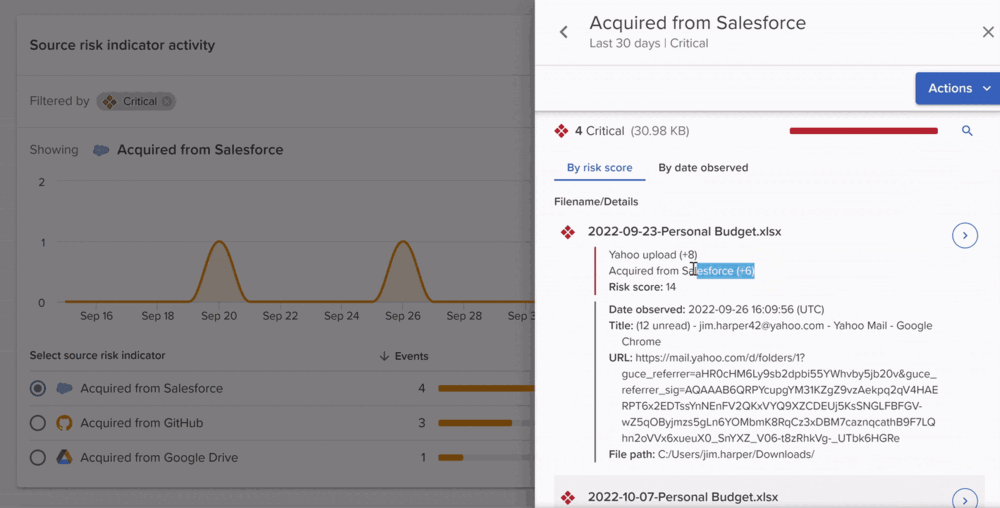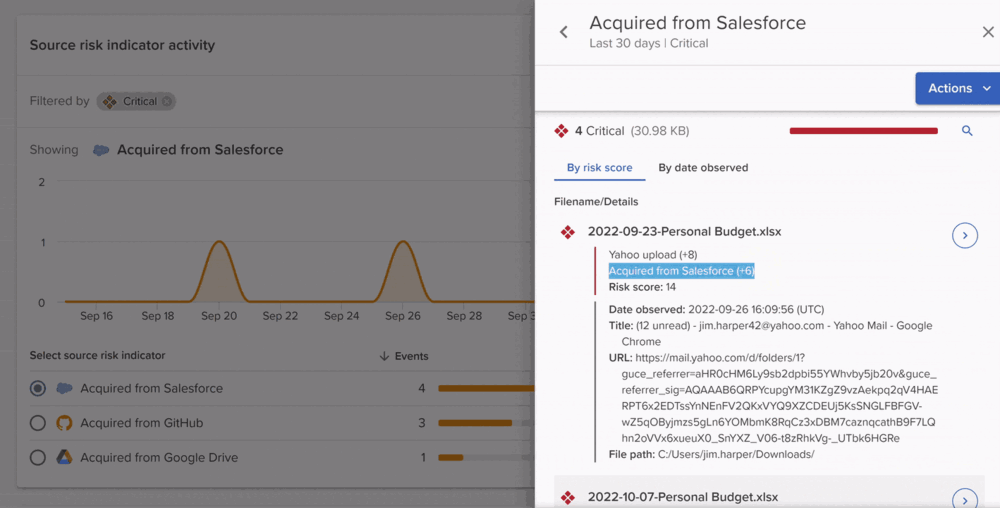
CRMs such as Salesforce
HR platforms such as ADP
Source code repositories such as Github
EMRs such as Epic
Users
Departing employee
Contract employee
First use of destination
File mismatch (concealed exfiltration)
Want to see Incydr Risk Indicators in action?
Get a tour of how Incydr Risk Indicators make it easy to detect and investigate data loss from insiders.
Connect With Sales
Watchlists
Automate management workflows and get focused visibility into file activity for a subset of users who are more likely to put data at risk, such as departing employees.
Learn MoreForensic Search
Investigate event details and custom query a comprehensive, cloud-based index of activity metadata without putting strain on employee devices.
Learn MoreResponse Controls
Implement effective, automated responses to protect data without disrupting productivity or burdening security teams.
Learn More
Incydr customers experienced benefits of $2 million over three years
According to the composite organization in Forrester TEI™ results.
Download Study