During this ongoing great resignation era, companies are dealing with a high volume of departing employees. Its impact is recognized by organizations looking to protect their IP and other sensitive data like never before. Examples abound of amplified cyber security challenges, specifically exposure and exfiltration of sensitive intellectual property. In fact, there is a one in three (37%) chance your company loses IP when an employee quits.
But if there are departing employees, it means that new talent is also actively joining. New employees are not used to your company’s security practices or tools, making them more likely to put data at risk through mistakes and negligence. Providing an appropriate onboarding process and ensuring proper data governance right off the bat is integral to the success of your company and those who recently joined your team. But even with that, sometimes having the right and immediate response controls in place can avert a company’s reputational crisis.
Laser-focused, one-click response to data exfiltration
At Code42, we solve a complicated problem that’s ever-changing. It’s especially urgent right now with employee turnover on the rise, many businesses are operating remotely, end-user Shadow IT is continuously growing as employees increasingly use new cloud applications every day. To keep pace with the rapid change, we need to continuously innovate and deliver new features and capabilities to our customers to effectively protect their valuable data.
That’s why we are announcing an additional way to better manage the risk of your continuously shifting workforce – Incydr’s new employee watchlist.
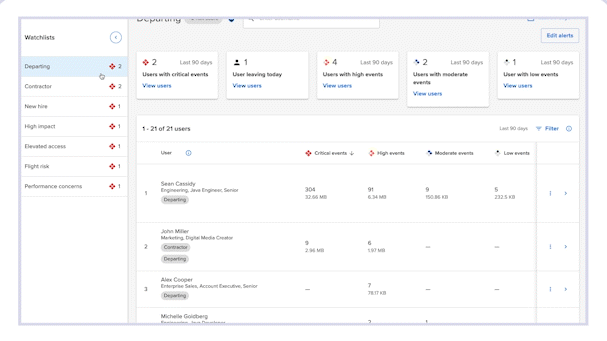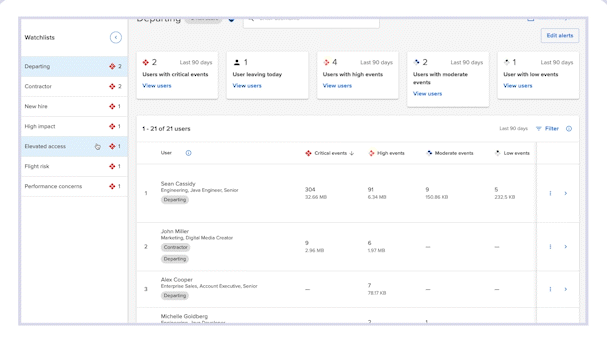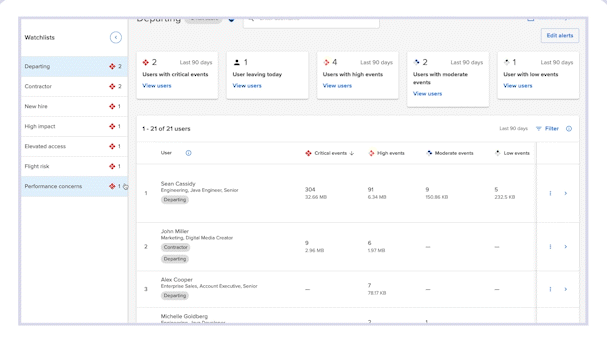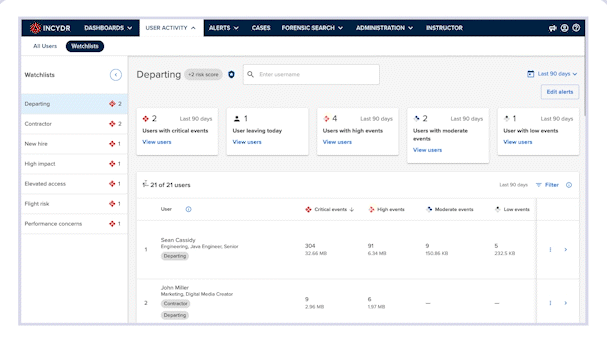
It allows your security team to gain visibility into how newly onboarded employees handle corporate data, helping you identify risky behavior before it’s too late.
Considering that data moves with lightning speed, an analyst’s response to a potential data exfiltration event is critical. Security process automation removes some of the workload. But the problem is, responding to a suspicious data event sometimes can not be fully automated. Some responses are too obstructive. Others may require an understanding of intent. That’s why it’s important that a security analyst be able to make the decision to manually initiate a response control.
To help security analysts choose the right-sized response to Insider Risk, we have added new actions to initiate Incydr Flows from within the console.
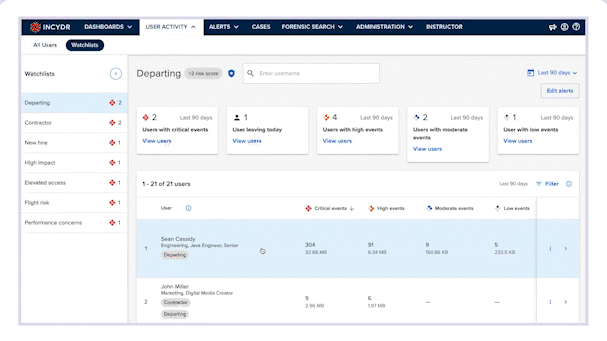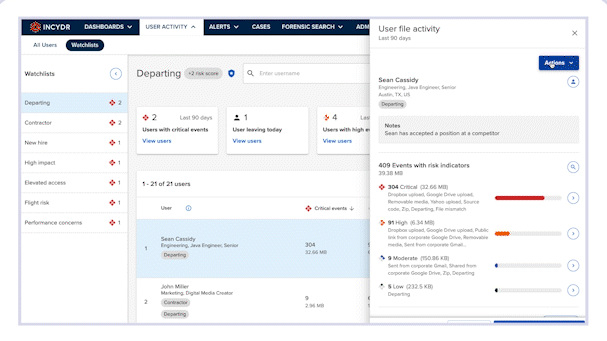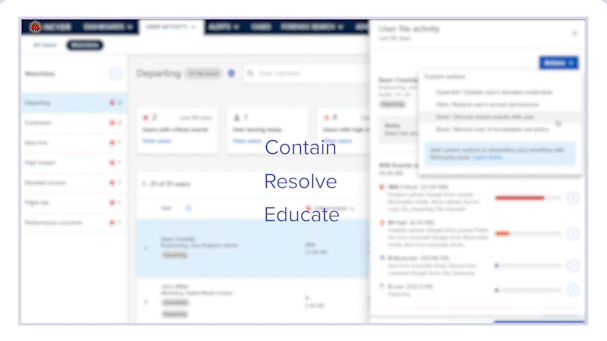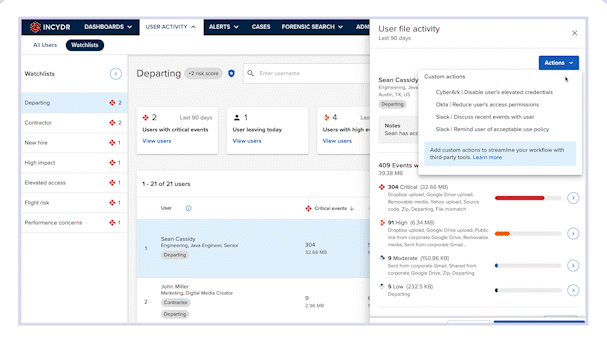
Our newest one-click Insider Risk response is now available within the product interface, offering the ability to initiate Incydr Flow response controls to potential exfiltration events. This feature provides an integrated experience and an even faster time to respond to a potential exfiltration event.
When investigating risky activity, whether in response to an alert or ad-hoc investigation, analysts can navigate to the user’s profile to get a full picture of the user and their activity. Once there, they will click on the Actions button, located at the top right corner of the screen. A drop-down list of actions will appear.
These actions can be customized based on the Incydr Flows an organization purchases.
Here’s an example of how such a workflow can be set up with Slack.
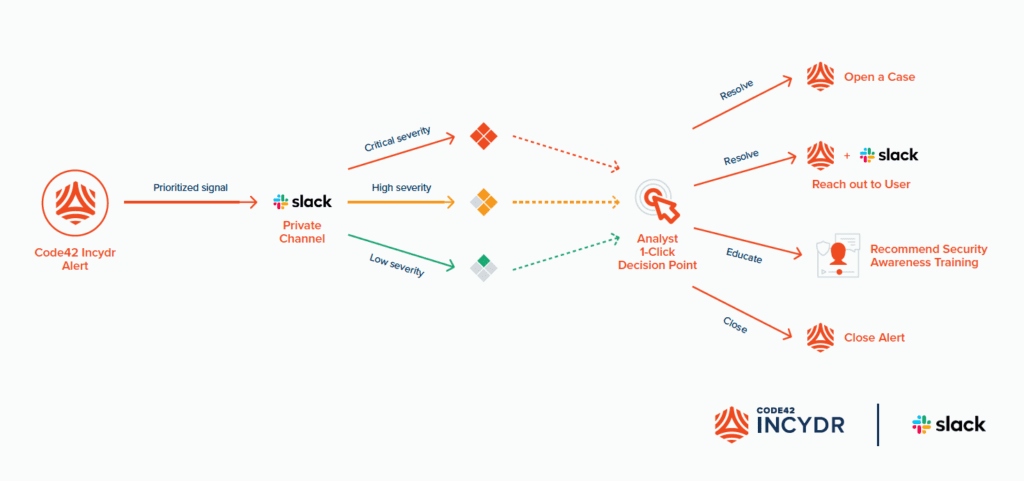
In as little as one click in Slack, the analyst can:
- Close out the alert in Incydr
- Trigger a response controls like
- Use a template to auto-populate a message to reach out to the employee via Slack to gather more information
- Recommend security awareness training
- Open a case in Incydr for deeper investigation
When confirming a specific action, you’ll see a confirmation message appear on your screen indicating that the response was successful.
Gain visibility and control over data leaks caused by new employees
As an Insider Risk Management (IRM) technology, Code42 Incydr’s approach is about providing visibility, context, and a wide range of controls. During the great resignation, this is critical in both departing employee use cases and now through new employee onboarding as well.
Insider Risk takes different forms. Each situation is unique based on the combination of who did what, the type of data in question, and where it went. A one-size-fits-all response is an impossible notion, but that doesn’t mean that responding to data loss events needs to be complicated. That’s why Code42 advocates for the need to take a right-sized response to Insider Risk events.
Incydr’s Approach
Respond confidently to data theft before damage is done
Incydr, a data protection solution, allows security teams to detect data theft by monitoring cloud & endpoint exfiltration, and accurately tailor responses to each offense. Let’s work together to protect IP without disrupting users or causing more work for your security team.
Discover Incydr