In this installment of the Incydr Scoop, we share some surprising statistics about what employees are doing with corporate data. This is the third installment of the Incydr Scoop. The previous Scoop findings touched on How to Recognize & Prioritize Insider Risk Signals and Quantifying & elevating Insider Risk signals through Incydr product telemetry data. Now, I am not about to assume you have read all of our material on Insider Risk, so first some background context. Incidentally, “context” is what is needed most to manage and mitigate Insider Risk, so there’s no better place to start.
What is Insider Risk?
Code42 defines Insider Risk as “the data exposure, exfiltration and threat of breach that are a natural result of how employees work.” Employees are innovating, collaborating and creating new digital assets every minute of every day and with it introducing data risks largely unseen by legacy security tools and technology.
What does Insider Risk look like?
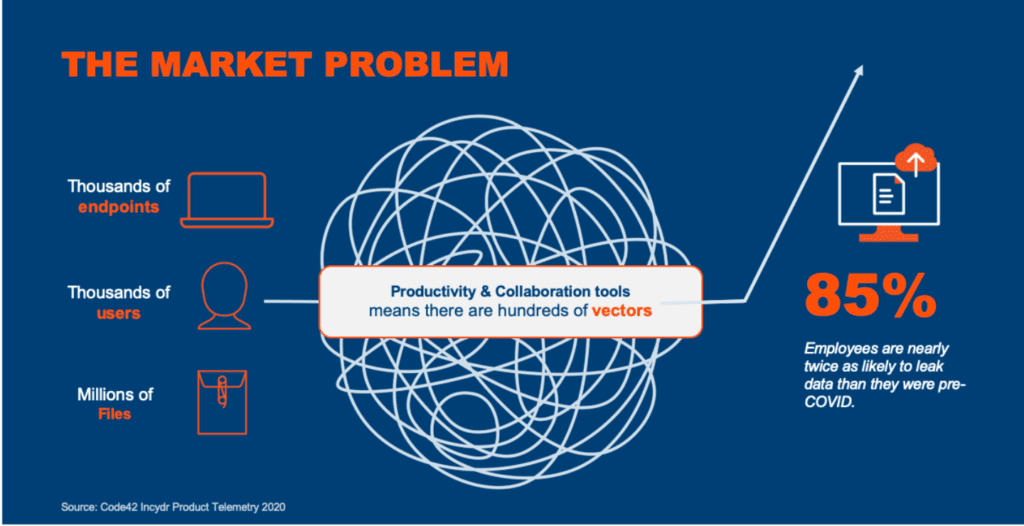
Insider Risk — how employees work — has long been a concern of CISOs. Code42’s 2019 Data Exposure Report study found that 89% of CISOs believe the very nature of how employees work puts the organization at greater risk of a data breach. They were right! Our 2021 Data Exposure Report found that employees are nearly twice as likely to leak data today than they were pre-COVID. To make matters worse, a remote hybrid workforce has rendered the perimeter obsolete meaning security teams now have thousands of users behind thousands of endpoints with access to millions of files to secure. Throw on top of that the hundreds of potential data exfiltration vectors in the form of cloud-based personal productivity and collaboration tools — both sanctioned and unsanctioned — that security must take into account. We end up with a mess of file, vector and user activity that renders organizations blind to Insider Risk.
What is Insider Risk Management (IRM)?
Insider Risk Management is designed to protect all data and users from everyday exfiltration risks — no matter the employee’s intent. We have a purpose at Code42 to secure the collaboration culture by never compromising the speed of innovation, nor the safety of data. Insider Risk Management (IRM) is the realization of that purpose. Unlike legacy approaches like data loss prevention (DLP), IRM takes a more pragmatic, dare I say, realistic approach. At its core, IRM is rooted in helping organizations identify where corporate data is exposed. With a better understanding of data exposure, security teams are more equipped to define data risk tolerance, prioritize data risk incidents and events and investigate those incidents to take a right-sized response. For more details on our approach, check out our overview: Insider Risk Management: A Better Way to Prevent Data Leaks. In a nutshell, IRM helps security teams better mitigate the data risks that come with how employees work without ever disrupting their productivity, i.e. blocking innovation, collaboration or creativity. To do this, security teams need the one thing they lack the most from tools like DLP: context.
Context is Queen, King, Everything
Now that we got the formalities of our definitions out of the way, let’s dive into the latest numbers — the context Incydr provides — starting with identifying where Insider Risk exposure exists and what changes in employee activity we are seeing. Below is a breakdown of data exposure events since our last report:
- Removable media made up 42% of data exposure events. This is down from 50% in our last Scoop
- Syncing files to cloud services dropped to 38% compared to 41% in our last Scoop
- Files uploaded via web browsers or apps grew from 6% of exposure events to 9%
- Open public file shares in the cloud is up significantly from 1% of exposure events to 7%
- Direct shares from corporate collaboration platforms to untrusted email domains more than doubled from 2% to 4.5% of all exposure events
Identifying where data is exposed is the first step in managing Insider Risk. The second is determining what activity is acceptable versus unacceptable. In other words, what risk to what types of files is tolerated and what isn’t. To better define risk tolerance, we analyze the types of files or file categories being exposed.
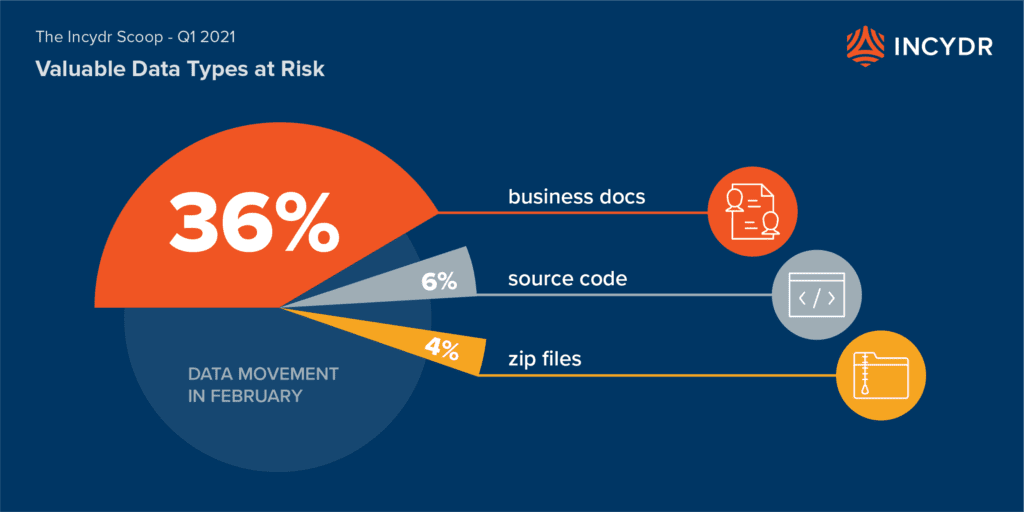
- 36% of files exposed were business documents – up slightly from 33% in our last Incydr Scoop
- 33% of files exposed were multimedia files (images, audio, video, etc.)
- 6% of files exposed were source code – up slightly from 5%
- 4% were zip files, which remained flat
- 21% were “other” indicating unique file categories that may be tied to specific applications
Risk tolerance will differ from one organization to the next. For example, we have customers that have zero risk tolerance for source code exposed via removable media. We have other customers that watch for Zip file creation and movement, and others that drill into specific business documents with the word “customer” in the filename. How a customer defines risk tolerance will dictate what alerts to prioritize. To help customers prioritize alters, we watch for Insider Risk Indicators.
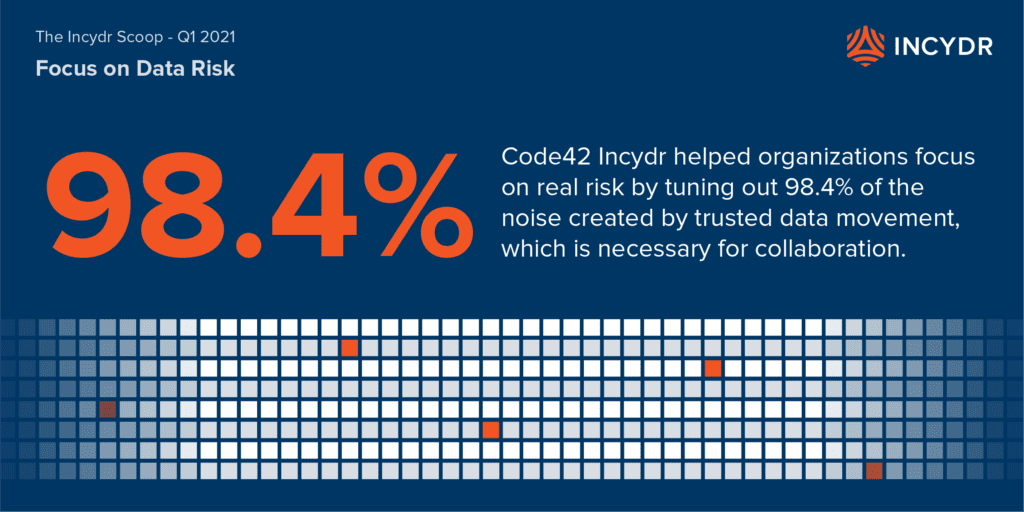
- The single biggest IRI is the use of untrusted domains. Of all of the Insider Risk exposure events occurring across all the different file categories, Incydr filtered out 98% of trusted activity to surface the 2% of the untrusted activity indicative of Insider Risk.
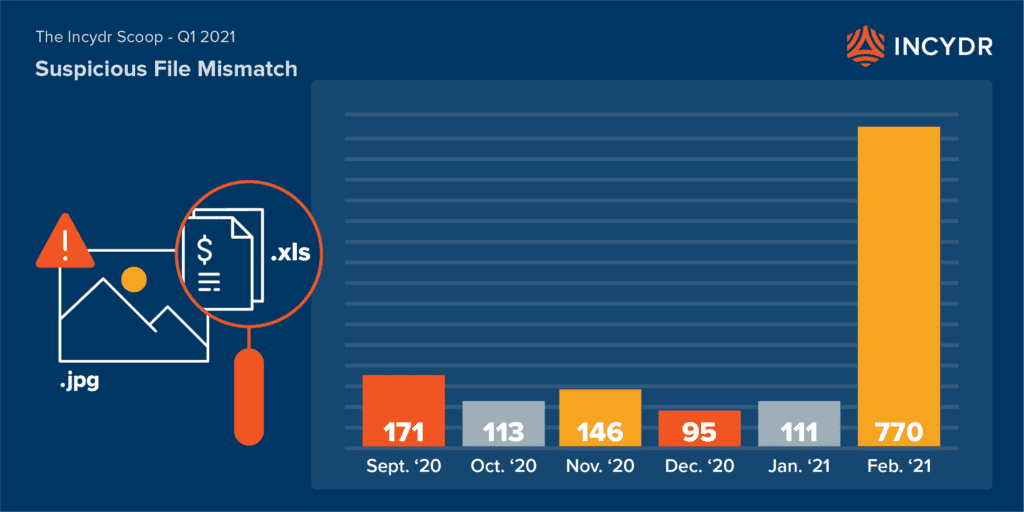
- There were 770 file-mismatch IRIs triggered in February alone, with 655 of them occurring on a single day! This is a staggering increase over previous months: 146 in November, 95 in December and 111 in January. File-mismatch events are indicative of users attempting to “hide their tracks” hence why they are a strong Insider Risk Indicator.
- Thursday, February 18, 2021 had the highest number of off-hours IRIs triggered since our last Scoop. Off-hours events accounted for 21% of all data exposure events that day. By comparison, November 23, 2020 was the last highest off-hours IRI day when off-hours accounted for 54% of all data exposure events.
In isolation, a spike in off-hours data exposure may not say much. But when customers are able to combine IRIs or sequence them together, they get a better picture — one with an extremely high level of true-positive Insider Risk. For example, an Incydr customer may have had an announcement of a pending restructuring, merger or acquisition throwing employees into a state of uncertainty. Perhaps following the announcement employees worked late into the night, changing file types and uploading them to personal cloud accounts. This is just an example to show the power of IRIs and what an Insider Risk Management approach can mean to security leaders and practitioners when it comes to protecting data.
At Code42, we practice what we preach. In fact, it’s our own security team’s IRM practice and use of Incydr that enables us to preach. Since helping define, develop and implement Incydr for Insider Risk Management at Code42, our security team has both empowered employee productivity and collaboration and reduced data risk. To learn more about how to get started with Insider Risk Management at your organization, check out our IRM resource hub.
