MACOM is truly a great place to work. But, like every
company, the unavoidable reality is that people leave. And, like every company,
we’re faced with the challenge of making sure our trade secrets — in our case,
highly proprietary semi-conductor designs and CAD drawings — don’t leave with
them. I am part of a three-person security team, and we are tasked with
overseeing around 1,500 employees spread across 50 sites worldwide. Today, I’d
like to share how we’re using Code42® Next-Gen Data Loss Protection to tackle
the challenge of data loss from departing employees — protecting our most
valuable files and protecting our business.
A Better Process for
Detecting, Investigating and Responding to Data Loss Risks
About a year ago, we chose to implement Code42’s solution as the foundation of our comprehensive data loss protection strategy. We’re leveraging the solution in a number of ways, but one of the simplest and most valuable use cases is detecting when departing employees put data at risk — and accelerating investigation and response to data loss incidents.
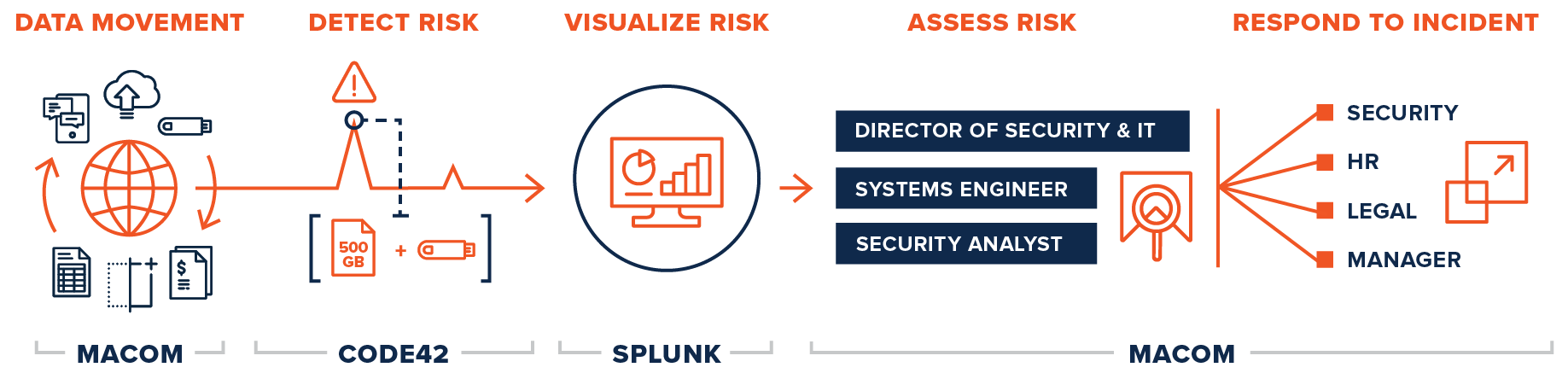
Here’s what a typical workflow looks like with departing
employees:
- HR
Notice: Our HR team understands how we’re trying to focus on the unique
data loss risk presented by departing employees. Having their buy-in ensures
that HR informs us as soon as an employee gives notice that they’re leaving the
company. This kick-starts the entire workflow. - Past
Activity Examined: As soon as we know an employee is leaving, we look back
at the last 90 days of their file activity to see if they’ve done anything
risky. - Employee
Added to Watchlist: Going forward, that employee is added to a watchlist
within Code42 for enhanced monitoring. We watch their file activity closely for
potentially risky data movement. - Activity
Alerts for File Movement: Code42 automatically generates activity
notifications when an employee on our watchlist exceeds our defined file
activity thresholds (moving too many files, moving too much data, moving files
in specific ways, etc.). - Forensic
Investigation: Once again, since we’re able to track all file activity over
the last 90 days, we’re able to rapidly investigate any alerts to assess
whether the activity represents a data loss risk. - Response:
Our strong partnerships with Legal and HR allow us to quickly bring them in to
execute an appropriate response to an identified risk. This also means we’re
not left being the bad guys; our staff see us as the brand-value and idea
protectors instead of the police.
How Cross-Functional
Support Makes Our Security Team Smarter
It wasn’t as hard as you’d think it would be (or I thought
it would be) to get to the point that we are at today with our data loss
protection program. But it really all started with the security team building
partnerships with our line-of-business (LOB) leaders. They helped us identify:
- Our most valuable and vulnerable files and
data: Our semi-conductor designs, our manufacturing CAD drawings, our marketing
plans, our customer lists, etc. - What normal vs. abnormal file movement
looks like: If someone from marketing is using a USB to transfer data,
that’s not that unusual — it’s common for collaborative marketing projects. But
if an engineer is removing design files or an executive is taking customer
lists, it might be risky. We have different alert profiles set up based on the
type of employee, because we recognize that “normal” looks different for
different types of employees. - What action is required: Just as
different files constitute different kinds of risk, different risks require
different kinds of action. We worked with our LOB leaders to identify what
corrective actions should be taken to protect files and prevent damage when a
departing employee attempts to take data with them.
Once we had these things figured out, we worked to develop
protocols where possible. This standardized our definition of what risk looks
like when an employee is leaving — and defines what action should be taken
based on the identified risk.
Focusing on Data —
Not People
Like all security teams, we’re trying to focus on our
biggest risks. But it’s the data — not the people — that we’re watching. Thanks
to our LOB partnerships, we know what our most vulnerable and valuable data is.
Thanks to Code42, we know where this data lives and we can see how it moves.
When we detect that something’s unusual, we have the forensic depth to look
closely at files that we detect as having left — so we know immediately if it’s
something we need to address.
Moreover, by first narrowing our scope to focus on departing
employees, we can more fully leverage this broad and deep file visibility to
efficiently and effectively protect our data. And because we have this
streamlined process in place, we are able to expand our team’s focus to monitor
data in other potentially high-risk situations. We’re able to look more closely
— while simultaneously being smarter and more efficient about how we spend our
time.
A Rapid Learning
Curve
I’ve mentioned that we run a lean security operation. In
fact, we only recently added the third member of our security team, hiring a
security analyst to help our director of IT security and me in better
protecting the company. Our new security analyst came in with very little
experience using enterprise data security tools, but he was able to jump in and
begin using Code42 almost immediately. He’s taken a very hands-on role in using
Code42 to actively protect our data, and it’s expanded what we can do
— our capabilities, our use cases, etc. — as a security team.
This experience stands in stark contrast to most legacy data
security tools, which are complex, require weeks of training — and years to
become really proficient. Using these complex tools is no problem for more
seasoned security pros. But most of us are familiar with the increasing
shortage of security people — even as data security becomes more high-profile
and demand rises. This was a popular
topic at Black Hat USA 2019, and the consensus is that we need tools that
don’t require extensive training and allow even rookie security analysts to hit
the ground running.
Giving Us Confidence
to Protect Our Business
Code42 has already proven its value in myriad ways, and our process
for monitoring departing employees has already helped us catch risky data
movement and take action. Because of successes like these, HR and Legal
understand and appreciate the capabilities our security team has — and this
fosters a deeper collaborative partnership as we tackle other data security
challenges in our organization. Code42 is giving us the confidence to
proactively protect our valuable files and data across our global environment,
and to take rapid action to protect our business.
