I am already sick of it. That particular way that people’s faces look on webcasts is just not flattering. That said, that’s just one of the challenges we face (pun slightly intended) right now. Every day more employees are working from home. To get our jobs done and keep the business moving forward, we are turning to collaboration tools. Our days are filled with sharing files, Slacking colleagues and saving work to Google Drive. What does this mean for your security teams? Suddenly, they’re on the hook to manage a spike in file activity that now lives off network. The cherry on this particular sundae is, most of their tools (VPN, web proxies, etc.) aren’t architected to solve this problem at scale.
That’s why we developed a new way to see places where your data may be being put at risk without slowing down your employees. The functionality is not complicated. It’s easy to deploy. And if you’re one of our customers, you actually have it already. For more information, check out this short video or skip past the break:
Spot high-risk users
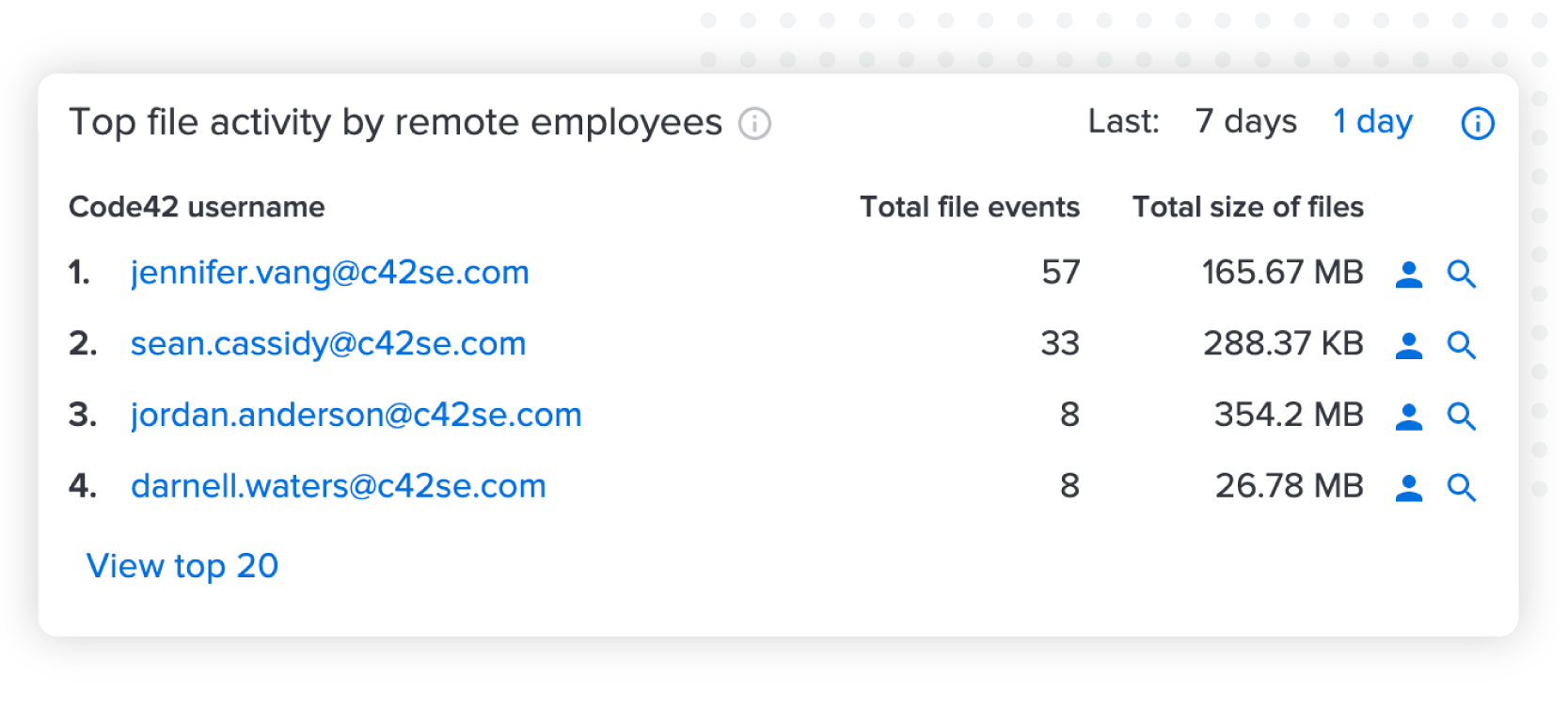
With our new functionality, the risk intelligence around your remote workforce’s file activity is surfaced alongside existing data on our risk exposure dashboard. From the interface, you get a view into company-wide file activity across computers, cloud and email — including a specific focus on file activity for employees who are working remotely. In fact, you can pinpoint which workers are most actively moving data and may represent the highest level of risk to your organization. You also can quickly investigate file events, including file content, through our forensic search interface or see a view of the users’ individual activity by accessing their user profile. For example, below we see a sorted list of the employees with the most remote file activity. The ranking makes it easy for your team to decide where to dig deeper.
Detect off-network file exfiltration
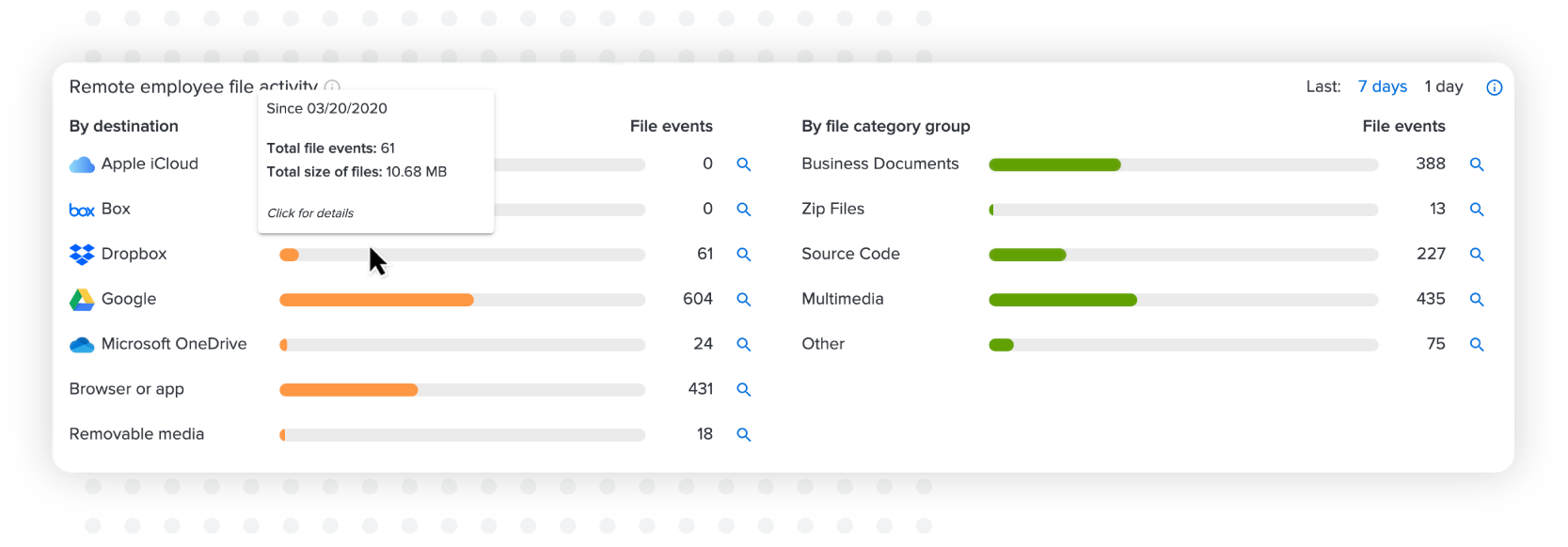
To focus in on the data itself, the risk exposure dashboard also shows file movement to the most common exfiltration vectors. This includes cloud sync activity, web browser uploads and movement to removable media, broken down by file category across your organization. With this level of detail, you can not only detect off-network exfiltration events but also validate proper use of corporate tools, and uncover Shadow IT that might indicate gaps in tools or training.
Don’t believe it? See it for yourself.
To really appreciate how quickly and easily the dashboard digs into off-network file activity, we think seeing is believing, so we’re offering a free product trial for 60 days to anyone who can use it during this time. Get more details about our 30-day free trial, including terms and conditions, here: https://code42.com/trial.
Now that we’ve covered all that, if you’re still reading this, congratulations. You’re now my new best friend. Talk soon!
