It’s never been harder to stop data from leaking. To start, every employee has a portal to send files anywhere on the internet. It’s called a web browser. Add to this the complexity of employees working both on and off the corporate network, and security teams are up against real visibility challenges.
Incydr is the purpose-built solution to manage Insider Risk. It enables security teams to detect and respond to data exfiltration and exposure in a way that’s rooted in simplicity, signal and speed. Incydr monitors for data risk across a variety of vectors–including web browsers.
How Incydr’s browser upload detection works:
Incydr detects browser upload activity via an endpoint agent that’s registered with the operating system. This allows it to detect risky activity wherever the endpoint is located, no matter the network. There are no proxies or SSL inspections to configure or maintain. Our browser technology doesn’t rely on KEXT, browser plugins, extensions, or technology that requires specific browsers, updates or software versions. With the “evergreen” browsers in today’s world, we don’t have to pin versions or deal with bluescreens/errors arising from tech incompatibilities.
Incydr’s detection spans operating systems and browser types
Incydr detects browser uploads on both Mac and Windows devices, across a variety of browsers such as:
- Internet Explorer
- Chrome
- Firefox
- Safari
- Edge
- Chromium
- Opera
Incydr’s destination categories provide security with a quick assessment of where files are going
Incydr groups browser activity into destination categories. This provides security teams with at-a-glance understanding of where files are moving without having to investigate full event details.
Example destination categories include:
Watch a product demo: See how Incydr can help you detect and respond when data is put at risk
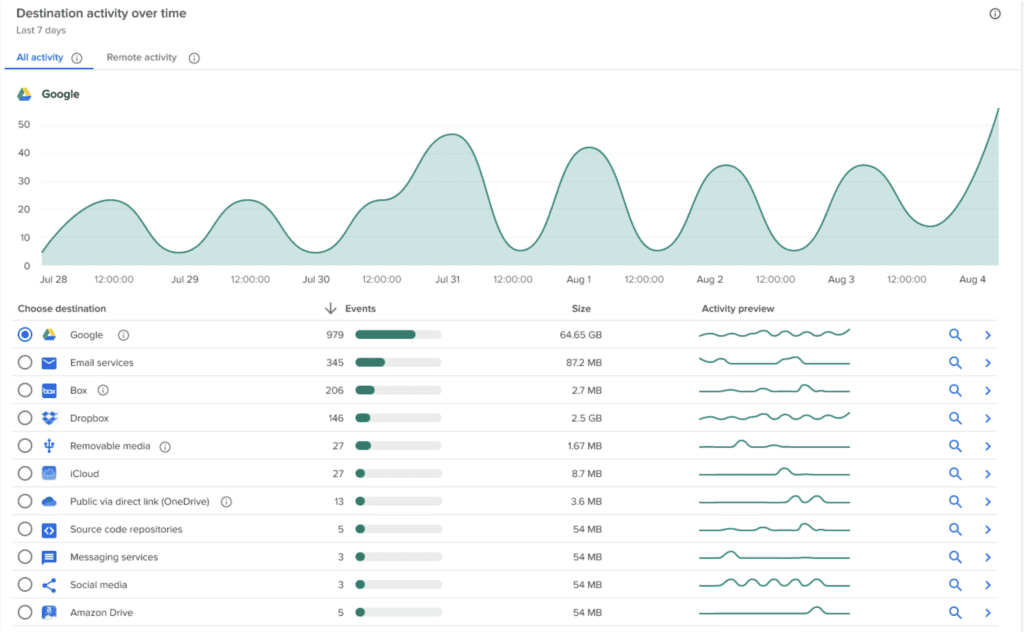
Risky upload activity is displayed at a company-wide and per-user level
The Risk Exposure Dashboard allows security administrators to see file upload risks and most common destinations across the entire company. Visualizations on user profiles provide a comprehensive understanding of a single user’s risky file activity across all vectors.
Trusted domain settings allow Incydr to surface only personal and untrusted file events
Incydr is all about delivering signal, not noise. Employees have many legitimate reasons to perform web uploads while they go about their job duties. Incydr surfaces when files are uploaded to domains and URLs that are not considered trusted. Security users establish the trusted domains for their company. Doing so allows Incydr to better identify data exposure risk and prevents file activity on domains you trust from appearing in alerts and dashboards.
Detailed event context speeds investigation
Incydr provides detailed information on browsers event. Here’s an example of the detail you’d see on a file upload to GitHub via browser:
- The destination category (example: source code repository)
- The destination name (example: GitHub)
- The application used: (example: Chrome)
- The active tab title and URL: (example: Title: Upload files JenVang/longfellow-ent – Google Chrome, URL: https://github.com/JenVanampg/longfellow-ent/upload/master
This is in addition to other detailed user, file and device information available attached to the event. Incydr also provides authorized security users with the file uploaded. This speeds security investigation and response by allowing administrators to review the actual file contents to assess risk.
